Anti-Malware , DDoS , Endpoint Security
But Xiongmai's Move Won't Stop Mirai-Powered Botnets, Security Experts Warn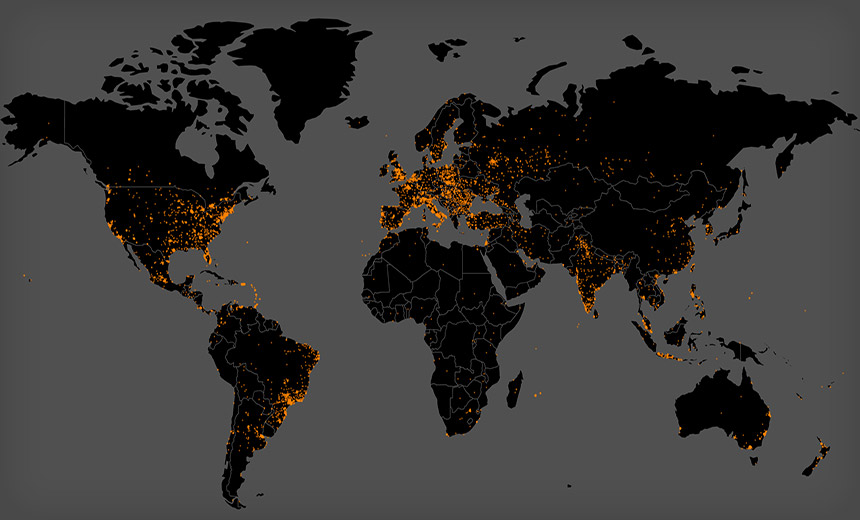 Map of Mirai-infected devices seen from Oct. 22 to 23. Credit: MalwareTech
Map of Mirai-infected devices seen from Oct. 22 to 23. Credit: MalwareTechChinese manufacturer Xiongmai Technologies has promised to recall or patch some components and circuit boards that it manufactures, which attackers compromised and used to help power a massive internet of things botnet that overwhelmed DNS provider Dyn's systems on Oct. 21 via distributed denial-of-service attacks (see Mirai Botnet Pummels Internet DNS in Unprecedented Attack).
See Also: Secrets to a Simpler Security Incident Response
Xiongmai's components and circuit boards are built into numerous white-labeled IoT goods, including CCTV and webcam devices, as well as digital video recorders that often get connected to those devices.
Many popular websites - ranging from Amazon and Spotify to Tumblr and Twitter - that used Dyn as their DNS provider were rendered temporarily unreachable on Oct. 21. The culprit was a massive DDoS attack that security intelligence firm Flashpoint says involved IoT devices infected with Mirai malware, which overwhelmed the DNS service and prevented internet users from reaching many sites. Flashpoint adds that at least some of those devices were built by - or used components from - Xiongmai, even if they were not labeled as such.
Security researchers report that tens of millions of IP addresses were used in the attack. But they add that some of those IP addresses were likely spoofed by attackers, thus making it difficult to get an accurate count of how many different infected devices, or distinct Mirai botnets, may have been involved in the attacks.
"The attack really is yet another wake-up call to website operators that DNS is vulnerable," Alan Woodward, a computer science professor at the University of Surrey, tells Information Security Media Group. "We've known it was the soft underbelly of the web for years. What is surprising is that more sites haven't taken the precaution of having secondary DNS servers with automated switchover of some kind."
Dyn: Investigation Continues
Dyn reports that its investigation into the attack continues. "We are conducting a thorough root cause and forensic analysis and will report what we know in a responsible fashion. The nature and source of the attack is under investigation, but it was a sophisticated attack across multiple attack vectors and internet locations," Kyle York, chief strategy officer for Dyn, says in a post-attack blog post. "We can confirm, with the help of analysis from Flashpoint and Akamai, that one source of the traffic for the attacks were devices infected by the Mirai botnet. We observed tens of millions of discrete IP addresses associated with the Mirai botnet that were part of the attack."
One obvious problem is that the Mirai malware is built to target default usernames and passwords used by dozens of different types of components that get built into IoT devices. "One thing all these devices should be doing - and let's face it, it's not rocket science - is forcing users to change the default credentials when it is first turned on," says Woodward, who's also a cybersecurity adviser to the EU's law enforcement intelligence agency, Europol. "Some devices seem to do the exact opposite and make it difficult. That's very poor practice."
There appear to be more than 500,000 internet-connected devices with Xiongmai components that have telnet enabled, and many still sport the manufacturer's default username and password that is respectively "root" and "xc3511," Bill Buchanan, a computer science professor at Scotland's Napier University, says in a blog post. He explains that just this one line of Mirai source code is all that's required to compromise devices for which the username and password remain unchanged:
"As these systems tend not to update themselves, an intruder can create scripts which scan for port 23 (telnet), and then try to connect with the default password," Buchanan says. "If successful, the script can then upload the malware and compromise the device. Many people running CCTV systems might have no idea that their devices are being used to launch an attack against the core of the internet."
Internet-Connected Xiongmai DVRs
 A search for internet-connected Xiongmai DVRs returned 569,214 results on Sept. 28. Source: Shodan
A search for internet-connected Xiongmai DVRs returned 569,214 results on Sept. 28. Source: ShodanXiongmai Promises Fixes
While confirming that some devices that employ its IoT technology were compromised by attackers, Xiongmai disputes suggestions that its technology was present in a majority of the infected devices and contends that all IoT manufacturers face similar challenges.
