Anti-Malware , DDoS , Technology
Can't Stop the Mirai Malware So Save Yourself, and Maybe the Rest of Us Too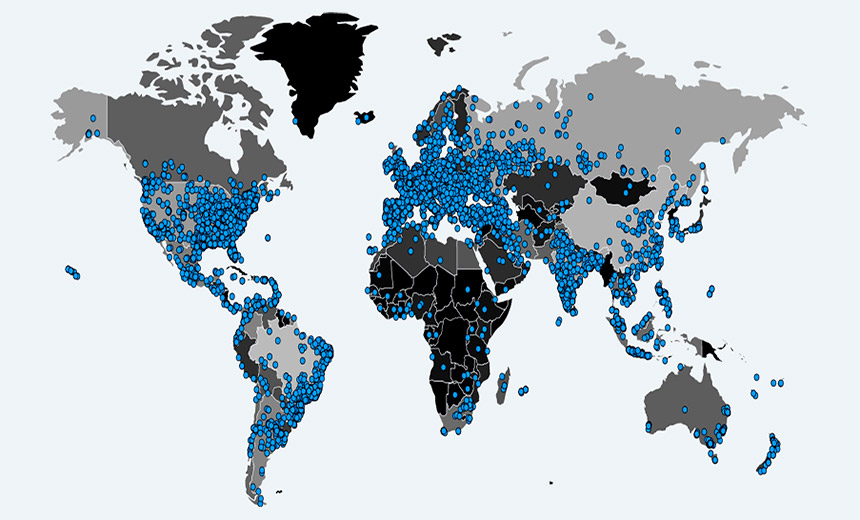 Mirai outbreak: 196,000 infected devices were seen online on Oct. 24. Source: MalwareTech
Mirai outbreak: 196,000 infected devices were seen online on Oct. 24. Source: MalwareTechInternet of things security takeaway: Save yourself. And by doing so, maybe help save the rest of us too.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
That's the obvious takeaway from the rise of low-tech, high-impact Mirai malware, which was built to exploit the default usernames and passwords used by dozens of different manufacturers' IoT devices. It's also been tied to the record-setting distributed denial-of-service attacks against domain name server provider Dyn on Oct. 21, which resulted in widespread internet outages, preventing users from reaching such leading websites as Amazon, PayPal, Spotify and Twitter.
Just as some vaccines provide a "herd effect" - indirectly protecting people at risk of a disease by ensuring there's a large population that's immunized against it - the more individuals and organizations that proactively secure their IoT devices, the better off we'll all be.
Unfortunately, it's going to be a long time - read: never - before we see the equivalent of IoT herd immunity against information security threats.
"Mirai is a huge disaster for the internet of things," Hangzhou Xiongmai Technologies spokesman Cooper Wang tells Information Security Media Group. Xiongmai is the manufacturer of some of the many different types of IoT components and circuit boards targeted by Mirai. The manufacturer promised to recall some of that technology, or at least release more secure firmware.
Meanwhile, the U.S. Department of Homeland Security says it's "working with law enforcement, the private sector and the research community to develop ways to mitigate against [Mirai] and other related malware." It plans to develop and release "a set of strategic principles for securing the internet of things ... in the coming weeks."
Both of those moves, however, require manufacturers of low-cost devices as well as the users - including millions of consumers - who rely on them to up their security game. And that's a long shot.
Far From Sophisticated
Compounding the problem: Mirai-type attacks are not complex.
"I'm not quite sure when people are going to realize that the Internet and the web are running on protocols that were never intended to be secure, and as such it's almost inevitable that these guys will find a way of attacking," University of Surrey computer science professor Alan Woodward tells me.
"It's not sophisticated, it's not clever, it's just waiting to happen," he adds.
