 StarHub's headquarters
StarHub's headquartersThe massive attack against U.S.-based domain name server provider Dyn isn't the only such disruption launched by internet of things devices that's been seen in recent days.
See Also: Avoid Theft of Your Privileged Credentials
Just after Dyn was targeted with distributed denial-of-service attacks that disrupted its DNS services, blocking access to major websites for many internet users, Singaporean ISP StarHub suffered two similar DNS attacks.
StarHub has blamed the attacks on malware-infected IoT devices owned by its customers.
"We are now able to confirm that we had experienced intentional and likely malicious distributed denial-of-service attacks on our domain name servers," StarHub says in a Facebook post to customers. "These two recent attacks that we experienced were unprecedented in scale, nature and complexity."
DNS services resolve domain names into internet protocol addresses, which is how machines and systems reach websites.
"This is the first time that Singapore has experienced such an attack on its telco infrastructure," Singapore's Cyber Security Agency and Infocomm Media Development Authority said in a joint statement, reports Singapore's The Straits Times.
IoT Devices Blamed
Speaking at an Oct. 26 press conference, StarHub CTO Mock Pak Lum said the company traced the attacks to infected devices - such as webcams and routers - owned by subscribers and advised consumers to only purchase the devices from reliable vendors, The Strait Times reports. He added StarHub would "soon" dispatch technicians to help customers clean any malware-infected devices (see Mirai Aftermath: China's Xiongmai Details Webcam Recall).
StarHub says the attacks against it involved a "sudden and huge increase in traffic load" on Oct. 22, the same day that the seventh annual StarHub TVB Awards aired. The awards involve viewers as well as a panel of judges voting for their favorite actors, actresses and television programs on Hong Kong's TVB station. Winners this year included actress Nancy Wu for "A Fist Within Four Walls" and actor Wayne Lai for "Short End of the Stick," among others.
StarHub said it was targeted by a second wave of attacks on Oct. 24.
"On both occasions, we mitigated the attacks by filtering unwanted traffic and increasing our DNS capacity, and restored service within two hours," StarHub says. "No impact was observed on the rest of our services, and the security of our customers' information was not compromised. We kept customers informed on these matters via our hotline and social media."
We're aware that some broadband customers are facing difficulties accessing the internet. For more information visit https://t.co/GpRC2eFWXF
Home Broadband Disrupted
StarHub says that home broadband users were affected, but not enterprise, mobile or home voice customers. So far, the ISP says it does not know who launched the attacks or what their motivation might have been. "We continue to stay vigilant against possible follow-up DDoS attempts. In addition, we are working closely with the authorities to determine intent and source of these two DDoS attacks," StarHub says.
Singapore's Cyber Security Agency and IMDA have warned other ISPs and telecommunications providers to beware of similar attacks and have also called on IoT device owners to keep their devices secure. "Given the increasing connectedness of digital systems, there is no fool-proof solution. It takes a collective effort from companies and society to bolster our cyber resilience," they said.
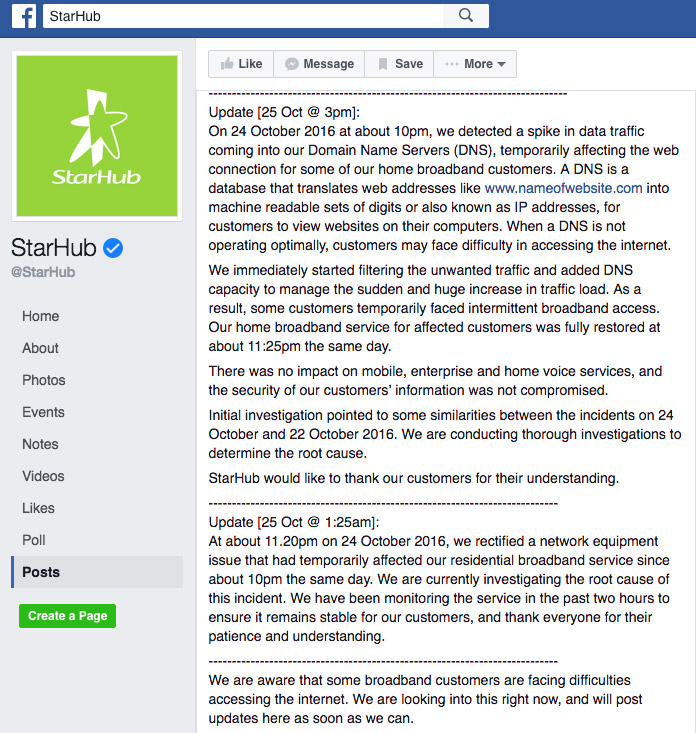 StarHub's communication to customers via Facebook.
StarHub's communication to customers via Facebook.A StarHub spokesman tells Information Security Media Group that the ISP has begun scheduling home visits for customers whose devices it's identified as being involved in the attacks. "During the home visits, our technical service officers 'HubTroopers' will conduct an onsite investigation before helping the customers secure any unsecured internet connected devices," he says. "These may include installing anti-malware software, changing default passwords, updating device software, fixing device misconfiguration and/or replacing devices."
The spokesman adds that StarHub is also encouraging all customers "to review the security settings of their internet-connected devices and disconnect any suspect device."
No Word on Malware Used
StarHub declined to comment on a request for more information about the attacks, including the type of malware that was used and whether the infected devices included any IoT devices - such as routers - supplied by the ISP to its customers.
So it's not clear if the ISP was targeted by IoT devices infected by Mirai malware, or a different type of malware, such as Bashlite - a.k.a. Lizkebab, Torlis, Gafgyt. According to telco Level 3 Communications and security intelligence firm Flashpoint, there are more than 200 separate command-and-control servers for Bashlite. Since July, the largest of those botnets was controlling 120,000 infected devices, the firms reported last month.
Dyn, meanwhile, says that its ongoing investigation into the DDoS attacks against it has found that the attack was launched by "up to 100,000" IoT devices, and that "a significant volume of attack traffic originated from Mirai-based botnets.
This story has been updated with comment from StarHub.

