Anti-Malware , DDoS , DDoS Attacks
Notorious Hack Forums Blocks Offerings, But Cybercrime Services Surge On The 19-year-old administrator of Titanium Stresser recently pleaded guilty to related computer crime charges.
The 19-year-old administrator of Titanium Stresser recently pleaded guilty to related computer crime charges.The administrators and enablers of so-called stresser/booter services may be feeling some heat.
See Also: 2016 IAM Research: Where Financial Institutions' PAM Programs Are Falling Short
Such services are often marketed as tools for stress-testing one's website by providing on-demand distributed denial-of-service attacks. But the tools have long been used by individuals who want to disrupt others' websites, and cybercrime experts say they can be a source of easy money for unscrupulous developers and administrators.
In a sign that investigators are paying more attention to disrupting stresser/booter services, the notorious Hack Forums, a site that security experts say caters especially to script kiddies and cybercrime wannabes, recently announced that it will be shutting down its Server Stress Testing forum.
"Unfortunately once again the few ruin it for the many. I am sure this is going to upset some members but also please many, some of whom aren't even members," site admin Jesse "Omniscient" LaBrocca said in an Oct. 28 post. "I'm personally disappointed that this is the path I have to take in order to protect the community. I loathe having to censor material that could be beneficial to members. But I do need to make sure that we continue to exist and given the recent events I think it's more important that the section be permanently shut down."
 Hack Forums announced Oct. 28 that it would no longer allow information relating to stresser/booter services to be posted.
Hack Forums announced Oct. 28 that it would no longer allow information relating to stresser/booter services to be posted.What is yet to be seen, however, is if the move by Hack Forums leads to any reduction in on-demand DDoS attacks (see Cybercrime-as-a-Service Economy: Stronger Than Ever).
On-demand DDoS attacks can be tough to trace, especially if service operators use infected endpoints to launch their attacks. To date, for example, it's unclear if the record-setting DDoS attacks tied to infected internet of things devices - and IoT malware such as Mirai - have been launched by stresser/booter services. But historically, cybercriminals have only infected large numbers of IoT devices to monetize their efforts by offering on-demand DDoS attacks.
Recently, however, there have been a number of arrests of alleged stresser/booter operators. In September, for example, two 18-year-old men - Itay Huri, a.k.a. "P1st" and "M30w," and Yarden Bidani, a.k.a. "AppleJ4ck" - were arrested in Israel at the FBI's request in connection with an investigation into the vDos site, which provided DDoS attacks on demand.
"Based on a subscription scheme, starting from $19.99 per month, tens of thousands of customers paid more than $600,000 over the past two years to vDos," according to a new DDoS attack trends report released by Moscow-based security firm Kaspersky Lab. "In just four months between April and July, vDos launched more than 277 million seconds of attack time, or approximately 8.81 years' worth of attack traffic," it adds.
Europol Sees DDoS Threat
The threat posed by stresser/booter services was cited in the Internet Organized Crime Assessment for 2016, published in September by the EU's law enforcement intelligence agency Europol, as one of the top cybercrime challenges that police are currently battling.
"DDoS attacks continue to grow in intensity and complexity, with many attacks blending network and application layer attacks," the IOCTA report reads. "Booters/stressers are readily available as-a-service, accounting for an increasing number of DDoS attacks." Such services are often also used to extort victims.
The problem is international in scope. Kaspersky Lab says that from July to September, the top countries hosting victims targeted by DDoS attacks were China, the United States and South Korea. It said SYN floods remain by far the most prevalent type of DDoS attack.
