Business Continuity/Disaster Recovery , Cybercrime , Fraud Management & Cybercrime
Dharma/CrySiS, GandCrab and Globelmposter Strains Most Prevalent, Study Finds(euroinfosec) • February 4, 2019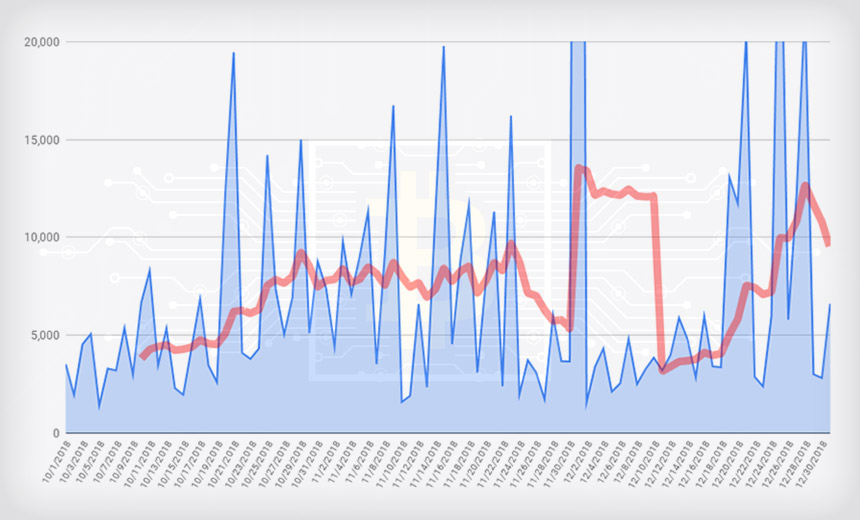 Ransom payments (mean in red): From October to December 2018, 226 victims paid an average of $6,733 for the promise of a decryption key. (Source: Coveware)
Ransom payments (mean in red): From October to December 2018, 226 victims paid an average of $6,733 for the promise of a decryption key. (Source: Coveware)Ransomware victims who opt to pay their attackes for the promise of a decryption key forked over, on average, $6,733 during the fourth quarter of 2018, up 13 percent from the previous quarter, says ransomware incident response firm Coveware.
See Also: Live Webinar: Building Secure Delivery Pipelines with Docker, Kubernetes, and Trend Micro
"The Q4 data set is derived from 226 unique ransomware attacks that were reported to, and triaged by, Coveware," CEO Bill Siegel tells Information Security Media Group. He says his firm handled negotiations for all ransoms that its customers - both individuals and organizations - chose to pay. But he cautions that not all payments resulted in victims receiving a decryption key or successfully decrypting all cryptoo-locked data.
The increase in the average ransom demand may trace to attackers more often targeting specific firms - via social engineering attacks and remote desktop protocol access - from which they demand higher ransoms, the company says in a research report (see: Stolen RDP Credentials Live On After xDedic Takedown).
Coveware also notes that at the end of last year, ransomware strains such as SamSam and Ryuk, which demand higher-than-average ransom payments, infected a greater portion of victims than before.
But those were not the most prevalent types of ransomware. Coveware says Dharma/CrySiS variants - namely the .adobe, .gamma. and .combo variants - were most common, followed by GandCrab and Globelmposter.
For victims who were able to identify the source of their ransomware infection, Coveware says 85 percent traced to RDP, 14 percent to phishing and 2 percent to another form of social engineering.
Bitcoin Preferred
By and large, ransomware attackers still prefer bitcoin. Indeed, 95 percent of all ransomware infections observed by Coveware at the end of 2018 demanded payment in bitcoin, although some have switched instead to alternatives, including dash. "While bitcoin wallets are anonymous, the transactions are trackable," the report says. "GandCrab charges 10 percent more for ransomware if paid in bitcoin versus dash, which is known for its greater anonymity."
