Cybercrime
,
Fraud Management & Cybercrime
,
Governance
Social-Planning Website Says Pre-2014 User Database Has Been Stolen(
euroinfosec)
•
June 11, 2019

It's hackers' party; cry if you want to.
Online invitation site Evite says it was hacked and information on an unspecified number of users was stolen. Although the breach appears to have happened between Feb. 22 and May 14, the stolen information dates from 2013 and before.
See Also: Webinar | The Future of Adaptive Authentication in Financial Services
Founded in 1998, Los Angeles-based Evite is a social-planning website that allows users to create, send and manage online invitations.
"Back in 2013, I was beginning to get the sense that data breaches were becoming a big thing."
"Potentially affected information could include names, usernames, email addresses, passwords and, if optionally provided to us, dates of birth, phone numbers and mailing addresses," Evite says in its data breach notification.
"We continue to monitor our systems for unauthorized access, have introduced additional security measures, and will be prompting affected Evite users to reset their Evite passwords on their next log-in," it adds.
So on the upside, if hackers want to invite you to their party, it's possible they're not going to get your contact details right.
On the downside, Evite says whoever stole the data can use it to send phishing messages that may well get through.
Existential Issues
The Evite breach is a reminder of this perpetual, existential data breach problem: We don't know how bad data breaches are because we don't know how many more super-bad historical mega-breaches have yet to come to light. Furthermore, if an organization gets badly breached today, but the breach doesn't get discovered for another five or 10 years, our future view of today's data breach landscape will have to be revised (see: Battling Big Breaches: Are We Getting Better?).
Many breaches don't go years before being detected. FireEye's Mandiant 2019 M-Trends report found that for breaches that an organization self-discovered in 2018, attackers had been inside the network for an average of 50.5 days. But when an organization was tipped off to the breach from an external source, as Citrix was, attackers had already been inside the network for an average of 184 days, or just over six months (see Citrix Hackers Camped in Tech Giant's Network for 6 Months).
But historical breaches that go undiscovered - or, as in the cases of LinkedIn and Yahoo, were poorly investigated or covered up - continue to crop up.
So, too, do organizations that lose information that they should never have left lying around. This concept, known as data minimization, is a cornerstone of the EU's General Data Protection Regulation. Thanks to GDPR, at least where Europeans' personal data is concerned, it belongs to individuals, and any organization that stores the data does not own it, but must safeguard it. Part of that safeguarding requires the organization to regularly review what it is storing and why, and if it should not be storing the data any longer, to delete it.
Evite's Passive Data Breach Voice
Evite says one or more hackers managed to obtain an "inactive data storage file associated with Evite user accounts."
The company says it's continuing to investigate the breach. "Upon discovering the incident, we took steps to understand the nature and scope of the issue, and brought in external forensic consultants that specialize in cyberattacks. We coordinated with law enforcement regarding the incident, and are working with leading security experts to address any vulnerabilities."
Unfortunately, Evite users whose data was stolen could be easily targeted, as the company writes in a breach notification that makes heavy use of the passive voice (see: Hackers Love to Strike on Saturday).
"Emails regarding this issue were sent to users whose personal data was stored in the inactive data storage file that was acquired by the unauthorized party," Evite says.
By that, Evite meant that it has been emailing affected users directly. But it warns that such emails could come from anyone. "Please note that the email from Evite does not ask you to click on any links or contain attachments and does not request your personal data," it says. "If the email you received about this issue prompts you to click on a link, suggests you download an attachment, or asks you for information, the email was not sent by Evite and may be an attempt to steal your personal data."
The company didn't immediately respond to a request for comment about how many users were affected or in which geographies. The company's data breach notification, however, lists contact telephone numbers for both U.S. and international users.
Here's What Active Security Looks Like
Breaches such as Evite's make some of the security features built into Apple's forthcoming iOS 13 mobile operation system look like a great idea. Using the new operating system, for any iOS app, you will be able to have iOS hide your email address for any service you sign up to. Behind the scenes, Apple will supply a random email address to the app, then relay any messages. As a result, this will mean that if the service suffers a breach, attackers won't have your real email address. In addition, it would likely make it easier for the likes of Apple to spot emerging phishing attacks and block those too. The new version of iOS is due out this fall.
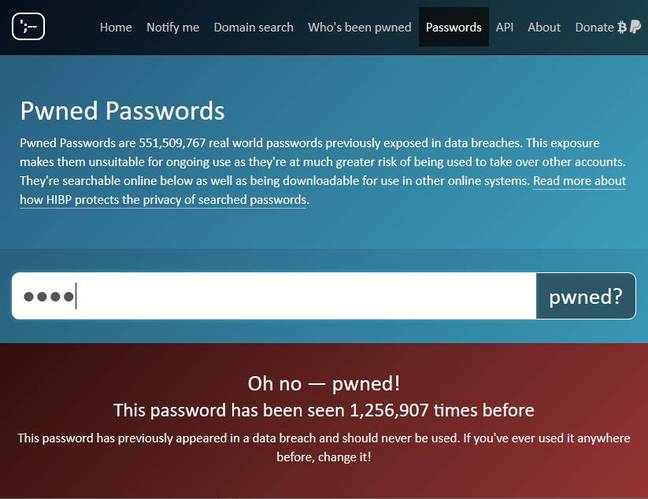
News of the Evite breach arrives the same day that Troy Hunt, the Australian developer who created the free Have I Been Pwned? breach notification service nearly six years ago, announced that the service has grown so big that he's exploring M&A possibilities for its future. The service allows anyone to register an email address and then sends an alert to that email.
The Australian government and the U.K. National Cyber Security Center - the public-facing arm of GCHQ - are among the organizations that are working with HIBP to monitor their own domains.
Simpler Times
"Back in 2013, I was beginning to get the sense that data breaches were becoming a big thing," Hunt writes in a Tuesday blog post.
Since them, however, HIBP has grown to encompass 8 billion breached records that Hunt loads in. Speaking at least week's Infosecurity Europe conference in London, where he was inducted into the conference's hall of fame, Hunt said he only learns when his information has appeared in a breach cataloged by HIBP when the site emails him as well, which he said has happened so far more than a dozen times.
Hunt says that nearly 3 million individuals have subscribed to HIBP to get notifications when their email appears in a data dump, as have numerous administrators of sites run by businesses, government agencies and others. "I've emailed those folks about a breach 7 million times, there are 120,000 people monitoring domains they've done 230,000 searches for and I've emailed them another 1.1 million times."
As organizations continue to get breached and to discover old breaches, of course that number is going to continue to rise.
All of this breached data is a boon for nation-state espionage teams as well as cybercriminals, because it gives them more ways to potentially blackmail individuals, commit identity theft, steal online banking credentials, trick users into executing ransomware or wage other types of attacks.
Where data breaches are concerned, it's still hackers' party. You can cry if you want to.




 Image copyright
davelogan
Image caption
Facial recognition cameras are used widely at border crossings
Image copyright
davelogan
Image caption
Facial recognition cameras are used widely at border crossings
 It's hackers' party; cry if you want to.
It's hackers' party; cry if you want to.