Anti-Malware , Encryption , Technology
FBI to Ransomware Victims: Please Come Forward Bureau Says Reporting Crime Drives Intelligence, Disruption, Arrests
Have you been the target or victim of ransomware-wielding attackers? If so, your government needs you to come forward.
See Also: Disrupt Attack Campaigns with Network Traffic Security Analytics
So says the FBI in a new public service announcement aimed at both individuals and businesses. The FBI says the effort is designed to get "victims to report ransomware incidents to federal law enforcement to help us gain a more comprehensive view of the current threat and its impact on U.S. victims."
The bureau says that while anecdotal reports of crypto-locking attacks abound, it needs more precise information about attackers - ranging from the ransomware variant to the attacker's bitcoin address - to help it pursue, disrupt and potentially arrest suspects.
"While ransomware infection statistics are often highlighted in the media and by computer security companies, it has been challenging for the FBI to ascertain the true number of ransomware victims as many infections go unreported to law enforcement," the FBI's alert says.
Why Report?
The bureau has previously asked victims of everything from tech support scams to CEO fraud to come forward in efforts that parallel outreach by European law enforcement and security experts.
Security experts say that even if law enforcement agencies cannot act on every criminal report they receive, having victims come forward serves several essential purposes:
Intelligence: Reporting crime gives law enforcement agencies a more accurate picture of attackers' techniques so that they can attempt to track and ultimately disrupt them. Funding: Crime reports also help law enforcement agencies gauge the scale of the problem so they can devote sufficient resources as well as secure needed funding from legislators or other policymakers. Arrests: Amassing intelligence on cybercrime gangs helps investigators better correlate gangs' activities, thus potentially helping them unmask and pursue the individuals involved as their attacks generate more clues. The FBI has previously noted that "much of the infrastructure being used by cybercriminals is hosted overseas," and that it often works with international law enforcement agencies.FBI Seeks 9 Data Points
The FBI is asking anyone who's been the victim of a ransomware infection to file a report with the local FBI field office or via the website of the Internet Crime Complaint Center, or IC3. That's a joint partnership between the FBI, the National White Collar Crime Center and the Bureau of Justice Assistance, which was set up to receive and investigate internet-related crime complaints.
Here's the precise information being sought by the bureau:
Date of infection; Ransomware variant, as identified on the ransom page or by the encrypted file extension; Victim company information - industry type, business size; How the infection occurred - link in email, browsing the internet, etc.; Requested ransom amount Attacker's bitcoin wallet address - often listed on the ransom page; Ransom amount paid, if any; Overall losses associated with a ransomware infection, including the ransom amount; Victim impact statement.Please Don't Pay
In its public service request, the FBI again urges anyone who's suffered a ransomware infection to never pay ransoms because it helps criminals refine their attacks and snare even more victims.
"Paying a ransom does not guarantee the victim will regain access to their data; in fact, some individuals or organizations are never provided with decryption keys after paying a ransom," the FBI says. "Paying a ransom emboldens the adversary to target other victims for profit, and could provide incentive for other criminals to engage in similar illicit activities for financial gain."
The FBI also notes that business realities may, of course, influence some organizations to pay the ransom. "While the FBI does not support paying a ransom, it recognizes executives, when faced with inoperability issues, will evaluate all options to protect their shareholders, employees and customers."
Legal experts say there appears to be no way for U.S. law enforcement agencies to prosecute anyone who pays a ransom, even if the money ends up in the hands of an individual or organization on the U.S. Treasury Department's sanctions list, provided victims employ an intermediary. I've been told that some organizations are setting up such plans as well as stockpiling bitcoins in the event that they do fall victim to a related attack.
Anti-Ransomware Portal Offers Help
Some victims, however, can get the equivalent of a "get out of jail for free" card, thanks to ongoing efforts by security researchers to crack attackers' weak crypto or otherwise exploit code-level flaws in attack code.
 Photo: Mark Strozier (Flickr/CC)
Photo: Mark Strozier (Flickr/CC)One related effort, the public/private No More Ransomware portal, says that since launching in July, it's enabled 822 CoinVault and 941 Shade ransomware victims to decrypt their data for free.
