Anti-Malware , Data Loss , Technology
Thanksgiving Attacker Demands 100 Bitcoins, Threatens 30 GB Data Dump Muni light rail train in San Francisco. Credit: David Wilson (Flickr/CC)
Muni light rail train in San Francisco. Credit: David Wilson (Flickr/CC)(This story has been updated.)
See Also: Fencing an Imaginary Yard; How to Secure your IP with an Unidentifiable Network Perimeter
"You Hacked, ALL Data Encrypted."
That was part of a message that reportedly appeared on thousands of Windows systems used by the San Francisco Municipal Transportation Agency, better known as Muni, in recent days, after they were locked by ransomware and 100 bitcoins - currently worth $73,000 - demanded in exchange for a decryption key.
The attack, which compromised more than 2,000 Muni payment and scheduling systems, began unfolding by Nov. 25 - during the busy Thanksgiving and Black Friday shopping period - reports San Francisco Examiner. As a result, officials ordered Muni subway fare gates to be opened - and all light-rail rides were free - as IT personnel worked to scrub the ransomware from affected systems.
Apparently the SF Muni fell victim to ransomware last night #sanfrancisco #infosec pic.twitter.com/E1OVQpAAzY
"We can confirm a cyberattack," Muni spokesman Paul Rose tells Information Security Media Group. "It disrupted some of our internal computer systems, such as email. Fare gates are again operational."
Rose says the turnstiles were left open - so people could ride the subway for free - as the organization worked to mitigate the ransomware infection. "We opened them on Friday and Saturday [Nov. 25 to 26] as a precaution to minimize any possible impacts to customers," he said. "There has been no impact to transit service, to our safety systems or to our customer's personal information. The incident remains under investigation, so it wouldn't be appropriate to provide any additional details at this point."
Rose said the attack didn't have any impact on the city's iconic street cars.
News of the attack was first broken by CBS San Francisco, which said that the ransomware may have also locked Muni's payroll systems. Rose declined to comment on that possibility.
Muni would lose an estimated $559,000 for every day that it was unable to collect fares, according to its operating budget (see Ransomware Extortion: A Question of Time).
Political Statement?
Some Muni users, via Twitter, asked if the Muni ransomware lockdown might have been a political act - as in, free rides for the masses. "I hope the hacker who made @sfmta_muni free yesterday did it as a political statement," said Twitter user Keith Beneath. "Public transit should always be free."
But the full message displayed by the ransomware - "You Hacked, ALL Data Encrypted. Contact For Key(This email address is being protected from spambots. You need JavaScript enabled to view it.)ID:681,Enter." - implied that the attack was simply an attempt by criminals to shake down a victim for bitcoins.
Criminal Shakedown
In fact, this does appear to be a criminal shakedown.
"We do this for money, nothing else !" said someone calling themselves "Andy Saolis," in reply to an email sent to the ransom note's email address by the San Francisco Examiner.
Saolis claimed to San Francisco news website Hoodline that 2,112 Muni systems were successfully locked by a variant of the HDDCryptor malware, a.k.a. Mamba, using AES 2048-bit crypto.
Meanwhile, Saolis tells ISMG via email that the attack successfully infected and crypto-locked both PCs and servers. "We hacked 2000 server/PC in SFMTA including all payment kiosk and internal automation and email and ...!" he says. Saolis added that the infection had been random, and suggested that it might have been much worse had Muni been the victim of a targeted attack.
Saolis is also threatening to dump 30 GB of stolen data - including contracts and employees' personal information - unless Muni pays the ransom (see Please Don't Pay Ransoms, FBI Urges).
"We don't live in USA but I hope company try to fix it correctly and we can advise them but if they don't, we will publish 30G databases and documents include contracts, employees data, LLD plans, customers and ... to have more impact to company to force them to do right job!" Saolis wrote in his email.
HDDCryptor Can Infect Networked Drives
Security researchers say that whoever is behind HDDCryptor often uses the alias "Andy Saolis" when communicating with victims, and note that the ransomware can infect not just PCs, but also network-connected drives, servers and other devices.
"HDDCryptor not only targets resources in network shares such as drives, folders, files, printers, and serial ports via Server Message Block (SMB), but also locks the drive," according to a ransomware teardown published by security firm Trend Micro in September. "Such a damaging routine makes this particular ransomware a very serious and credible threat not only to home users but also to enterprises."
