Application Security , Breach Preparedness , Cybersecurity
2 Senators Say Guidelines Don't Go Far Enough, Seek Regulations Cover of NHTSA's new auto cybersecurity guide.
Cover of NHTSA's new auto cybersecurity guide.Stopping well short of issuing regulations, the U.S. federal government is proposing voluntary cybersecurity guidelines aimed at getting carmakers and their suppliers to secure computers and electronics in automobiles.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
The proposed guidance from the Transportation Department's National Highway Traffic Safety Administration, Cybersecurity Best Practices for Modern Vehicles, focuses on hardening a vehicle's electronic architecture against potential cyberattacks and ensuriing vehicle systems take appropriate actions even if an attack succeeds.
Hackers' Points of Entry
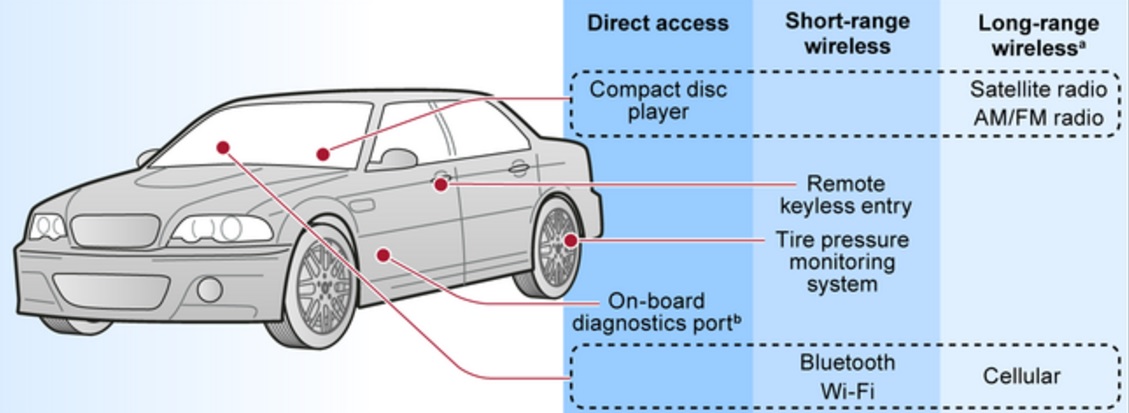 Source: Government Accountability Office
Source: Government Accountability Office"In the constantly changing environment of technology and cybersecurity, no single or static approach is sufficient," NHTSA Administrator Mark Rosekind says. "Everyone involved must keep moving, adapting and improving to stay ahead of the bad guys."
Layered Approach
The guidelines offer a layered approach to cybersecurity, which NHTSA contends would reduce the possibility of an attack's success and mitigate the ramifications of potential unauthorized access to a vehicle's computerized systems.
NHTSA says a layered method should:
Incorporate a risk-based approach to security that protects the vehicle's control systems and safeguards personally identifiable information contained in automotive systems; Provide for timely detection and rapid response to potential vehicle cybersecurity incidents; Include measures to facilitate rapid recovery from incidents when they occur; and Institutionalize methods for accelerated adoption of lessons learned across the industry through effective information sharing, such as through participation in the Automotive Information Sharing and Analysis Center.Mandatory Standards Sought
But the voluntary approach to implementing automotive cybersecurity standards didn't please two Democratic senators, Edward Markey of Massachusetts and Richard Blumenthal of Connecticut. "This new cybersecurity guidance from the Department of Transportation is like giving a take-home exam on the honor code to failing students," the senators say in a joint statement. "If modern day cars are computers on wheels, we need mandatory standards, not voluntary guidance, to ensure that our vehicles cannot be hacked and lives and information put in danger. In this new internet of things era, we cannot let safety, cybersecurity and privacy be an afterthought."
In the current Congress, both lawmakers introduced the Security and Privacy in Your Car Act, or the Spy Car Act, to require auto manufacturers to equip cars for sale in the U.S. "with reasonable measures to protect against hacking attacks." The legislation would require vehicles to be armed with the capabilities to immediately detect, report and stop attempts to intercept driving data or control of the vehicle.
