The ransomware-as-a-service operation known as Cerber is earning at least $200,000 per month via bitcoin ransoms paid by victims seeking to decrypt their PCs, says Gadi Naveh, a threat-prevention expert with Check Point Software Technologies.
Earlier this year, Check Point managed to access data feeds relating to Cerber and study how the cybercrime group operates, Naveh explains in an interview with Information Security Media Group at Black Hat Europe 2016 in London.
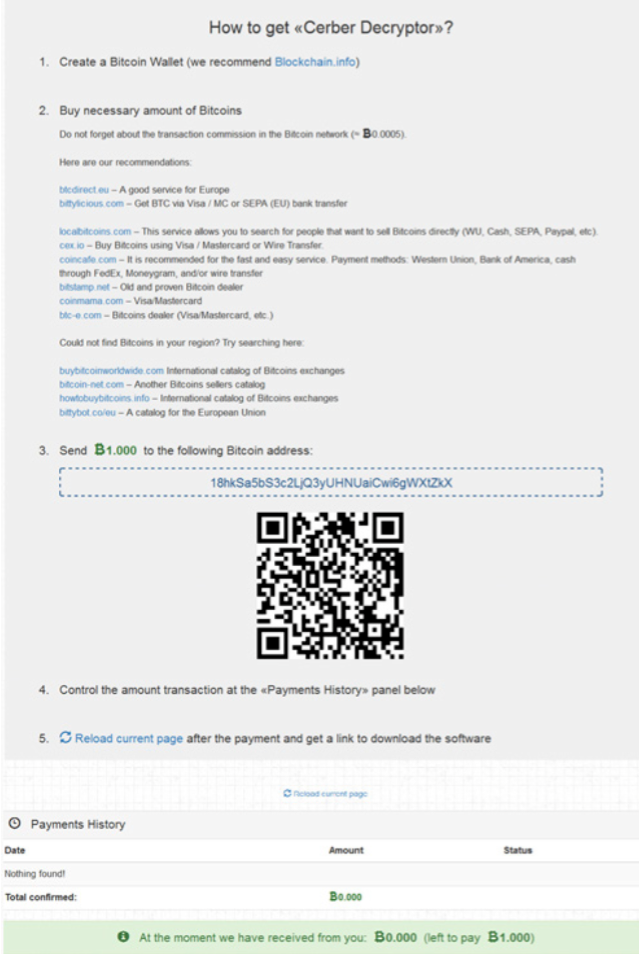 Cerber's lock screen instructs victims how to pay the ransom.
Cerber's lock screen instructs victims how to pay the ransom.The security company believes Cerber is run by a single group, though it's not clear which parts might get outsourced to other cybercrime service providers. But one key to Cerber's success is the fact that it's a highly automated operation, both for participants as well as for servicing ransom payments and distributing decryptors to victims who pay, Naveh says. "We see it pushing ... banking Trojans out of the market, because banking Trojans need much more customization to be done - at least in the retail sector," he says.
The Cerber group shares executable malicious code with participants, who register their bitcoin addresses with the operation, he says. Whenever the participant successfully infects a PC with a copy of the ransomware - typically via an exploit kit - and the victim pays the ransom, the Cerber participant automatically gets a cut of the proceeds deposited into their bitcoin account, Naveh explains.
Cerber ransoms are typically set at 1 bitcoin - currently worth about $700 - and about one out of every 600 users that gets infected with the ransomware, which forcibly encrypts numerous file types on their PCs, will ultimately pay the ransom, Naveh says. Along the way, however, Cerber participants may send millions of spam emails containing malicious attachments. "It's a very noisy operation," he says. "You can estimate lots of damage is done to generate this amount of revenue."
In this interview (see audio link below photo), Naveh discusses:
How the cybercrime service economy enables operations such as Cerber; Why ransomware is displacing banking Trojans; How using bitcoins enables attackers to cut out middlemen and better protect their operations.Naveh is an advanced threat prevention evangelist at Check Point Software Technologies Ltd. He previously worked in product development for Websense, as a security researcher for both Trusteer and Radware, and served as a researcher for the Israel Defense Forces.

