Breach Preparedness , Breach Response , Data Breach
Could a Defensive Hack Fix the Internet of Things? Warning: Bricking Devices May Disarm Hackers But Trigger Unintended Fallout Internet-connected XiongMai components comprise at least part of the Mirai botnet.
Internet-connected XiongMai components comprise at least part of the Mirai botnet.Neutering the army of web-connected devices used in the large internet attack that hampered access to major sites - including Amazon, PayPal, Spotify and Twitter - is technically possible. But no option offers either a great or near-term fix.
See Also: Main Cyber Attack Destinations in 2016
One option is to counterhack the infected devices and permanently break them, via what's known as "bricking." But the ethics around interfering with people's devices are sticky, and most countries would consider any such intervention to be illegal.
A less intrusive idea would be for ISPs to notify customers that, for example, their baby monitor is involved in a mass internet attack - a kind of alert that most parents struggling with little sleep might find bizarre. Coordinating a global campaign involving ISPs is also likely to be daunting and ultimately piecemeal.
The unfortunate takeaway: Essentially, there's no good solution to avoid future distributed denial-of-service attacks on the scale of last week's interruptions, which showed an aggressive escalation of a problem long warned about by computer security experts.
A 'Dyn-amic' Assault
The vast collection of surveillance cameras and other internet-connected devices, some of which are infected with the Mirai malware, can't be easily fixed. The latest attacks barely differed from those executed in mid-September against French hosting provider OVH and Brian Krebs' security blog, but generated a whole lot more attention. The latest wave focused on a provider of domain name system services, Dyn (see Mirai Botnet Pummels Internet DNS in Unprecedented Attack).
The DNS is the internet's addressing system, which enables a web browser to find the right IP address for a domain name. Dyn is one of many companies that offer outsourced management of DNS for the likes of PayPal and Twitter. As the attacks showed, a concentrated assault on one DNS provider can have a severe knock-on effect, even if the services themselves haven't been directly attacked.
The culprits behind the Dyn attack are, yet again, millions of mundane but insecure devices, such as digital video recorders, baby monitors and other low-grade consumer devices with an internet connection that have been corralled into a botnet. Such devices too often ship with default or easily guessable passwords, allowing hackers to infect them with DDoS attack code (see Hacked IoT Devices Unleash Record DDoS Mayhem).
But those devices' poor security also presents a luring opportunity: Security researchers or law enforcement could instead seize control of the devices and disable them.
Lessons Learned From Spam Battles
Less than a decade ago, large botnets functioned as spam cannons, overwhelming email users en masse. But law enforcement and security companies found effective ways to curtail these botnets.
Some of those methods involved taking over command-and-control servers, which are machines used to distribute instructions to infected computers. ISPs often assist in such operations, which cut off botnet operators from their armies.
But in 2010, Dutch police went one step further when shutting down a botnet called Bredolab. They took over Bredolab's command and control servers and then did something unprecedented: They uploaded their own code to the infected computers.
The code directed a computer's web browser to a special website set up by the Netherlands Police Agency, which advised them to remove the malware. Technically, it was a hack, albeit an altruistic one, but one which would likely have violated computer security laws in most countries.
Likewise, owners of Mirai-infected devices could also receive such alerts from their ISPs, or see even more extreme action, such as the devices being remotely bricked. Lauri Love, a British citizen facing hacking-related charges in U.S. federal court, posed this possibility on Twitter.
"Should I unilaterally dismantle the Mirai botnet, which would take about two hours of work and break the law in 90 percent of the world's nation-states?" he writes.
Should I unilaterally dismantle the Mirai botnet, which would take about 2hr of work and break the law in 90% of the world's nation-states?
— Lauri Love (@LauriLoveX) October 23, 2016But such actions could have severe consequences for owners of the Mirai-infected CCTV systems and digital video recorders, many of whom live in Vietnam, Brazil and Turkey, says Allison Nixon, director of security research at security intelligence firm Flashpoint.
"These CCTV systems are important to their owners because they collect evidence of crimes, and it may be that once these DVRs get bricked, maybe the owners won't find out until after their store's been robbed, and maybe they will find out there's no footage because their DVR got bricked," she says. "If someone were to go out and brick all the DVRs, their actions may have consequences that they will never know about and never be able to account for."
