Data Breach , Fraud , Fraud Management & Cybercrime
Fresh SS7 Fraud Highlights Ongoing Call Routing Weaknesses(jeremy_kirk) • February 5, 2019 Photo: Philafrenzy via Wikipedia/CC
Photo: Philafrenzy via Wikipedia/CCA U.K. bank says no customers lost money after cyberattackers attempted account takeovers by rerouting one-time passcodes, Motherboard reports. Such attacks involve tampering with Signaling System #7, the protocol used to route mobile phone calls worldwide.
Confirmations of such attacks are rare. But Motherboard reports that London-based Metro Bank has confirmed that the hacking attempts involved SS7, although says only an "extremely small" number of customers were affected.
SS7 is an obscure protocol that dates from the 1970s, but which remains incredibly important. Without SS7, mobile phone calls couldn't be correctly routed as people travel.
Carriers use SS7 to exchange messages between their different Home Location Registers, which contain subscriber and routing data. It's why a mobile phone can be turned on in, say, Japan, and calls and texts get correctly routed.
In the case of Metro Bank, texting was the problem, because attackers were able to intercept one-time codes sent to customers.
While two-step verification has made account takeovers more difficult, "it's not foolproof," says Alex Holden, CISO of Hold Security, a Wisconsin-based information security consultancy.
SMS Codes: End of Days
Most banks have implemented some form of two-step verification as part of their customer authentication process. Although some banks are steering away from sending one-time codes via SMS, it still remains a common practice.
Single-factor authentication - typically, a password that gets used with a customer's username or email address - leaves consumers very vulnerable to phishing attempts, in which cybercriminals try to harvest someone's login credentials through email ruses, bogus websites or malware.
If banks require a customer to also receive and enter a one-time code before being granted access, that makes attackers' life more difficult. But one-time codes are not impossible to obtain, as the Metro Bank attack demonstrates.
Security experts have been sounding the alarm over SMS, saying it should be retired as an authentication channel. In fact, advisory bodies such as NIST have warned that it should no longer be considered secure.
Over the past year, cybercriminals have succeeded in mounting attacks known as number ports or SIM swaps, where someone's number gets transferred to a new SIM in order to collect the one-time code. Those attacks often rely on fraudsters successfully social-engineering telecoms employees who can authorize account changes (see Gone in 15 Minutes: Australia's Phone Number Theft Problem).
SS7 Hack Services - on Facebook
A less prevalent way to intercept one-time codes sent via SMS involves manipulating SS7. Access to SS7 is supposed to be tightly held and restricted to mobile operators. That's also because not only can calls be diverted, but the system can reveal the exact location of a person's mobile devices, and likely, that person.
But the number of mobile operators worldwide has expanded, and the access isn't so tightly controlled. Additionally, SS7 lacks strong authentication and encryption that could help reduce the attack surface.
Four years ago, researcher Karsten Nohl highlighted weaknesses in SS7 by showing how he could eavesdrop on someone's phone calls knowing only the person's mobile number. He also highlighted risks such as tracking, denial-of-service attacks and fraud attempts that leverage SS7 access in a presentation at the Chaos Computer Club conference.
Positive Technologies, a security company, published research early last year that showed some operators don't properly validate signaling messages, making it possible for an attacker to send a fraudulent one.
Holden says there are advertisements on hacking forums by groups who purport to be able to reroute calls using SS7. On Tuesday, Holden shared a link to a hacking group that offers its services on Facebook. The Facebook group is still active.
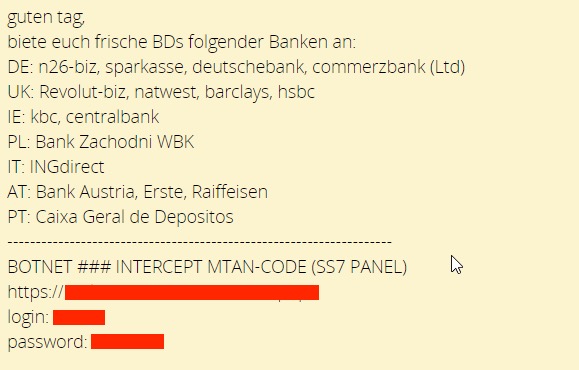 A hacking group claims to be able to manipulate SS7. (Source: Alex Holden)
A hacking group claims to be able to manipulate SS7. (Source: Alex Holden)In another advertisement in German, the same group alludes to being able to intercept mTANs, or one-time mobile transaction authentication numbers. In 2017, fraudsters reportedly used SS7 to reroute messages on devices on O2-Telefonica's network and compromise online bank accounts in Germany (see Bank Account Hackers Used SS7 to Intercept Security Codes).
The hacking group mentions several banks by name, including Barclays, ING Direct and Bank Austria. It's unclear exactly how the group gains access to SS7.

