Authentication
,
ID & Access Management
,
Multi-factor & Risk-based Authentication
Cause for Celebration: Microsoft Stops Recommending Periodic Password Changes(
euroinfosec)
•
May 2, 2019

Hallmark alert: Hands up if you hate "days" devoted to this or that.
See Also: Webinar | The Future of Adaptive Authentication in Financial Services
Besides celebrating Mom, Dad and Star Wars, I'd argue we don't need any more days, thank you very much (see: 7 'Star Wars Day' Cybersecurity Lessons).
But with May 2 rolling around again, nonstop alerts that Thursday is World Password Day are tough to miss.
So here's a pro tip: For everyone who uses an online site or service, every day needs to be a password day. Attackers certainly aren't dormant the other 364 days of the year.
Unfortunately, every year, "correct horse battery staple" password guidance gets trotted out to annoy and confuse users, along the lines of choosing passwords with at least eight characters that include the name of your first llama, the first letters of a phrase you love, plus a few random numbers and symbols.
Password Security: A New Hope
For this year's password day, however, it's important to note that there have been a number of recent changes that make password security easier than ever. I don't mean primarily for users, although they're an important part of the equation.
Rather, Microsoft and others are finally getting their act together when it comes to not forcibly expiring passwords, letting users paste passwords as well as helping to ensure that users don't pick easily guessable - aka pwnable - passwords.
While the onus remains on businesses to better keep users' data - including passwords - secure and enforce minimum password security standards, let's first recap what end users can do to best help themselves. Then we'll move on to what businesses need to do.
So if you want to get all "Hallmark" about it, be sure to pass these tips along to your employees and customers.
First Essential: Keep It Unique
Above all else, the best way to protect your data and privacy - to the extent that you can - is to use a unique password for every site and service. Never, ever reuse a password. Also make sure it's not a commonly used password.
What do those look like? Together with Troy Hunt and his Pwned Password service, the U.K.'s National Cyber Security Center has released a list of the 100,000 most commonly used passwords seen in online breaches. Attackers often employ lists like these to try to brute-force their way into accounts, using email addresses they've obtained from other sources.
Reusing passwords means that if an attacker breaches a site and steals your username and password, they can use it in an attempt to log onto every other site or service you use.

"This is the underlying problem, says Australian password security expert Troy Hunt about credential stuffing. "People have said: 'Hey, I have a favorite password, it's my cat's name and this is the year that it was born; this is fantastic and I'm going to use it everywhere.'"
Such credential stuffing is rife, given its apparent ease and efficacy (see: Credential Stuffing Attacks: How to Combat Reused Passwords).
Second Essential: Use a Password Manager
The best way to be unique is to outsource the job to a password manager.
Sorry, but when it comes to picking a password, extensive research has found that our choices aren't unique enough to block brute-force attacks.
Enter password managers, which not only generate unique passwords, but also store them and quickly retrieve - and allow users to paste them - for every different site or service they use. My password manager has hundreds of entries, from Amazon, eBay and the Guardian to work accounts, pet microchip codes and bicycle padlock combinations.
Password management software runs on PCs and smartphones, meaning you can always carry your passwords with you, securely stored. In some cases, keeping passwords in a book at home - preferably stored in a safe - might also be an option. But it's tough to beat the software.
Third Essential: Activate Second Factors
As Martijn Grooten, editor of Virus Bulletin, has noted, always use a second factor to secure your important accounts.
Numerous sites now offer two-step authentication. Many banks provide one-time passwords via SMS (not great) or authentication apps on smartphones (much better).
Fourth Essential: Businesses Must Do Better
Picking unique passwords remains something that users can do.
But so much of the password security equation relies on businesses handling passwords correctly, avoiding coding errors, offering strong second authentication capabilities and forcing users to reset their passwords if any of this is in doubt, especially after a breach (see: LinkedIn's Password Fail).
Most service providers store passwords as hashes, which are mathematical representations of a plain-text password. Hashes are supposed to be irreversible, meaning that it's not possible to start with a hash and figure out of the real password. Even better is when sites also "salt" the password by adding random data to it before hashing.
Banish MD5 and SHA1
In years past, however, many businesses used hashing algorithms such as MD5 and SHA1, which weren't fit for their purpose, because they're easy to crack and also failed to salt (see: We're So Stupid About Passwords: Ashley Madison Edition).
Thankfully, many have adopted password-hashing algorithms such as bcrypt, which are much more resistant to hash-cracking hardware.
Blacklist Common Passwords
The Pwned Password list gathered by Troy Hunt and published by NCSC gives organizations a way to easily improve the security of any passwords their service users might choose (see: Here Are 306 Million Passwords You Should Never Use).