Ethical concerns aside, there are also technical problems with bricking. After Mirai infects a DVR, the malware takes steps to block someone else from doing the same.
One major problem is so-called internet of things manufacturers have sold devices with remote access protocols such as telnet enabled with default login credentials. After Mirai infects a device, it shuts down telnet, making it impossible to take control of it again that way.
Rebooting a Mirai-infected device will erase the malware, but on average it takes less than five minutes for the device to become reinfected, says the researcher behind the MalwareTech blog. He thinks researchers could get to the rebooted devices before hackers do - but still, it would be a race.
Xiongmai Finally Responds
While there are many manufacturers and brands of IoT devices, one Chinese vendor has received the majority of the blame: XiongMai Technologies of Hangzhou.
Although there are millions of insecure IoT devices, Flashpoint estimates that between 495,000 to 560,000 have vulnerable critical components made by the company.
XiongMai doesn't actually sell digital video recorders. Instead, it manufacturers circuit boards with preinstalled firmware, which then get sold to many other vendors that create the finished product, says Zach Wikholm, a Flashpoint security researcher. The products, sold since at least 2004, are operating from at least 124 countries.
"These things are everywhere," Wikholm says.
XiongMai, which was quickly identified after the attacks against Krebs' website, has been silent on the problems - until now. In an Oct. 23 email statement, the company acknowledged that hackers had taken over its components.
"Mirai is a huge disaster for the internet of things," writes Cooper Wang, XiongMai's international sales director.
Wang claims that in September 2015, XiongMai stopped shipping firmware that has telnet enabled by default. He also says that users are prompted - when they turn on a new device - to change the default username and passwords. The company is also advising people to update to the latest firmware.
Flashpoint says it's already investigating those claims, but on initial inspection, they appear to be doubtful. Flashpoint's Wikholm obtained the latest version of firmware released by XiongMai, which is dated Oct. 18. Telnet is still turned on, and the root password hasn't been changed, he says. "There could be a difference that we're not seeing," but it's unlikely, Wikholm adds.
Flashpoint has contacted XiongMai several times but gotten no response, he says. The statement the company released is the first time it has addressed the issues. Likewise, Information Security Media Group has reached out multiple times to XiongMai for comment, but heard no reply.
Insecure, Off the Shelf
As part of Flashpoint's research, Wikholm says that over the weekend, he bought a hybrid digital video recorder - a type of a DVR - made by a company called KKMoon.
The HVR's firmware - made by XiongMai - is dated Aug. 31, 2015. Telnet is enabled by default, and the root password hadn't been changed. Even worse, Wikholm says he can't figure out how to update the firmware. If a professional security researcher can't do that, then there's a next to nil possibility consumers would be able to do it.
Nixon says it's possible that the device Wikholm purchased has sat on a shelf for more than a year. But if not, "then I'd call [XiongMai's] statement into question," he tells me.


 Photo: Yahoo
Photo: Yahoo NIST Fellow Ron Ross
NIST Fellow Ron Ross Cover of NHTSA's new auto cybersecurity guide.