While that's good news, as the FBI noted earlier this year in an intelligence memo, don't count on decryptors always being available, because they rely on attackers making coding errors.
"Since the most sophisticated ransomware variants are practically impossible to defeat without obtaining the actor's own private decryption keys, the FBI has focused on performing significant outreach to educate the public on ransomware and the importance of keeping backups and maintaining a level of operational security when using a computer," the FBI's memo states.


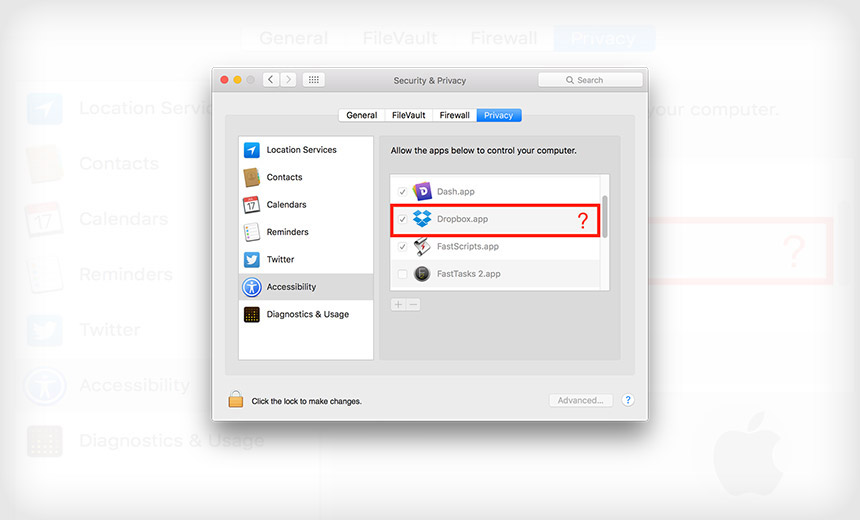 Mystery: Why doesn't Dropbox want to leave Apple's accessibility menu?
Mystery: Why doesn't Dropbox want to leave Apple's accessibility menu?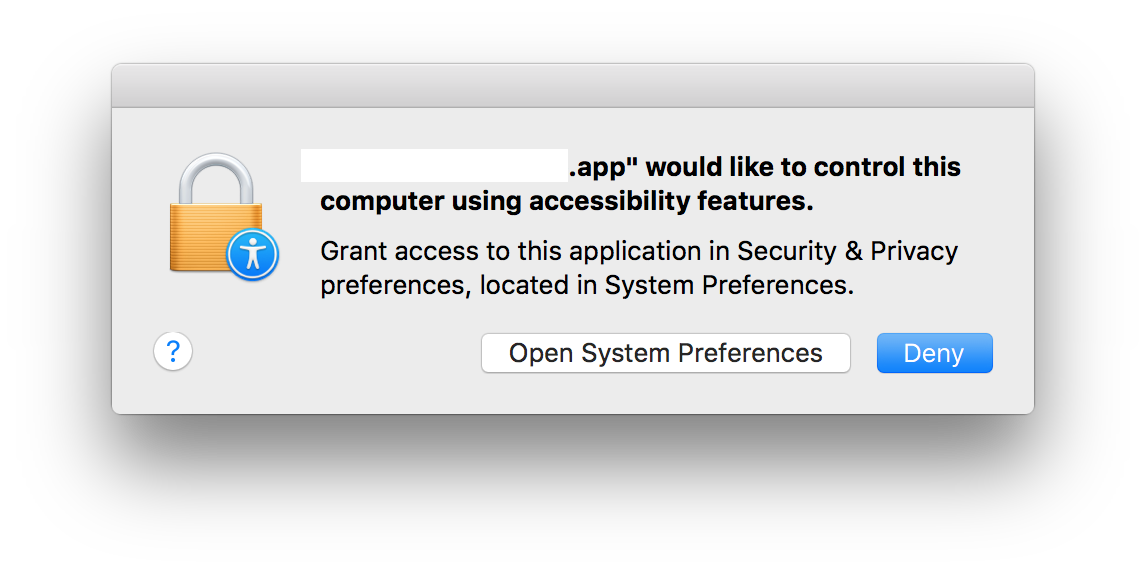 The app doesn't ask a user for permission to access the Mac OS X Accessibility menu. (Source: Paul Stokes)
The app doesn't ask a user for permission to access the Mac OS X Accessibility menu. (Source: Paul Stokes) Photo:
Photo:  Photo:
Photo:  Commerce Secretary Penny Pritzker (Photo: Department of Commerce)
Commerce Secretary Penny Pritzker (Photo: Department of Commerce) How Has Enterprise Mobility Forever Changed the Way Your Enterprise Conducts - and Secures - Business?
