Application Security , Breach Response , Data Breach
Vulnerability Highlights Poor Security Controls for Passenger Name Records(jeremy_kirk) • January 17, 2019 An El Al Boeing 767-3Y0/ER. (Photo: Magic Aviation via Wikimedia Commons/CC)
An El Al Boeing 767-3Y0/ER. (Photo: Magic Aviation via Wikimedia Commons/CC)An investigation is underway into a booking software vulnerability that exposed airline passenger name records, which is a bundle of personal and travel data that gets collected whenever someone books a flight.
See Also: Live Webinar: Building Secure Delivery Pipelines with Docker, Kubernetes, and Trend Micro
Security researcher Noam Rotem discovered the flaw on Israeli airline El Al's website. El Al uses a booking system from Amadeus, a Madrid-based company based that works with 500 airlines, including United Airlines and Air Canada.
"We are conducting a thorough internal review and detailed investigation into the root cause and impact of this issue and will be working hand-in-hand with those customers affected," Amadeus says.
In an update on the incident, Amadeus says on Thursday that it "has not detected any data breach and that no data from travelers was disclosed. We regret any disruption this situation may have caused."
A passenger name record - PNR - comprises a collected bundle of personal and travel information that gets transferred between countries for law enforcement and customs purposes. A PNR includes name, itinerary, email and postal addresses, destination and seat and meal preferences.
Airlines typically issue a six-digit alphanumeric booking reference code whenever someone books their ticket. When combined with a passenger's last name, this code, which is sometimes referred to as a PNR locator, is enough to access the individual's travel record via the airline's website.
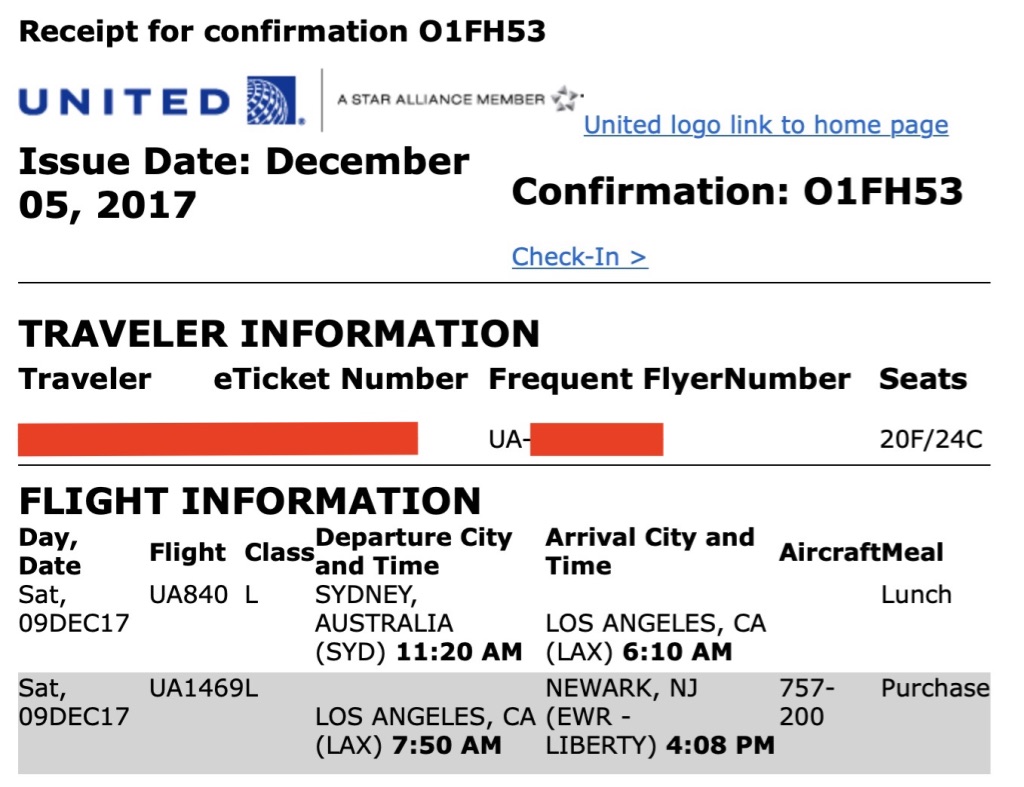 In this example, "O1FH53" is the booking reference code or PNR locator.
In this example, "O1FH53" is the booking reference code or PNR locator.The reference is also encoded in a ticket's barcode as well as on baggage tags, which security experts have noted essentially makes it a public passcode. Although many security experts have criticized the current PNR system as being inadequate, it remains in place.
Passenger Data Exposure
Rotem, who works at the security company Safety Detective, discovered the flaw in El Al's website while booking his own flight, according to a blog post from the company.
El Al sends customers a link to a web page to check their PNR. But Rotem discovered that he could insert a random booking reference number into the link. After inputting the number, Rotem then obtained a random PNR, which exposed a passenger's data.
With that information in hand, it's possible to access someone else's booking information using the booking reference number and the last name of a passenger. From there, an attacker could change meal preferences and seats, fraudulently claim frequent flyer miles, update email addresses and phone numbers and cancel flights.
Even worse, Rotem found that there were no brute-force or rate-limit protections for such requests. That would allow an attacker to code a script that rapidly cycles through potential booking reference numbers in the hopes of getting a hit.
Rotem says he alerted El Al's CISO to the flaw on Wednesday.
In response, Amadeus says its technical team took immediate action and that it is working with customers. The company noted that the airline industry relies on standards developed by the International Air Transport Association, in an apparent allusion to there being bigger problems with PNRs, which are beyond its ability to fix outright.
"Because the industry works on common industry standards, including the PNR, further improvements should include reviewing and changing some of the industry standards themselves, which will require industry collaboration," Amadeus says.
Authentication Revamp Needed
The security around PNRs was the subject of a presentation by researchers Karsten Nohl and Nemanja Nikodijevic at the Chaos Communication Conference in Germany in December 2016.
Global distribution systems, such as the one run by Amadeus and other booking software providers, including Sabre and Travelport, date back decades. But their software has been woven into web services that lack proper security controls, according to a summary of Nohl and Nikodijevic's research.
A big problem remains weak authentication.
"The most important security feature lacking from all three GDSs is a proper way to authenticate travellers," the researchers write. "While the rest of the internet is debating which second and third factors to use, GDSs do not offer a first authentication factor. Instead, the booking code (aka PNR Locator, a 6-digit alphanumeric string such as 8EI29V) is used to access and change travelers' information."
The researchers also highlighted the very same issue found by Rotem in the Amadeu system: a lack of brute-force protection.
"The way 6-digit booking codes are chosen makes them weaker than a 5-digit password (
In the short term, Nohl and Nikodijevic recommended airlines employ Captchas and also limit the number of requests per IP address. Longer term, however, PNRs need better authentication protection, which could include giving customers the ability to set their own passwords, they write.