Cover of NHTSA's new auto cybersecurity guide.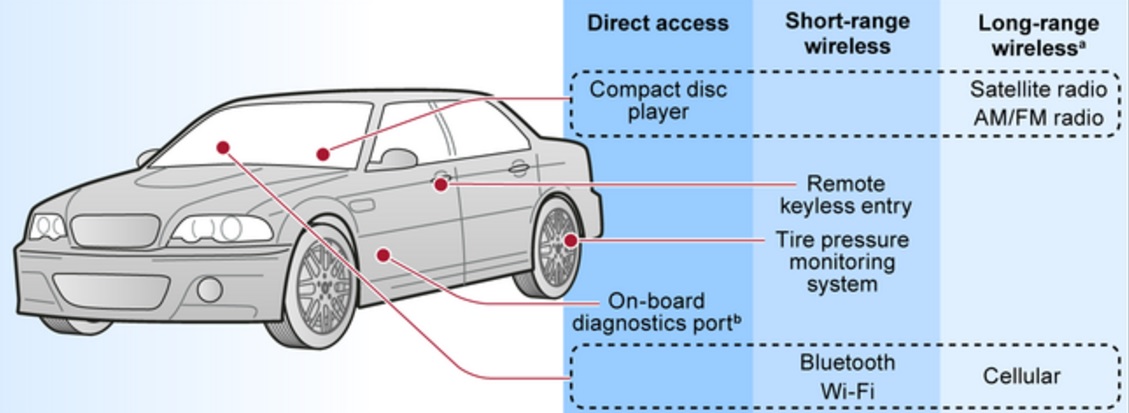 Source: Government Accountability Office
Source: Government Accountability Office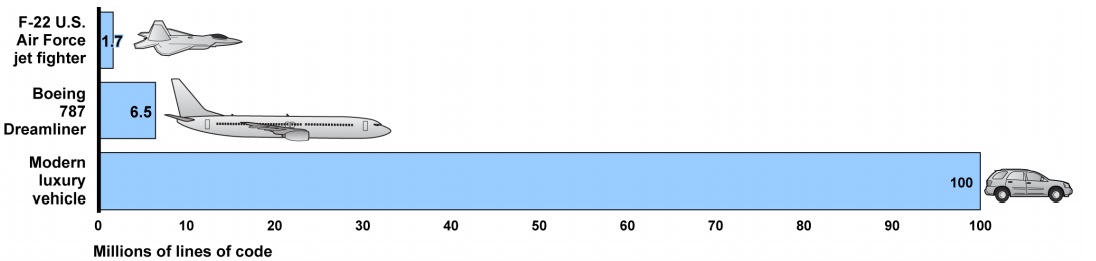 Source: Battelle
Source: Battelle Detail of an IoT component manufactured by Xiongmai
Detail of an IoT component manufactured by Xiongmai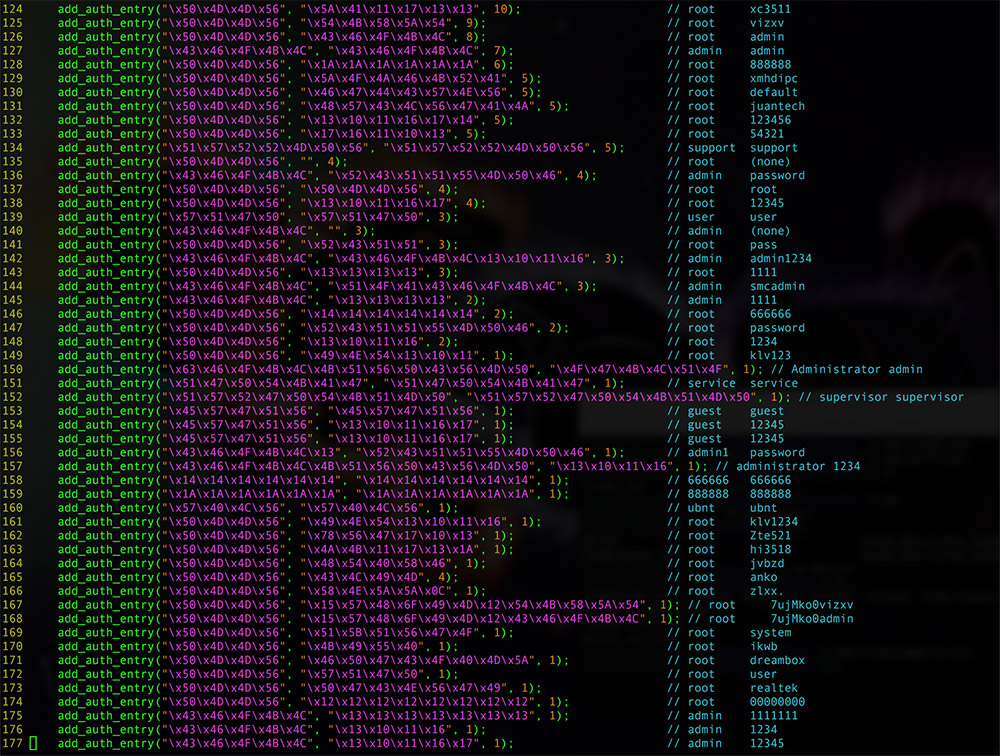 The Mirai source code targets hardcoded and default access credentials for many different types of IoT devices and components.
The Mirai source code targets hardcoded and default access credentials for many different types of IoT devices and components.