Anti-Malware
,
DDoS
,
Technology
Mirai Malware Drove Record-Breaking DDoS Attack
Mathew J. Schwartz (euroinfosec) •
October 27, 2016
Mirai botnet herders use malware-infected IoT components to unleash DDoS attacks.
The malware-infected internet of things army that disrupted domain name server provider Dyn was composed of, at most, 100,000 devices.
See Also: Main Cyber Attack Destinations in 2016
That's the estimate from Dyn in its latest analysis of the Oct. 21 distributed denial-of-service attacks, noting that while attack traffic was massive, it's so far been unable to verify claims that the attacks peaked at 1.2 terabits per second.
Dyn's analysis has yet to be verified by external security researchers. Analysis of the attacks is complicated by the difficulty of distinguishing legitimate traffic from attack traffic.
"We saw both attack and legitimate traffic coming from millions of IPs across all geographies. It appears the malicious attacks were sourced from at least one botnet, with the retry storm providing a false indicator of a significantly larger set of endpoints than we now know it to be," says Scott Hilton, executive vice president of products for Dyn, in a blog post.
Dyn's investigation is ongoing. "We are still working on analyzing the data, but the estimate at the time of this report is up to 100,000 malicious endpoints," Hilton says. "We are able to confirm that a significant volume of attack traffic originated from Mirai-based botnets."
Full Bag of DDoS Tricks
Mirai targets dozens of different manufacturers' IoT devices and components - routers, CCTV cameras, digital video recorders and more - including items manufactured by Hangzhou Xiongmai Technology and Dahua Technology, among many others (see Mirai Aftermath: China's Xiongmai Details Webcam Recall).
But the Mirai malware is built to do much more than was seen in the assault against Dyn, based on a tear down of the malware's source code. The code was released in ready-to-compile form in September via HackForums - "a wretched hive of scum and villainy" regularly frequented by script kiddies - by a user called "Anna-senpai."
"For network layer assaults, Mirai is capable of launching GRE [generic routing encapsulation] IP and GRE ETH [Ethernet] floods, as well as SYN and ACK floods, STOMP [Simple Text Oriented Message Protocol] floods, DNS floods and UDP flood attacks," according to research published by cybersecurity and DDoS defense firm Imperva.
Retries Fueled Disruptions
Dyn's Hilton says the severity of the attack against his firm was compounded by legitimate DNS servers attempting to connect to its network, and these cascading retries contributing to further disruptions. He adds that the disruptions occurred despite some attack traffic having been scrubbed via Dyn's defense, as well as DDoS defenses employed by unnamed, upstream providers.
Some security experts say the DNS disruption was due, in part, to many Dyn customers, including PayPal, apparently not having any fallback plans if their primary DNS provider failed. Having secondary DNS providers in place is common in some industries, most notably for porn sites, and there have been signs that some of the large sites that were affected by the Dyn outage have been putting backup plans in place.
Another factor in the disruption, security experts say, were DNS amplification attacks. These remain a long-running problem. The U.S. Computer Emergency Readiness Team issued a related alert in 2013 warning that attackers could use "publicly accessible open DNS servers to flood a target system with DNS response traffic."
The US-CERT alert, revised last week, includes recommendations for free tools that can be used to scan for open resolvers so that organizations can lock them down.
Previous Attack Spotted
Imperva says that after the Mirai source code was released, it was able to look for historical Mirai-related attack activity that had targeted its network and found one such attack from August 17, which peaked at 280 gigibits per second. It said the attack was primarily launched by internet-connected CCTV cameras based in Vietnam, Brazil, the United States, China and Mexico, but added that devices based in 164 countries were seen.