Only 34 percent of surveyed security leaders say they have high confidence in their organization's ability to detect and prevent fraud before it results in serious business impact. Among the reasons why they lack confidence:
Today's fraud schemes are too sophisticated and evolve too quickly (56 percent of respondents)
Customers and/or partners lack sufficient awareness to protect themselves from socially-engineered schemes (56 percent)
Employees lack that same awareness (52 percent)
These are among the results of the 2016 Faces of Fraud Survey, sponsored by SAS and focused on The Analytics Approach to Fraud Prevention. Attend this session to learn:
The top forms of fraud afflicting financial and government organizations in 2016
Biggest gaps in organizations' efforts to detect and prevent fraud
How organizations are leveraging new data analytics tools to improve their abilities to spot and then stop today's top scams
ISMG has conducted the Faces of Fraud Survey for seven years now, but this is the first time under SAS sponsorship and with a focus on - as the title says - the Analytics Approach to Fraud Prevention.
Some statistics that jump out from this study:
67 percent of respondents say it takes one day or more to uncover a fraud incident once it occurs
56 percent say customers and/or partners lack sufficient awareness to protect themselves from socially-engineered schemes
54 percent are not currently deploying advanced data analytics tools
Encouraging news from the survey results? Forty-six percent of respondents say they actively deploy advanced data analytics to monitor transaction/program activity and predict the likelihood of fraud.
But there is also concerning news: Forty-two percent say they lack the staff expertise to successfully deploy advanced data analytics tools; and 45 percent say their current systems allow for only limited analytics.
Register for this session for a detailed look at the forms of fraud afflicting financial and government organizations; their current security controls - and gaps; and where they plan their biggest anti-fraud investments for 2017.
You might also be interested in …
How Has Enterprise Mobility Forever Changed the Way Your Enterprise Conducts - and Secures - Business?
Only 34 percent of surveyed security leaders say they have high confidence in their organization's ability to detect and prevent fraud before it results in serious business impact. Among the reasons why they lack confidence:
Today's fraud schemes are too sophisticated and evolve too quickly (56 percent of respondents)
Customers and/or partners lack sufficient awareness to protect themselves from socially-engineered schemes (56 percent)
Employees lack that same awareness (52 percent)
These are among the results of the 2016 Faces of Fraud Survey, sponsored by SAS and focused on The Analytics Approach to Fraud Prevention. Attend this session to learn:
The top forms of fraud afflicting financial and government organizations in 2016
Biggest gaps in organizations' efforts to detect and prevent fraud
How organizations are leveraging new data analytics tools to improve their abilities to spot and then stop today's top scams
ISMG has conducted the Faces of Fraud Survey for seven years now, but this is the first time under SAS sponsorship and with a focus on - as the title says - the Analytics Approach to Fraud Prevention.
Some statistics that jump out from this study:
67 percent of respondents say it takes one day or more to uncover a fraud incident once it occurs
56 percent say customers and/or partners lack sufficient awareness to protect themselves from socially-engineered schemes
54 percent are not currently deploying advanced data analytics tools
Encouraging news from the survey results? Forty-six percent of respondents say they actively deploy advanced data analytics to monitor transaction/program activity and predict the likelihood of fraud.
But there is also concerning news: Forty-two percent say they lack the staff expertise to successfully deploy advanced data analytics tools; and 45 percent say their current systems allow for only limited analytics.
Register for this session for a detailed look at the forms of fraud afflicting financial and government organizations; their current security controls - and gaps; and where they plan their biggest anti-fraud investments for 2017.
You might also be interested in …







 Photo of Facebook's Mark Zuckerberg shows laptop Webcam covered with tape.
Photo of Facebook's Mark Zuckerberg shows laptop Webcam covered with tape.