Mirai Botnet: Unique IP Addresses Seen
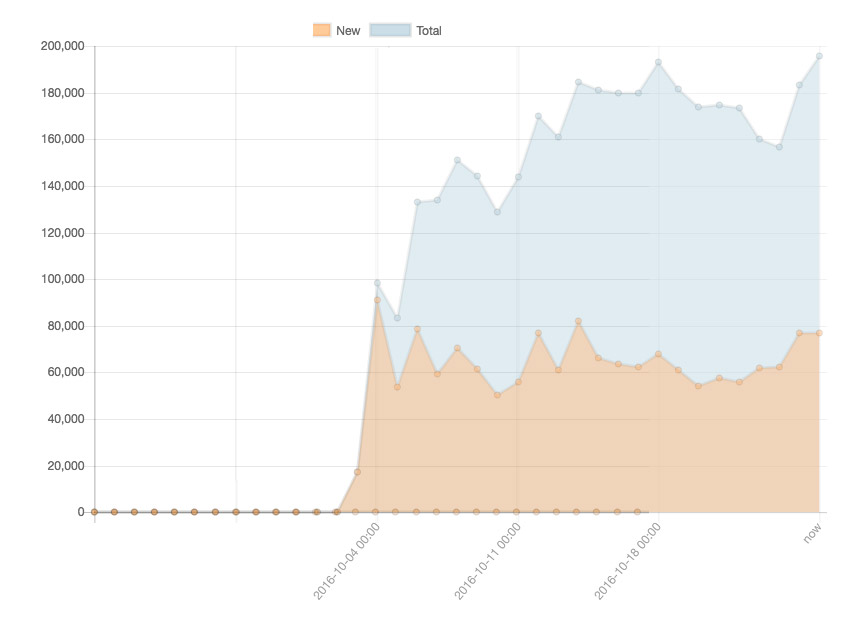 Mirai-infected devices seen online from Oct. 2 to Oct. 25. Source: MalwareTech.
Mirai-infected devices seen online from Oct. 2 to Oct. 25. Source: MalwareTech.Bet on Teenagers
Who's to blame? From an attack standpoint, there's abundant, albeit anecdotal, evidence that an individual or outfit calling itself Poodlecorp originally developed Mirai and used it to disrupt online gaming. Historically speaking, that's the M.O. of stresser/booter service providers, sometimes run by non-advanced but highly persistent teenagers.
"Mirai was once [controlled] by PoodleCorp and they even stated they would attack on the 21st [of October], specifically EA's Battlefield 1 launch day," Bryant Townsend, CEO of DDoS defense firm BackConnect, tells me. "Since their tweet about this, the Mirai source code was publicly released, which now makes it difficult to attribute the attack to any individual or organization."
October 21st #PoodleCorp will be putting @Battlefield in the oven
The Oct. 21 attacks did appear to disrupt some players of Electronic Arts' game, at least ones who were using the PlayStation Network.
Rise of the Exploiters
The ability to consistently marshal attacks of the size that targeted Dyn has implications. "What we do know is that an individual or organization has achieved hegemony over the botnet, as it would not be possible to launch an attack of this size unless they were in complete control over all of the infected IoT devices," Townsend says. "There is also the possibility of attackers using multiple botnets in addition to Mirai to increase the attack size, but we haven't seen anything to indicate this yet."
Already, rival online gangs are vying for vulnerable IoT devices, developing malware that removes rivals' botnet software from such devices. "There is a never-ending underground war for vulnerable IoT devices to be used for DDoS attacks," Townsend says. "Topple the current leader of this war, and the others will soon be fighting to claim their throne."
Design Philosophy: Battle IoT Breaches
Blocking IoT attacks isn't conceptually complex, and as the security researcher known as "SwiftOnSecurity" notes, we've solved these types of problems before.
"Assume breach" is a systems monitoring and information architecture approach, NOT a statement of the status of all electronic devices.
Xiongmai, for example, has promised to stop enabling telnet by default in its IoT components, as well as to prompt users to change default usernames and passwords, both of which have been exploited by Mirai. It's also advising users to firewall the devices and block all unnecessary ports.
Minneapolis-based IT consultant Rich Farris did just that when he found himself having to deal with internet-connected security cameras that had been infected with malware and used to launch DDoS attacks, despite his having changed their default usernames and passwords (see How an IT Pro Kicked Hackers Off Surveillance Cameras). With his customer not wanting to throw the cameras away and buy new ones, he put them behind a firewall, blocking all ports except the ones required for audio, video and to access the web-based admin panel. He then reinstalled a clean copy of the firmware.
That's one hands-on but relatively non-complex way that vulnerable IoT devices can be safeguarded, making them unavailable for malware-wielding attackers' exploitation. But realistically, how many other such IoT-using consumers or even some administrators will also be able save themselves, and by extension the rest of us?