Anatomy of a Mirai Botnet
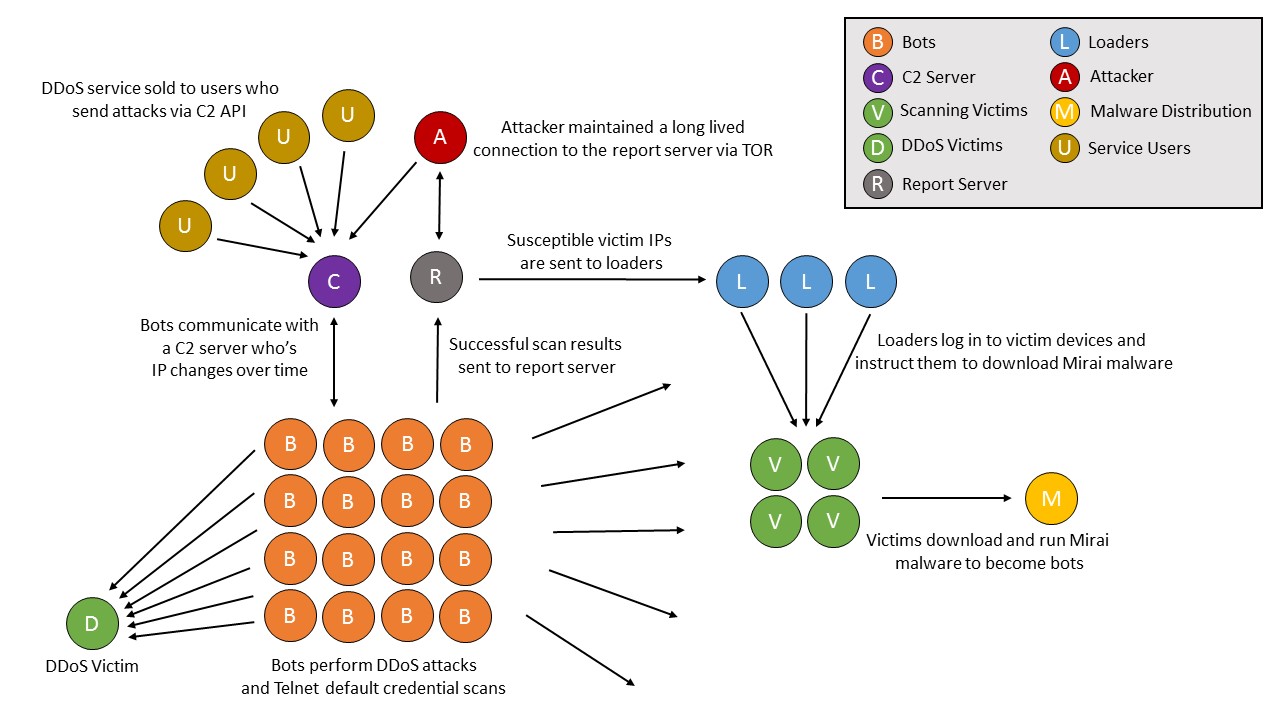
Structure of a Mirai botnet. Source: Level 3 Communications
Unanswered Questions
While more details about Mirai-driven attacks continue to come to light, it's also notable which questions have yet to be answered, especially those concerning the Dyn disruption.
"With respect to our customers and the ongoing investigation, Dyn may withhold some information," Hilton says. His company has also declined to comment on the potential identity or motive of its attackers.
U.K.-based security researcher Kevin Beaumont, who's been tracking the Mirai-launched DDoS attacks, says some crucial attack-related details have yet to be made public.
Something smells around the Dyn situation and nobody confirming the bandwidth, incl the different network providers.
But he says Dyn likely doesn't want to give would-be future attackers any details on exactly how much attack volume it can - or cannot - mitigate, as well as the resiliency of its network providers.
On the upside, however, Hilton claims that Dyn is working behind the scenes "with internet infrastructure providers to share learnings and mitigation methods" in advance of what will no doubt be future, Mirai-driven attacks.
Timeline: Mirai
Aug. 17: Imperva retroactively identifies a Mirai-powered attack against a client that peaked at 280 Gbps, involving 49,657 unique IPs located across 164 countries.
Sept. 19: OVH, a French ISP, is hit by a Mirai-powered attack that peaked at 800 Gbps, and which appeared to comprise 168,000 hacked devices.
Sept. 20:
Mirai-powered botnet hits Brian Krebs website, topping out at 665 Gbps.
Sept. 30: HackForum user "Anna-senpai" releases the Mirai source code.
Oct. 21: Record-breaking DDoS attack hits Dyn, which has so far declined to confirm the true size of the attack.


 The Federal Reserve and two other regulators published proposed cybersecurity mandates.
The Federal Reserve and two other regulators published proposed cybersecurity mandates.
 StarHub's headquarters
StarHub's headquarters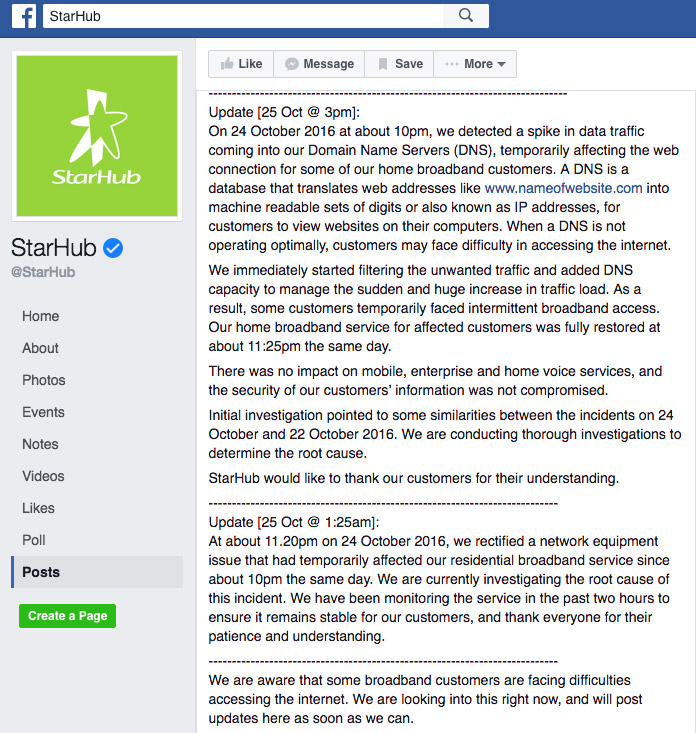 StarHub's communication to customers via Facebook.