"Security issues are a problem facing all mankind," the manufacturer says in a statement provided to media outlets, confirming that some devices that include its components were compromised by Mirai malware. "Since industry giants have experienced them, Xiongmai is not afraid to experience them once, too."
Xiongmai tells Reuters that it will launch a recall of the circuit boards and components that it manufactures, which go into webcams, as well as issue firmware updates for some devices. Xiongmai told Information Security Media Group that since September 2015, it has shipped devices that have telnet disabled by default, and which prompt a user to change the default username and password as soon as they activate the device. But some security researchers have questioned those assertions, noting that recently purchased devices with Xiongmai components appear to have neither of the specified security improvements.
Recall Efficacy Unclear
Furthermore, it's not clear if Xiongmai's promised recall of U.S. devices or patched firmware might take a bite out of future botnets that are built via compromised internet of things devices.
Woodward, for example, says any potential product recall would likely be a "horses and stable doors" proposition, meaning a recall or patch is too little, too late, especially because it would only involve U.S.-based devices. Furthermore, as he notes via Twitter, it's not likely that all buyers of products that include Xiongmai components will have filled out their product registration card and could thus be reliably alerted to the product recall anyway.
U.S. security researcher Robert David Graham, who heads security firm Errata Security, says it's unclear that any more big-picture attempts to "fix" internet of things security - for example by the U.S. government imposing related regulations or requiring every device to have a unique administrator username and password - would work.
"Most of the devices are made in China" and shipped to numerous countries, not just the United States, Graham says in a blog post. "Moreover, it's unclear what 'security' means. There no real bug/vulnerability being exploited here other than default passwords - something even the U.S. government has at times refused to recognize as a security 'vulnerability.'"
Attack Teardown
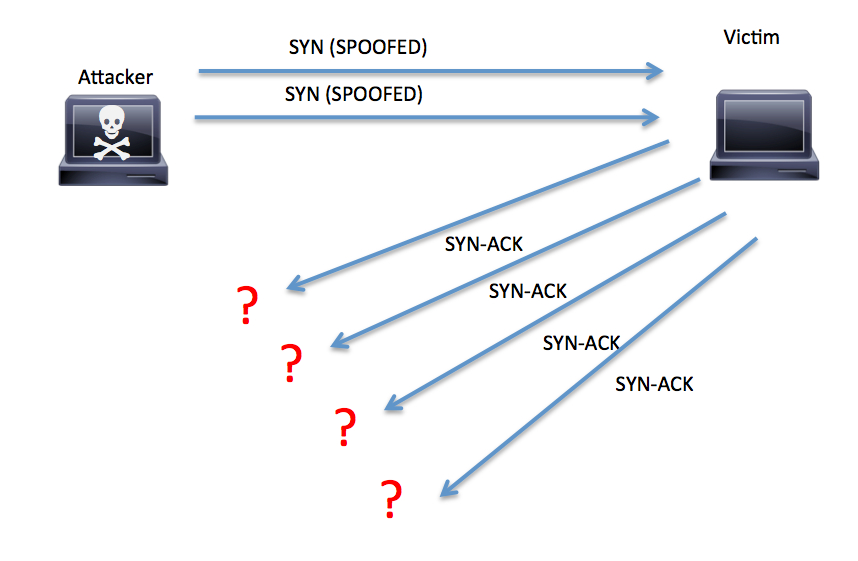 Anatomy of a SYN flood attack.Credit: Cisco
Anatomy of a SYN flood attack.Credit: CiscoMost DDoS attacks involve overwhelming targets with volumes of traffic or else overwhelming certain system resources, causing timeouts. But Napier University's Buchanan says that the attacks against Dyn were somewhat unusual, in that they used a one-two punch involving "TCP SYN floods against port 53 of the DNS servers, along with a subdomain attack."
In a typical TCP connection to a server, a client requests a synchronize, or SYN, message from a server, receives a SYN-ACK acknowledgment back from the server, then responds with an acknowledgement - ACK - and establishes a connection with the server.
In a SYN flood, however, the server gets flooded with SYN messages, each of which triggers a SYN-ACK, but the client never sends back the final ACK. The server, however, will wait to receive the acknowledgement for a preset time, and as the bogus synchronization messages build up, it becomes unable to handle legitimate SYN requests.
Subdomain Attack
Separately, the Mirai botnet also utilized a subdomain attack. Buchanan says this involves first picking a valid domain, such as mycoffeeshopboston.com, then adding an invalid subdomain name to the beginning, such as boblovescoffee.mycoffeeshopboston.com.
"The requested DNS server will not have this in their cache, and must then go to the authoritative source of the domain, which, in this case, was Dyn," Buchanan says. "This will then flood the Dyn network with requests from DNS servers asking about the non-existent domain. The only way to cope with this is to increase the bandwidth of the incoming network connections and to spin-up more servers to cope with the demand."
The widespread outages triggered on Oct. 21 show the difficulty of coping with that demand, at least initially.
Dyn reports that there were three attack waves against it on Oct. 21. The first affected DNS servers located on the East Coast of the United States and was mitigated after about two hours. The second wave, York says, "was more global in nature," and took about an hour to mitigate. Finally, Dyn reports that it later successfully repelled a third wave of attacks.
Dyn didn't immediately respond to a request for comment about what defenses it used to block the third attack wave. But York reports: "We were able to successfully mitigate it without customer impact."

