Anti-Malware , DDoS , DDoS Attacks
Mirai-Infected IoT Devices Are Involved, Security Firm Flashpoint Reports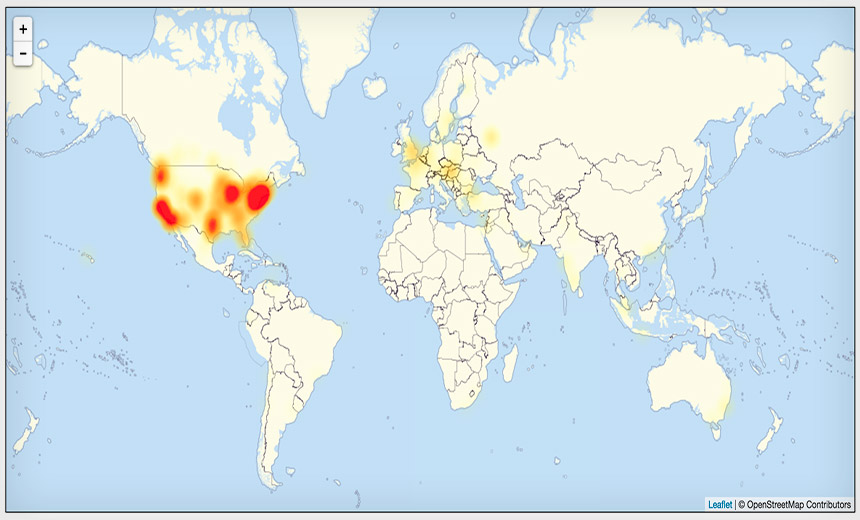 Map of outages reported by users of the downdetector site for the past 24 hours.
Map of outages reported by users of the downdetector site for the past 24 hours.Unprecedented distributed denial-of-service attacks that began in the early hours of Oct. 21 triggered widespread internet disruptions, with numerous sites remaining intermittently inaccessible. Major sites, including Amazon, PayPal, Spotify and Twitter have been affected.
See Also: Managing Identity, Security and Device Compliance in an IT World
The attack has been focused on domain name system provider Dyn, and the perpetrator remains unknown (see DDoS Attack Blamed for Massive Outages).
Security intelligence firm Flashpoint reports that the botnet is composed, at least in part, of internet of things devices infected by Mirai malware (see IoT Botnets: There Will Be Pwnage). Mirai malware has previously been tied to record-setting attacks against security researcher Brian Krebs as well as Paris-based French hosting giant OVH that used infected internet of things devices, including routers, webcams and internet-connected security cameras and digital video recorders.
"Flashpoint has confirmed that some of the infrastructure responsible for the distributed denial-of-service (DDoS) attacks against Dyn DNS were botnets compromised by Mirai malware," the company says in a research report published late on Oct. 21. As of 5:30 p.m. Eastern Time, "the attacks against Dyn DNS are still ongoing," it says, adding: "Flashpoint is coordinating with multiple vendors and law enforcement to track the infected devices that constitute the botnet being used to conduct these attacks."
By 6:17 p.m. on Oct. 21, however, in an incident report into the "DDoS Attack Against Dyn Managed DNS," Dyn reported that "this incident has been resolved."
The use of Mirai malware, however, is no smoking gun demonstrating that the previous, record-setting DDoS attacks were perpetrated by the same attacker or group. That's because a copy of the Mirai malware source code was recently leaked by a hacker known as "Anna-senpai" Now anyone can be - and has been - rolling their own Mirai botnet. "Since this release, copycat hackers have used the malware to create botnets of their own in order to launch DDoS attacks," Flashpoint says. Furthermore, the Dyn-targeting DDoS attacks against Dyn came from "separate and distinct botnets" from the ones used against Krebs and OVH's sites.
"The real problem we all now have is that the Mirai code is out in the wild. It's like putting biological weapons within reach of children - some idiot is bound to use it just to see if they can," says Alan Woodward, a computer science professor at the University of Surrey.
Perpetrator Unknown
 The Mirai source code was released by "Anna-senpai."
The Mirai source code was released by "Anna-senpai."Whistle-blowing WikiLeaks has claimed that the attacks are revenge for founder Julian Assange's internet connection being temporarily taken away. But it's provided no evidence to back up that assertion.
"It is unknown if the attacks against Dyn DNS are linked to the DDoS attacks against Krebs, OVH, or other previous attacks," Flashpoint says. "Given the proliferation of the Mirai malware, the relationship between the ongoing Dyn DDoS attacks, previous attacks, and 'Anna_Senpai' is unclear."
Woodward, who is also a cybersecurity adviser to the EU's law enforcement intelligence agency Europol, cautions too that Mirai may not be the full story here. "One point yet to be clarified is that the Mirai botnet appears to be responsible, but maybe only in part," he says. "The question is: What else is it?"
Weaponized CCTVs? Just the Start
The attacks may not be a one-off. That's not an attempt to stoke fear, uncertainty and doubt, but rather a reflection that someone has obviously been building this attack capability, their intentions remain unknown, and so far there are no easy defenses against these types of attacks.