StarHub's communication to customers via Facebook.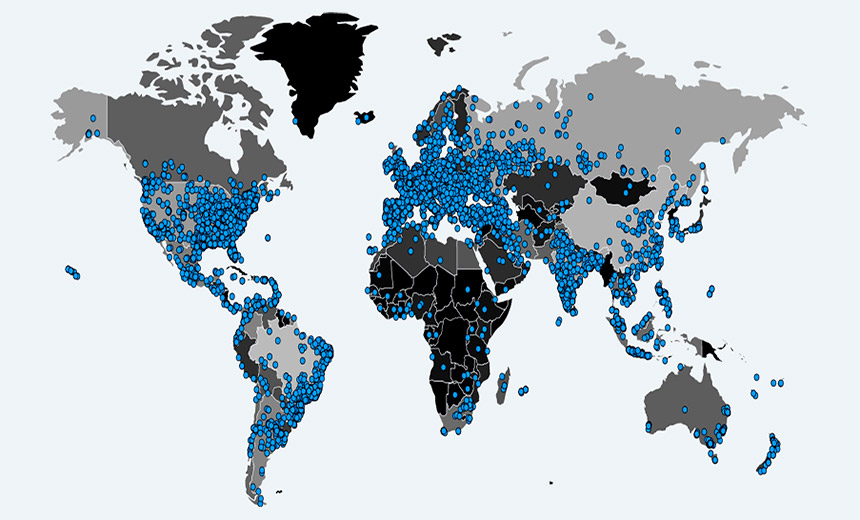 Mirai outbreak: 196,000 infected devices were seen online on Oct. 24. Source:
Mirai outbreak: 196,000 infected devices were seen online on Oct. 24. Source: 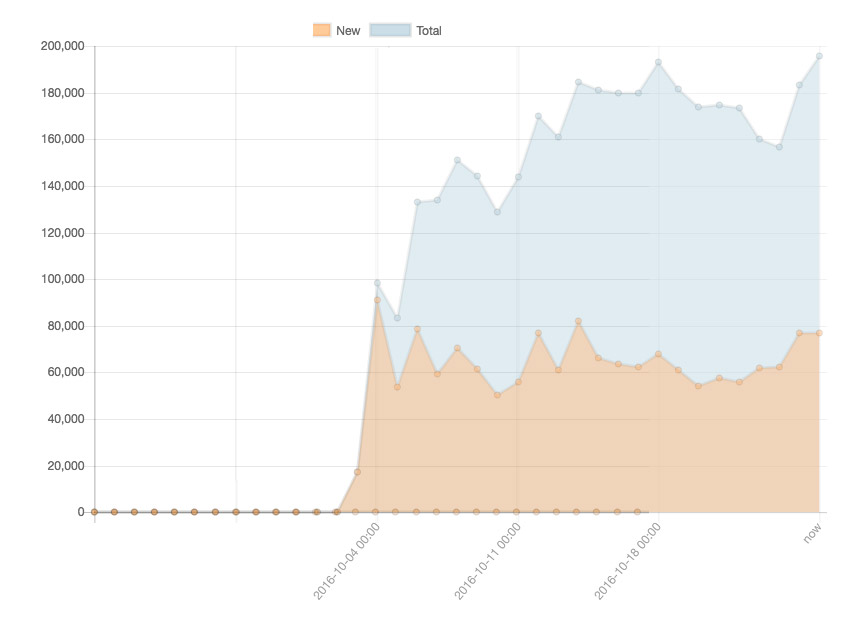 Mirai-infected devices seen online from Oct. 2 to Oct. 25. Source:
Mirai-infected devices seen online from Oct. 2 to Oct. 25. Source:  Mirai botnet herders use malware-infected IoT components to unleash DDoS attacks.
Mirai botnet herders use malware-infected IoT components to unleash DDoS attacks. Structure of a Mirai botnet. Source: Level 3 Communications
Structure of a Mirai botnet. Source: Level 3 Communications