Anti-Malware , Fraud , Technology
250 Million Infections of Click-Fraud Malware Tied to Digital Marketing Agency Digital marketing agency Rafotech advertised its ability to reach 300 million users worldwide. (Source: Rafotech website, via Check Point)
Digital marketing agency Rafotech advertised its ability to reach 300 million users worldwide. (Source: Rafotech website, via Check Point)Police in Beijing have arrested 11 individuals on charges that they developed and distributed Fireball, malicious adware that was tied to 250 million installations worldwide, according to Chinese media reports.
See Also: How to Scale Your Vendor Risk Management Program
All of the suspects work for Beijing-based Rafotech, which bills itself as being a digital marketing agency. The firm's president, technical director and operations director were among those detained, Chongqing Morning News reported Tuesday. Police told the publication that Rafotech earned 80 million yuan - nearly $11.8 million - in 2016 profits.
Rafotech could not be reached for comment. The company's website remains offline following a June 1 blog post from Israel-based security firm Check Point accusing the firm of not only distributing adware, but also installing browser-hijacking malware on users' systems that could be used to "drive victims to malicious sites, spy on them and conduct successful malware dropping," for the apparent purpose of perpetrating click fraud.
Check Point warned that unlike many types of adware, which pushes advertisements to PCs, typically via banners or pop-up advertising, Fireball was designed to give its authors complete control of any system on which it had been installed. As a result, any data stored on a system infected by the malware - including "banking and credit card credentials, medical files, patents and business plans" - would be at risk of being exfiltrated by the malware controllers, Check Point says.
Nine of the Rafotech suspects will face charges of "sabotaging computer systems," state-owned media outlet Sixth Tone reports, noting that the individuals were detained soon after the Check Point blog post appeared, although news of the arrests only recently emerged.
While a majority of the firm's alleged attacks involved foreign targets, they could still face jail time in China, criminal attorney Ding Dalong tells Sixth Tone. "As long as they are engaged in illegal activity on Chinese soil, they'll be held accountable according to Chinese law - which in their case should amount to at least five years in prison," he said.
The case remains under investigation, Beijing Youth Daily reports.
Hardest Hit: India, Brazil
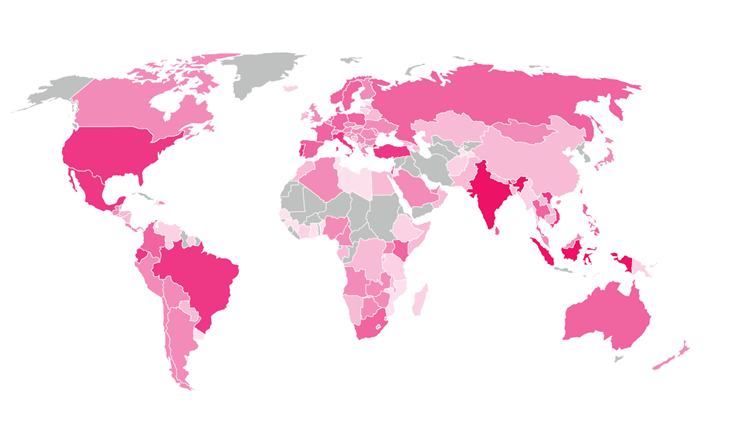 Fireball global infection rates; darker pink means more infections. (Source: Check Point)
Fireball global infection rates; darker pink means more infections. (Source: Check Point)By Check Point's count, more than 250 million PCs worldwide, and an estimated 20 percent of all corporate networks, were infected with Fireball. The security firm says it's counted 25 million infections in India (10 percent of total), 24 million in Brazil (10 percent), 16 million in Mexico (6 percent), 13 million in Indonesia (5 percent) and 6 million infections (2 percent) in the United States.
The adware has been spread in part via "Rafotech's fake search engines," Check Point says. Based on the Alexa list of the world's most-trafficked websites, 14 of these search engines regularly rank in the list of the 10,000 most-visited websites, "with some of them occasionally reaching the top 1,000," the security firm says.