But the bill is unlikely to get out of committee this year, let alone come up for a vote. Lawmakers and the Obama administration have been reluctant to issue cybersecurity regulations, and no groundswell exists in Washington to mandate automotive security standards. Instead, most lawmakers favor a voluntary collaborative approach between government and business to develop security standards. "These best practices, coupled with the continued partnership of government, academia, industry, security researchers and consumer groups, is a critical element of getting these technologies ready for our roads in the safest and securest manner possible," says Sen. Gary Peters, D-Mich., co-founder of the Senate Smart Transportation Caucus.
Regs Seen Stymieing Innovation
One automotive industry observer says the time isn't right for mandatory standards. "The technology is still in the process of developing, figuring out what is the best way to do this, how to address the problem of automotive security," says Sam Abuelsamid, senior research analyst at Navigant Research, a market research consultancy. "If we were to try and put a more solid regulation in place right now, it could stymie the development of some ideas."
Still, Abuelsamid says he could forsee the government requiring the auto industry to employ third-party auditors to review the software and architecture developed to secure vehicles. Cars and trucks contain much more code than other types of vehicles. According to the Battelle Memorial Institute, the not-for-profit research organization, a luxury sedan could contain more than 100 million lines of code; that's about 15 times more code than needed to operate systems in a Boeing 787 Dreamliner.
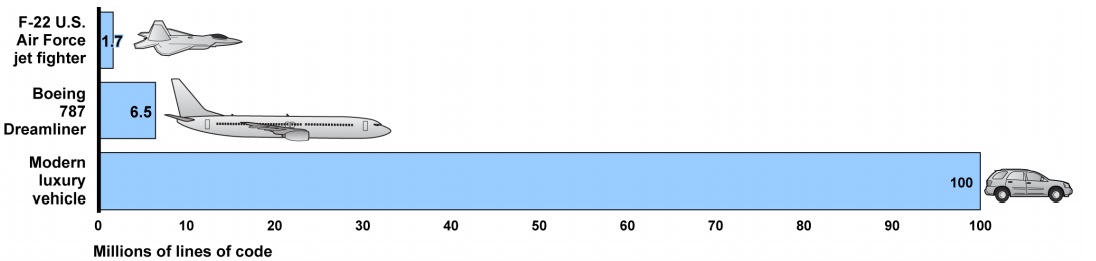 Source: Battelle
Source: Battelle
"A separate set of eyes are needed to look at the code for potential vulnerabilities because the people creating them tend not to see those [weaknesses]," Abuelsamid says. "Requiring some sort of process that includes third-party validation is probably a good thing."
The threat of cyberattacks on automobiles is real. So far, though, attacks have occurred in laboratory-type settings. For instance, Chinese researchers earlier this year remotely turned on the windshield wipers, opened a trunk and applied the brakes of a Tesla Model S sedan (see Tesla Patches Cars Against Wi-Fi 'Braking' Attack ).
In 2015, two hackers remotely triggered a 2014 Jeep Cherokee's brakes on a California highway. Also in 2015, the NHTSA issued a recall of 1.4 million Chrysler automobiles equipped with radios that have software vulnerabilities that could allow third parties access to networked vehicle control systems. "Exploitation of the software vulnerability may result in unauthorized remote modification and control of certain vehicle systems, increasing the risk of a crash," the recall notice states.
Future Prospects
In a report issued earlier this year by the Government Accountability Office, federal examiners contend a cyberattack on automobiles isn't imminent, but remains a possibility in the not-too-distant future. "To say that it hasn't happened in the past doesn't mean that it couldn't happen, because there are an awful lot of things that we didn't see happening in the past that have happened," says David Wise, GAO physical infrastructure issues director (see An In-Depth Analysis of How Automobiles Can Be Hacked).
If and when hackers begin to breach automotive IT systems, they'll likely seek profit over creating havoc on the highways. "There's probably going to be more attackers that are interested in trying to make money off of it," Abuelsamid says. "Ransomware and data theft are probably the two most likely scenarios. For the most part, most hackers are interested in making some money off of whatever [they're] doing."

