DDoS , Endpoint Security , Risk Management
But True Fix Requires a More Resilient Internet, Experts Warn Detail of an IoT component manufactured by Xiongmai
Detail of an IoT component manufactured by XiongmaiChinese manufacturer Hangzhou Xiongmai Technology will recall up to 10,000 webcams in the wake of massive distributed denial-of-service attacks driven, at least in part, by infected internet of things devices, Reuters reports.
See Also: Secrets to a Simpler Security Incident Response
The DDoS attacks targeted domain name server provider Dyn on Oct. 21, resulting in widespread website access disruptions. Affected sites ranged from Amazon, GitHub and Netflix to PayPal, Reddit and Twitter. Security researchers say the attacks were driven, at least in part, by Mirai malware, which targets default and hardcoded credentials in dozens of types of IoT devices. The source code for the malware was released last month.
Some - but far from all - of the devices targeted by Mirai included IoT components manufactured by Xiongmai. As a result, the company promised to recall some webcams, but only in the United States.
Now, Liu Yuexin, Xiongmai's marketing director, tells Reuters that the company has fixed the firmware used in components that it supplied to manufacturers this year and last. He said that the company will recall surveillance cameras in the United States for which updated firmware couldn't be installed, which he estimated numbered fewer than 10,000 vulnerable devices.
But it's not clear if Xiongmai's post-Mirai reaction plan will have any demonstrable effect. Xiongmai officials have previously claimed that, in 2015, the company updated its firmware to deactivate telnet by default, as well as to prompt users to change the default username and password. The company says the updated firmware has been made available for downloading from its site.
Some security experts, however, have questioned Xiongmai's claims. "The Mirai botnet is exploiting a 'backdoor' password that cannot be changed," Johannes Ullrich, dean of research for the SANS Technology Institute, says in a recent SANS Institute newsletter. "Only a firmware update will help. Right now, I don't see the firmware update available from [Xiongmai]."
But he adds that the manufacturer is far from the only IoT device maker to include hardcoded passwords in its components (see IoT Botnets: There Will Be Pwnage).
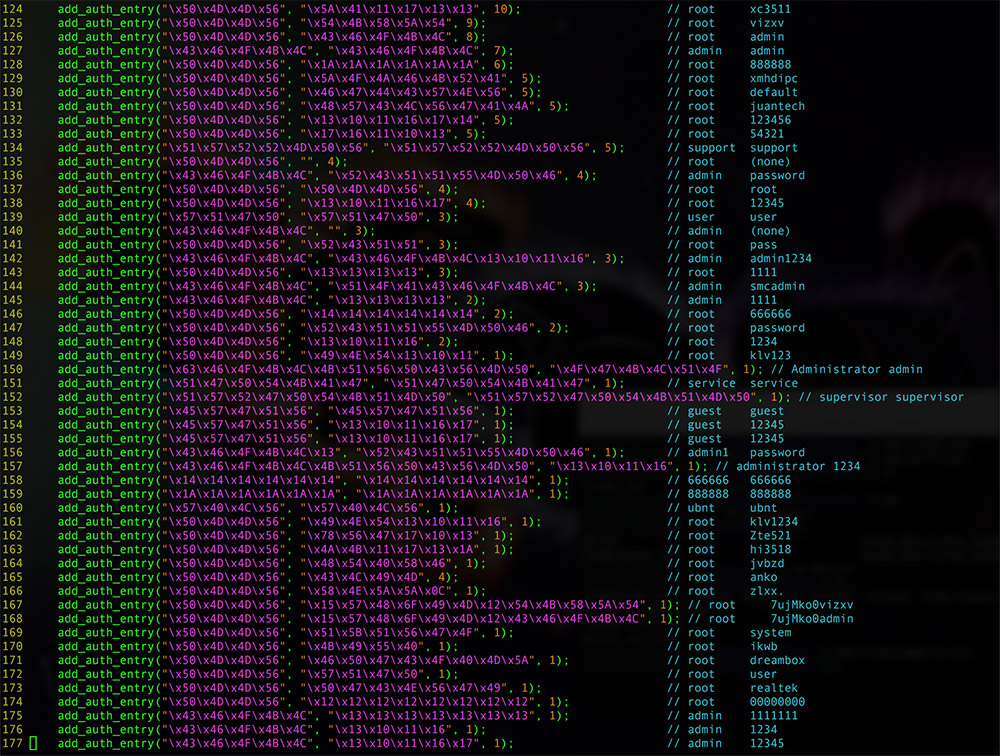 The Mirai source code targets hardcoded and default access credentials for many different types of IoT devices and components.