"Although Rafotech doesn't admit it produces browser-hijackers and fake search engines, it does - proudly - declare itself a successful marketing agency, reaching 300 million users worldwide - coincidentally similar to our number of estimated infections," Check Point says.
Fireball adware appears to also have been distributed via Rafotech's own Deal Wifi and Mustang Browser applications, as well as via adware called ELEX, developed by a Beijing-based firm of the same name that may be connected to Rafotech's operations, according to Check Point.
Most often, however, Fireball appears to have been bundled with other software, including the P2P client QQBrowser, RSS reader BiksQRSS, and applications called Soso Desktop and FVP Imageviewer, among many others.
Such software often gets distributed via "disreputable, third-party or otherwise sketchy" websites, researchers at the security firm Cylance say in a blog post, warning users to beware downloading anything from such sites.
The firm adds that Rafotech also works with other advertising networks, including PropellerAds and Dealply. "It is possible that bundles from any of these networks currently contains Fireball," it says.
 Advertising networks used by Rafotech. (Source: Cylance, via Rafotech website)
Advertising networks used by Rafotech. (Source: Cylance, via Rafotech website)Adware Leads to Malware
Security researchers say the adware component of Fireball is just that - adware - and is easy to remove.
Initial installations of this adware may not have resulted in PCs being immediately compromised, Check Point says. "It's important to remember that when a user installs freeware, additional malware isn't necessarily dropped at the same time," it notes. "If you download a suspicious freeware and nothing happens on the spot, it doesn't necessarily mean that something isn't happening behind the scenes."
In the case of Fireball, additional installed software often included malicious capabilities, security researchers say.
"The real issue is any of the several browser hijackers installed by this bundle," Cylance says. "Taking the form of a DLL turned into a service, these payloads all install common persistence mechanisms and even clean up after themselves." Within Windows, these services are often referred to as WinArcher/D_Box, WinSAP, iThemes, WinSnare, and MiliMili/IMO, it says, while the anti-virus industry general refers to them collectively as ELEX adware.
The browser hijackers can change a browser's homepage as well as redirect browser traffic, allowing the controller to perpetrate click fraud - generating fake page views and clicks - Check Point says, adding that the malware also includes "detailed logging capability." Many Fireball samples the security firm studied also include the ability to communicate with various command-and-control networks - aka C&C or C2 networks - mostly hosted on Amazon content delivery networks. "This ensures that the C2 and desired files will be available [on a] large scale," it says.
No Free Lunch
For users, Fireball should serve as a reminder that freeware may lead to malware. "As with everything in the internet, remember that there are no free lunches," Check Point notes.
 A fake search engine run by Rafotech called trotux.com. (Source: Check Point)
A fake search engine run by Rafotech called trotux.com. (Source: Check Point)Adware can be lucrative for its distributors. And security firms have long urged users to be wary of adware, whatever its promises. "Adware is the name given to programs that are designed to display advertisements on your computer, redirect your search requests to advertising websites and collect marketing-type data about you - for example, the types of websites that you visit - so that customized adverts can be displayed," according to anti-virus firm Kaspersky Lab.
While some types of adware are legitimate - notwithstanding their sometimes ethically questionable business models - it can be difficult for users to tell, technologically speaking, when adware starts to act more like malware.
Adware has long lived in gray territory for many anti-virus firms. To be considered adware, the software must be downloaded and installed by users who accept its end-user license agreement. Legitimate adware also notifies users about what types of information it collects. If it doesn't, then it's typically classified as a Trojan application or spyware, Kaspersky Lab notes.
Sometimes, adware can make systems more vulnerable to attackers. That was the case with Superfish Visual Discovery adware that Lenovo preinstalled on its PCs until 2015. Security researchers discovered that the root certificate installed by the adware could be abused by anyone else connected to the same network to eavesdrop on users (see Lenovo Hits 'Kill Switch' on Adware).

