Endpoint Security , Hardware / Chip-level Security , Internet of Things Security
Vulnerabilities Found in APIs Controlling Croatia-Based Zipato's IoT Devices(jeremy_kirk) • July 4, 2019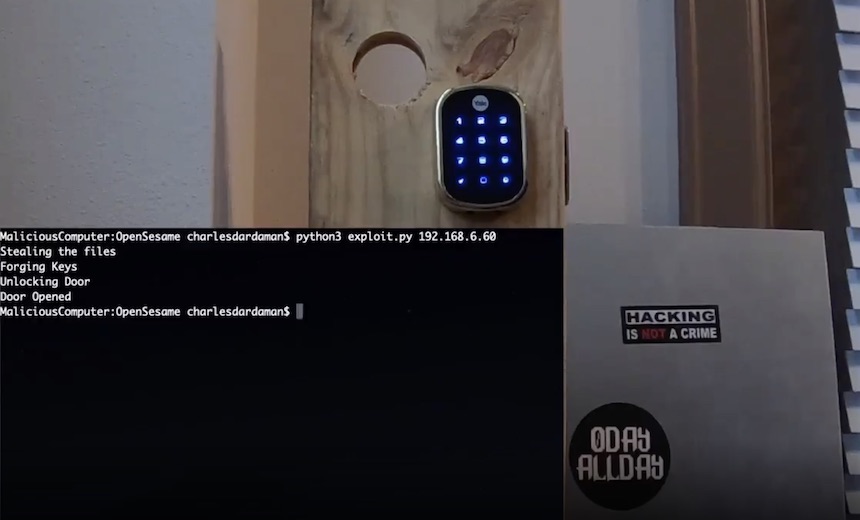 Researchers with Black Marble found three vulnerabilities in Zipato's smart hubs that could be exploited to unlock doors. (Source: Black Marble)
Researchers with Black Marble found three vulnerabilities in Zipato's smart hubs that could be exploited to unlock doors. (Source: Black Marble)Findings from researchers who hacked smart hub controllers used to manage networked locks, lights and security cameras underscore the risks that can accompany home networking and automation devices.
See Also: 10 Incredible Ways You Can Be Hacked Through Email & How To Stop The Bad Guys
Researchers Chase Dardaman and his colleague, INIT_6, of consultancy Black Marble, reported finding three vulnerabilities in two smart hubs made by Zagreb, Croatia-based Zipato, which develops smart home products.
The proliferation of smart home devices promises a new level of convenience for consumers, and in theory also security. But time and time again, researchers have found software problems that appear to have been baked-in during development that can make such devices easy pickings for hackers.
From Locked to Unlocked
The Black Marble researchers report that the flaws they found could be exploited either locally or remotely, and perhaps for some unlucky users, even be used to unlock their front door. The researchers say they reported the vulnerabilities to Zipato in March, and that they were fixed later that month.
On Tuesday, Black Marble released its technical findings . The affected smart hubs are Zipato's ZM.ZWUS ZipaMicro Z-Wave controller and the 2AAU7-ZBZWUS Zipabox Z-Wave controller.
 The ZipaMicro controller. (Source: Zipato)
The ZipaMicro controller. (Source: Zipato)Dardaman and INIT_6 write that they set out to see if they could unlock a door remotely without prior access. Also, they wanted to see if they could take data off a single controller that could be leveraged to open other doors in, for example, a complex that had deployed the system. Lastly, they sought to search for a vulnerability that might allow for unlocking a door if they were on the same network as the controller.
Their score? Two out of three, and they write that given enough time, all three might be possible.
 Black Marble's summary of the vulnerabilities they found in Zipato controllers
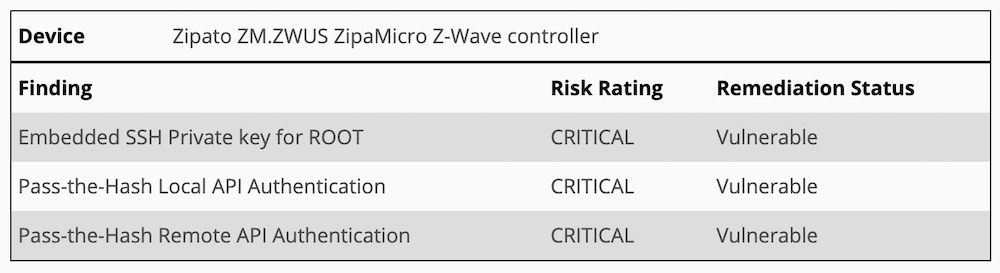
Black Marble's summary of the vulnerabilities they found in Zipato controllersThey managed to retrieve a hardcoded SSH private key (CVE-2019-9560) in the controllers. By removing and then imaging an SD card from the controller, they were able to extract the private key, which was needed for root access.
The private key was stored in a password-protected folder called /etc/dropbear and named dropbear_rsa_host_key. But they were still able to extract it despite it being password-protected.
That SSH key isn't unique, either, so it could be reused across other controllers. In a short video, they show how it is possible to use the vulnerabilities to unlock a Yale lock linked to the controller.
Remote API Attack
The researchers also discovered a local API authentication problem. They found a SHA1 password hash, and because the controller uses the pass-the-hash method rather than requiring the credentials to be input, they were able to construct a working authentication request. After that, they say it would be possible to send an authenticated request to unlock a lock.
The same attack is possible via the remote API as well. Using Shodan.io to search for internet-connected controllers, Black Marble says it spotted at least five. It's not clear if further refining Shodan searches might reveal more such devices.
Zipato says it has 112,000 devices in 20,000 households across 89 countries. It's not clear how many of those might be smart hub controllers.
As for the remote API vulnerability, the researchers write that "depending on the Zipato implementation it could be possible to control all the ZipatoMicro devices."
INIT_6 writes on Twitter that if an attacker was able to get access to the local network, the person could then use the SSH key to log into the controller.
INIT_6 also writes that the controllers contained three sets of credentials, designed for apartment owners and managers and their tenants. The credentials could be used in an attack in combination with passing the hash to get access to all devices on a network.
TechCrunch reports that Zipato's Chief Executive Sebastian Popovic says that its controllers will now have unique SSH keys plus other security improvements, and that his company has discontinued the ZipaMicro hub.
Does that fully address the flaws that were discovered? Zipato, in an email to the researchers that they published, says it disabled vulnerable functionality the same day it received the vulnerability alert, and that it had begun automatically updating the firmware on all affected devices.
But the researchers warn that at least some of the underlying flaws might still be present. "Passing-the-hash is still an issue if you can find the password hash," they write.