The Mirai source code targets hardcoded and default access credentials for many different types of IoT devices and components."While [Xiongmai] was somewhat singled out in this event, many other devices suffer from hardcoded 'backdoor' or 'support' passwords that the user cannot change," he says. After attackers begin targeting these hardcoded passwords, he adds, rather than removing them entirely, manufacturers often just update firmware with "a different password instead of eliminating this function."
Mounting Evidence: No Nation-State Attacker
To date, it's not clear who launched the DDoS attacks against Dyn, how many botnets might have been used, whether all of the attacks were enabled via IoT devices infected by Mirai or other malware, or if DDoS-on-demand stresser/booter services were also brought to bear.
The U.S. Department of Homeland Security is investigating the attacks, as well as "working with law enforcement, the private sector and the research community to develop ways to mitigate against [Mirai] and other related malware."
Sen. Mark Warner, D-Va., who heads the Senate Cybersecurity Caucus, has also written letters to DHS, the Federal Communications Commission and the Federal Trade Commission querying what tools and tactics are available to battle IoT malware - and which new ones the agencies might want to see get developed.
"The weak security of many of the new connected consumer devices provides an attractive target for attackers, leveraging the bandwidth and processing power of millions of devices, many of them with few privacy or security measures, to swamp internet sites and servers with an overwhelming volume of traffic," Warner says in a statement. "I am interested in a range of expert opinions and meaningful action on new and improved tools to better protect American consumers, manufacturers, retailers, internet sites and service providers."
Asking @FCC @FTC @DHSgov to look look into the #zombie #cyber attacks that swamped popular sites. https://t.co/RuG3dgabBY
Not Suspected: Nation-State Attackers
As Information Security Media Group has previously reported, security experts say the DDoS attacks against Dyn were likely launched by attackers who are also gamers, in part because the attacks were announced in advance as targeting the launch of a new Electronic Arts game. That implies that the attackers are relatively young men with no particular agenda to advance, except perhaps advertising their own stresser/booter services.
Supporting evidence for that theory continues to mount. Speaking at the Council on Foreign Relations in New York on Oct. 25, National Intelligence Director James Clapper said early indications are that the DDoS attack against Dyn were launched by a "non-state actor," the Associated Press reports.
Security intelligence firm Flashpoint, meanwhile, says that the release of the Mirai source code and related chatter on the script-kiddie forum known as HackForums suggest that individuals with an interest in stresser/booter services might have been involved in the Dyn disruptions.
"The technical and social indicators of this attack align more closely with attacks from the Hackforums community than the other type of actors that may be involved, such as higher-tier criminal actors, hacktivists, nation-states and terrorist groups," Flashpoint researchers say in a blog post. "These other types of threat actors are unlikely to launch such an attack without a clear financial, political or strategic objective, and they are very unlikely to launch an attack against a video game company."
Required: More Internet Resiliency
The internet disruptions triggered by IoT-powered DDoS attacks against Dyn are far from the first time that attackers have marshaled infected IoT devices to do their bidding.
"This issue highlights a bigger problem that I feel is often overlooked with IoT," information security consultant Brian Honan, who is a cybersecurity adviser to the EU's law enforcement intelligence agency Europol, writes in a recent SANS Institute newsletter. "We struggle to convince companies and individuals to keep their PCs patched. This is going to be a bigger challenge in IoT. We need to make the internet more resilient as more and more of these devices will become security threats over time."
With luck, the attacks against Dyn will serve as a wake-up call for the industry, says Dan Kaminsky, chief scientist at anti-malware firm White Ops.
"Nothing survives floods of this nature, existing or theoretical, centralized or decentralized," Kaminksi tells The Guardian. "It all falls over. The hard questions here are about preventing this sort of exposure in the first place, and about improving our ability to respond and remediate when we do get it wrong."
"DNS sucks!"
"And what would you replace it with?"
And that's when the Ninja Smoke Bombs come out. *whoosh*
But massive outages often focus attention on developing and implementing fixes, says Kaminsky, who in 2008 discovered - and single-handedly patched - a serious flaw in DNS. "The unifying principle of the internet is reliability, and systems went down," he said. "That tends to cause improvement. 'If we don't do this, bad things will happen' is not as compelling as 'if we don't do this, bad things will happen again.'"