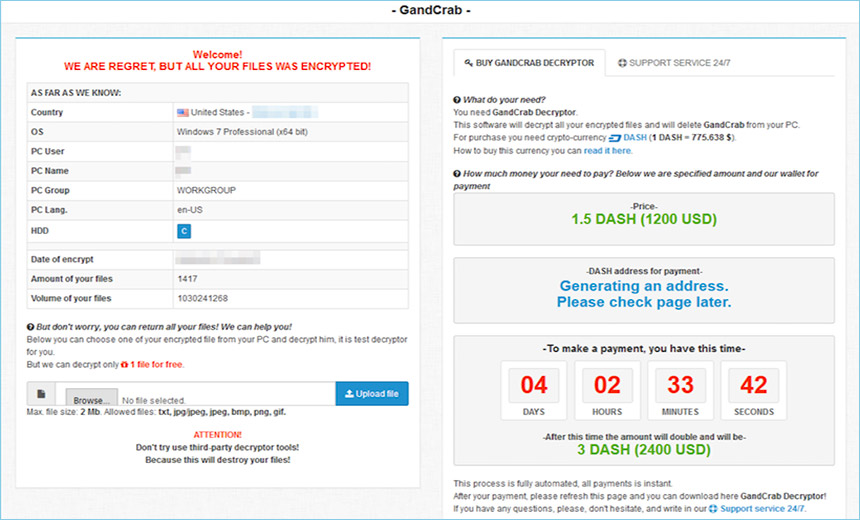 A GandCrab ransom-payment page, reachable only via a hidden TOR site (Source: Malwarebytes)
A GandCrab ransom-payment page, reachable only via a hidden TOR site (Source: Malwarebytes)Security experts and police recommend that ransomware victims never pay, warning that doing so directly funds cybercrime and further ransomware research and development. Some victims also get targeted again by the same attacker, demanding yet more payoffs (see: Please Don't Pay Ransoms, FBI Urges).
When victims do pay - in exchange for the promise of a decryption key - they also face the risk that their attacker may not honor that promise, or that technological mistakes may have already made it impossible to restore their system.
"Paying a ransom does not guarantee the victim will regain access to their data; in fact, some individuals or organizations are never provided with decryption keys after paying a ransom," the FBI has warned. "Paying a ransom emboldens the adversary to target other victims for profit, and could provide incentive for other criminals to engage in similar illicit activities for financial gain."
Decryptors: Dharma Disappoints
Of course, if too many attackers fail to give ransom payers a working decryption tool, that's a disincentive for future victims to even consider paying. But that can be small comfort to individual victims who might pay and still never see their data again.
Coveware says some ransomware outfits have a better track record than others. "For example, the GandCrab TOR site is very reliable and delivers a decryptor tool if you pay," it says. "However, some variants of Dharma can be much riskier depending on the variant and individual distributor."
When attackers do furnish decryptors, they also have differing rates of success. "The average data recovery rate when a working tool is delivered is about 95 percent but varies dramatically depending on the type of ransomware," Coveware reports. "For example, Ryuk is low at around 60 percent, while SamSam is close to 100 percent."
Dharma ransomware .adobe and .gamma variants, meanwhile, had the lowest rate of success at restoring crypto-locked files, which it attributes to some attackers' lack of technological sophistication.
Thieves Keep Targeting Backups
Security experts have long urged all computer users to keep backups of their systems so they can be wiped and restored in the event that they suffer a crypto-locking malware attack. With up-to-date backups, victims need never have to consider paying attackers for the promise of a decryptor.
Modern ransomware often includes the ability to crypto-lock not just a system, but also any network shares - mounted or not - to which the system can connect, as well as cloud storage and servers, including application servers. So it's crucial that systems be backed up to drives or network shares that will then be completely disconnected from the system being backup up.
Coveware says that 75 percent of ransomware victims who paid a ransom from October to December 2018 had also lost their backups to the crypto-locking attack, up from 54 percent the prior quarter.
"Backup systems are typically the first target of the hacker. Next, hackers encrypt the primary file and application servers in order to completely cripple the target company," Coveware says. "Proper network partitioning and 'least privilege' administrative access are a must to avoid being compromised."