Pwned Passwords: Top 20
The U.S. National Institute of Standards and Technology, for one, recommends blocking passwords that have previously appeared in breaches, or which might have repetitive or sequential characters or context-specific words.
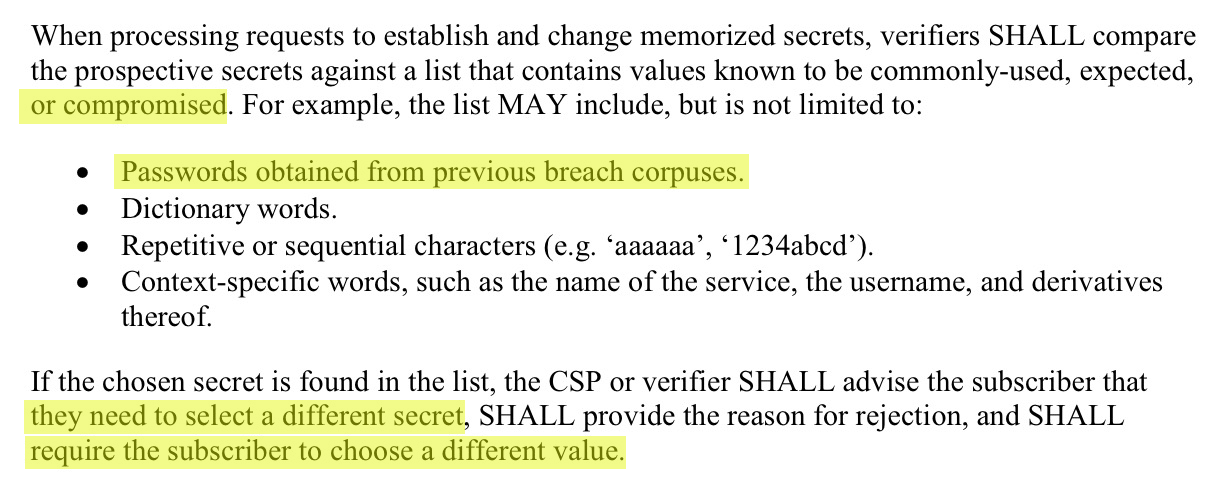
Excerpt from NIST's authentication & lifecycle management document, including Credential Service Provider (CSP) guidance. (Source: Troy Hunt)
Unleash the Power of Pasting
Security experts say sites should never block users' ability to paste usernames and passwords when authenticating. That's because password managers give users this capability, which then speeds up the process of allowing users to both store and use unique passwords.
"Let them paste passwords," the NCSC's "Sacha B." writes in a blog post.
Stop Expiring Passwords
Numerous security experts, including NCSC - part of Britain's GCHQ intelligence agency - also recommend not forcing regular passwords to expire. "It's one of those counterintuitive security scenarios; the more often users are forced to change passwords, the greater the overall vulnerability to attack," NCSC reports.
That's because when users are forced to keep changing passwords, they too often default to something easy to remember, which is typically easy to crack. We humans aren't good at picking properly "unique" passwords (see: Successful Security? Stop Blaming Users).
One password-expiry holdout has been Microsoft, which continues to require that Office 365 passwords get changed every 90 days, and which has recommended that Windows administrators enforce the same.
Microsoft Wakes Up
Finally, however, a reason to celebrate on the occasion of the latest World Password Day: The latest security baseline draft from Microsoft for Windows 10 and Windows Server recommends "dropping the password-expiration policies that require periodic password changes."
Here's why: "Periodic password expiration is an ancient and obsolete mitigation of very low value, and we don't believe it's worthwhile for our baseline to enforce any specific value," Microsoft says.
"By removing it from our baseline rather than recommending a particular value or no expiration, organizations can choose whatever best suits their perceived needs without contradicting our guidance," it adds. "At the same time, we must reiterate that we strongly recommend additional protections even though they cannot be expressed in our baselines."
Office 365 Default: Passwords Don't Expire
Microsoft's latest Office 365 guidance now says the same thing. "By default, passwords are set to never expire," Microsoft tells administrators. "Current research strongly indicates that mandated password changes do more harm than good. They drive users to choose weaker passwords, reuse passwords, or update old passwords in ways that are easily guessed by hackers."
So for any Windows or Office 365 users who remain forced to reset their passwords every 60 days - or whenever - forward Microsoft's policy to your administrator and tell them it's time to reset their approach.



 Red Balloon Security researchers demonstrated their exploit using Cisco's 1001-X enterprise router, but many other devices also have the flaw.
Red Balloon Security researchers demonstrated their exploit using Cisco's 1001-X enterprise router, but many other devices also have the flaw.
 GCHQ Director Jeremy Fleming addresses the CyberUK conference on April 24. (Photo: NCSC)
GCHQ Director Jeremy Fleming addresses the CyberUK conference on April 24. (Photo: NCSC) Ciaran Martin at CyberUK 2019
Ciaran Martin at CyberUK 2019 Scott Jones, head of the Canadian Center for Cyber Security, speaking on a CyberUK panel next to intelligence officials from Australia, New Zealand, the U.K. and U.S., all seated alphabetically by country.
Scott Jones, head of the Canadian Center for Cyber Security, speaking on a CyberUK panel next to intelligence officials from Australia, New Zealand, the U.K. and U.S., all seated alphabetically by country. Paul Chichester, NCSC's director of operations, at CyberUK 2019
Paul Chichester, NCSC's director of operations, at CyberUK 2019

 Pwned Passwords: Top 20
Pwned Passwords: Top 20 Excerpt from NIST's authentication & lifecycle management document, including Credential Service Provider (CSP) guidance. (Source: Troy Hunt)
Excerpt from NIST's authentication & lifecycle management document, including Credential Service Provider (CSP) guidance. (Source: Troy Hunt) Image copyright
Getty Images
Image copyright
Getty Images