From the worst-case scenario perspective, security expert Bruce Schneier, CTO for IBM's Resilient Systems, warned last month that someone has been testing how to take down the internet. "Over the past year or two, someone has been probing the defenses of the companies that run critical pieces of the Internet," Schneier wrote on the Lawfare blog. "These probes take the form of precisely calibrated attacks designed to determine exactly how well these companies can defend themselves, and what would be required to take them down. We don't know who is doing this, but it feels like a large a large nation state. China and Russia would be my first guesses."
The problem is compounded by the burgeoning number of internet-connected devices that continue to be built, for which security seems to be an afterthought. Indeed, security experts say that numerous internet-connected devices - ranging from routers and smart TVs to refrigerators and security cameras - will often be connected to the internet by consumers and then forgotten about, unless they somehow fail. Furthermore, many manufacturers fail to get security updates into consumers' hands, or release any patches at all, often preferring instead to simply ship a newer type of product.
When Toasters Attack
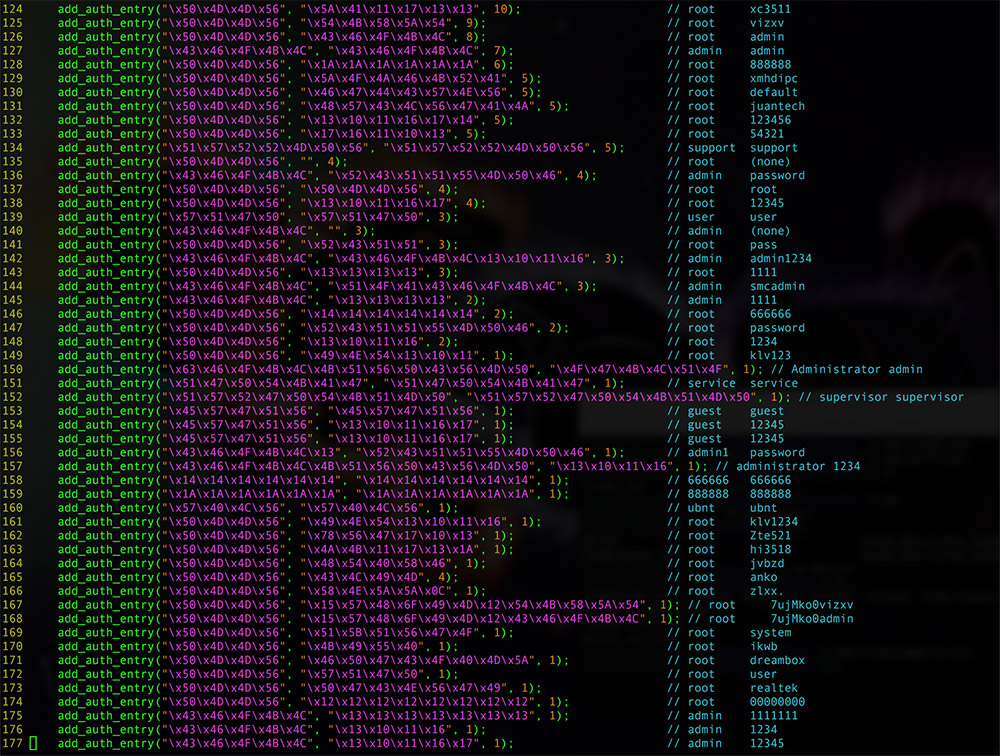 Mirai targets default credentials in IoT devices, which many consumers and businesses fail to change.
Mirai targets default credentials in IoT devices, which many consumers and businesses fail to change.
Woodward says he's not sure there's yet enough evidence to support Schneier's assertion that someone is testing ways to scupper the internet. Even so, "it does look like this another manifestation of our toasters come back to haunt us," not least because "Mirai is particularly successful at exploiting equipment from one Chinese manufacturer." That's a reference to Chinese high-technology firm XiongMai Technologies, which Allison Nixon, director of research at Flashpoint, tells Krebs is responsible for manufacturing numerous components that are used by manufacturers of IoT devices that have been infected with Mirai.
Woodward says it's not yet clear whether the devices sport default credentials, or if the credentials are tough to change. "Either way, it throws into stark relief the problem of the IoT - it's cheap and not very cheerful," he says. "If your IoT device proves to be vulnerable it is going to be so cheap that there is unlikely to be a fix for it. The manufacturers are producing these devices to a price point that means it's cheaper for them to assume you'll have to bin the item, even if they had a way of getting any fix to you."
Business Continuity: Lessons Learned
So far, the full impact - or duration - of the DDoS attacks against Dyn remains unclear. But already, one short-term victim may be Dyn. Security researchers report that numerous sites have either stopped using Dyn's DNS services, or else added backups.
But the Dyn disruption is already spurring many companies - including the likes of PayPal - to refine their defenses. And of course as U.K.-based security researcher Kevin Beaumont, who tweets as @GossiTheDog, notes, that's a good thing.
Major sites have made DNS nameservers changes over last 24 hours either away from or diversifying from Dyn. Suggests it had big biz impact.
"If you're a company who got hit by Dyn DNS outage: use a second provider for second nameserver. Mirror DNS records using automated tools," Beaumont says via Twitter. "Secondary DNS *should be* secondary DNS. Zone transfers and secondary DNS exist for a reason. If porn sites can do it right, so can PayPal."