DDoS Attacks: Most-Targeted Countries
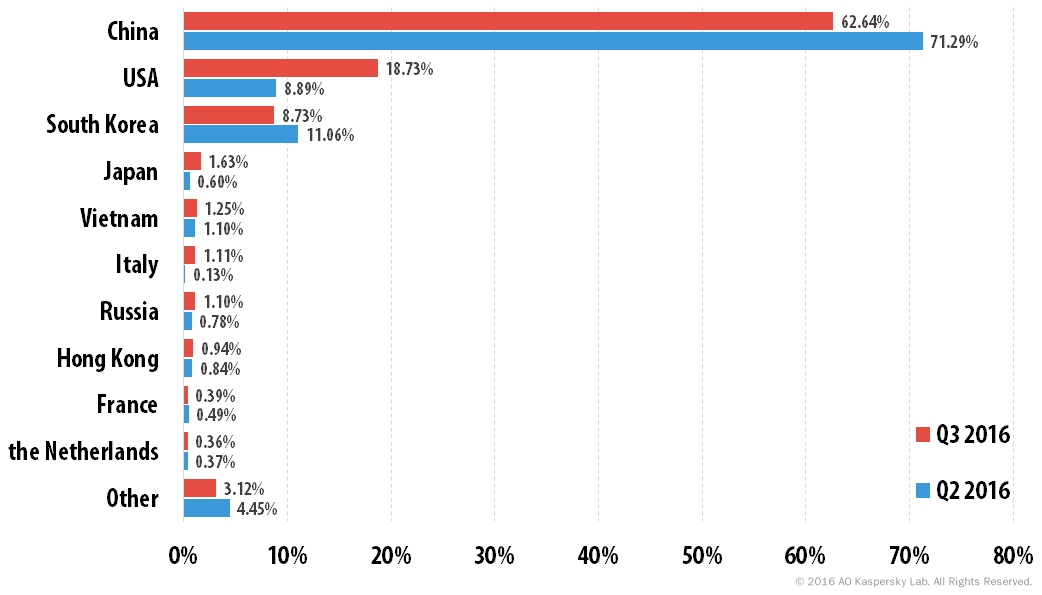 Distribution of unique DDoS attack targets by country, Q2 2016 vs. Q3 2016 (source: Kaspersky Lab).
Distribution of unique DDoS attack targets by country, Q2 2016 vs. Q3 2016 (source: Kaspersky Lab).Related Arrests Continue
But Europol says related DDoS-disruption efforts are underway. "Providers are taking more responsibility for the security and health of their own networks and services," according to the IOCTA report. In addition, "ISPs are actively detecting and filtering DDoS attacks, implementing standards such as BCP38 to reduce IP spoofing, detecting fraudulent logins and other malicious activity."
Law enforcement agencies are also continuing to investigate stresser/booter services as well as their users. But security experts say such efforts are complicated in part by the relative ease with which such services can be designed, hosted or procured, as well as the criminal profits to be made by running a stresser/booter service.
Last year, for example, as part of "Operation Vivarium" British police arrested four individuals - a 15-year-old, 16-year-old and two 18-year-olds - on suspicion of having used the Lizard Squad's Lizard Stresser DDoS-on-demand service. Police said the suspects bought attack time "using alternative payment services such as Bitcoin in a bid to remain anonymous."
Previous stresser/booter arrests - including suspected ringleaders behind the Lizard Squad group - in some cases revealed that they too were, legally speaking, only children, at least when they first designed and began selling such services.
Titanium Stresser Admin Pleads Guilty
The same is true for 19-year-old Adam Mudd in England, who ran "Titanium Stresser," a service that police say was tapped by international users to launch 1.8 million attacks over two years.
On Oct. 21, Mudd pleaded guilty at the Central Criminal Court of England and Wales in London - better known as the Old Bailey - to three related charges: two counts of computer misuse, related to creating and administrating his stressor tool; and one count of money laundering in relation to financial gains made via his stressor tool being used by others. He also admitted to attacking his old college - as a pupil studying computer science - while testing his tool.
According to England's Eastern Region Special Operations Unit, Mudd earned more than £300,000 ($365,000) before he turned 18 years old, and allege that from September 2013 until March 2015, his service was used to launch 1.8 million attacks. Prosecutors said in court that he first developed the software when he was only 15 years old, and that he used it himself 594 times against 181 individual IP addresses, employing the username "themuddfamily," Britain's Evening Standard reports, adding that the service logged every attack - and related username - that it launched.
Lizards Learned from Mudd
They also said that Mudd's software was copied by the Lizard Squad, becoming the basis for its Lizard Stresser service.
Mudd has been freed on bail - on condition of not using any internet-connected devices - until Dec. 16, when he faces sentencing, and Judge Michael Topolski indicated that he might serve time in a young offenders' institution, Evening Standard reports. It adds that Mudd's attorney, Ben Cooper, told the court that his client has been diagnosed as autistic, is currently undergoing psychological evaluation, lives with his parents and works as a hotel porter.
"Adam Mudd's case is a regrettable one, because this young man clearly has a lot of skill, but he has been utilizing that talent for personal gain at the expense of others," Detective Inspector Martin Peters, head of the Eastern Region Special Operations Unit's cybercrime team, which arrested Mudd, said in a statement issued after the suspect pleaded guilty.
"We want to make clear it is not our wish to unnecessarily criminalize young people, but want to harness those skills before they accelerate into crime," Peters added.