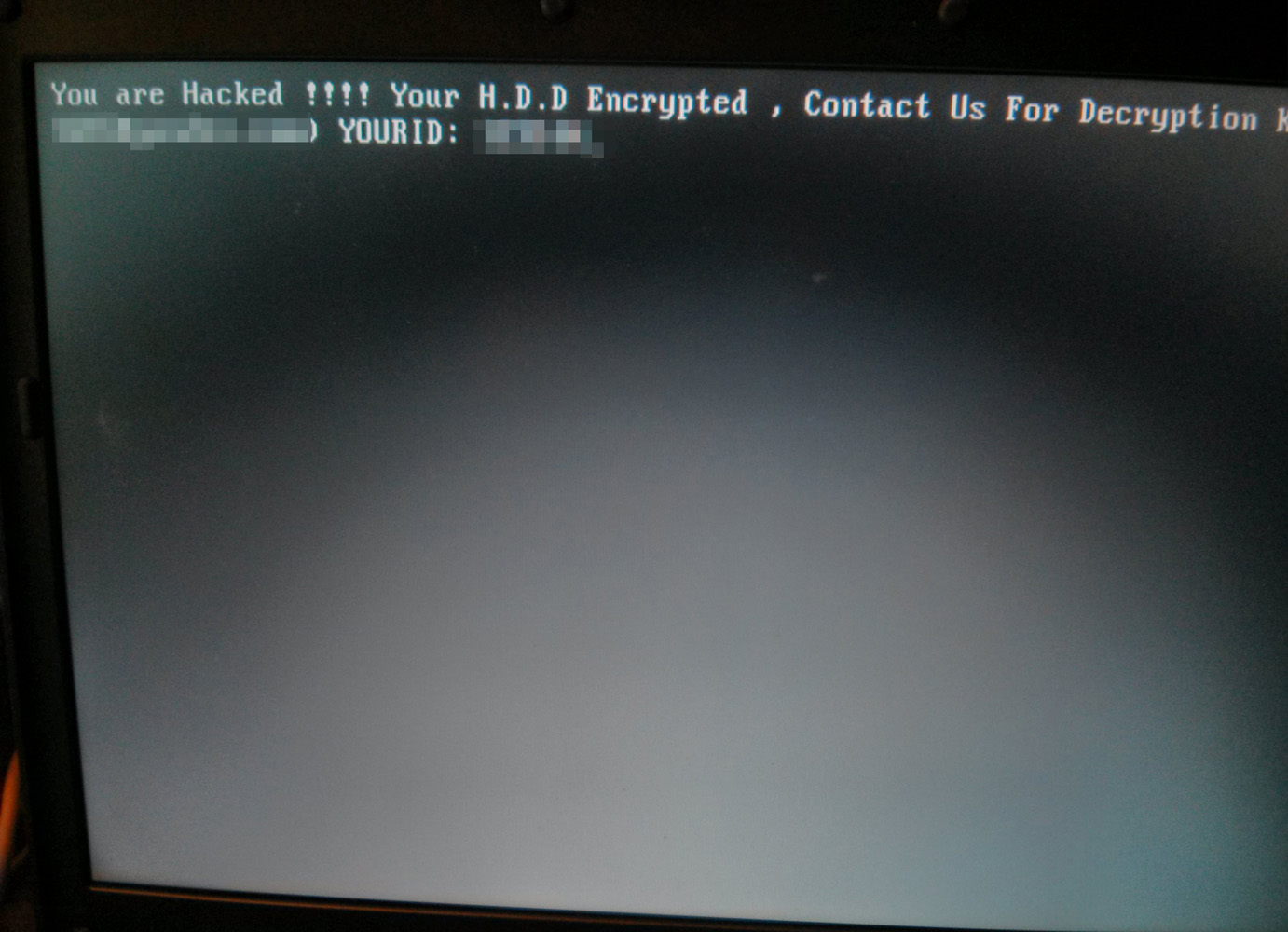 A previously seen HDDCryptor (a.k.a. Mamba) ransom note. Source: Trend Micro
A previously seen HDDCryptor (a.k.a. Mamba) ransom note. Source: Trend MicroMuni officials declined to comment about how quickly they expected to expunge the ransomware infection, whether they would pay the ransom, whether they planned to instead restore affected systems as well as whether they expected to lose any information as a result, for example if some backups might have been outdated. Muni has also not released any information about the version of Windows being used by infected devices, and what - if any - security software defenses may have been in place on those systems.
Of course, Muni is only the latest in a long line of ransomware victims, which have included not only individuals but also a number of organizations and enterprises, ranging from hospitals and police departments to universities and smart TVs.
Ransomware Defense: Keep Backing Up
Last week, at ISMG's Fraud and Data Breach Prevention Summit in Singapore, security experts speaking on a panel devoted to stopping ransomware said that backups remain the No. 1 defense.
"For business continuity, just make sure that you actually back up your data - that's one way to recover it if you actually do suffer an infection," said Paolo Miranda, the membership director for nonprofit membership organization (ISC)2 in Singapore.
"Back up so it's not connected to your network - that's most important," added Robert Poh, director of the Singapore program at Financial Services Information Sharing and Analysis Center, a.k.a. FS-ISAC.

