Cybercrime as-a-service , Endpoint Security , Fraud Management & Cybercrime
City's IT Department Continuing Recovery Work(@Ferguson_Writes) • June 7, 2019
A month after Baltimore's IT system was hit with ransomware, local officials expect the attack to cost the city $18 million in recovery costs and lost revenue, although that number could increase in the coming months as systems are brought back online and a federal investigation continues.
See Also: Webinar | The Future of Adaptive Authentication in Financial Services
At a press conference this week, City Finance Director Henry Raymond offered some preliminary details about the cost to the city so far. In his estimate, Baltimore has spent about $10 million in recovery and forensic expenses, and the city is expected to lose about $8 million in revenue.
"While far from ideal, this situation and its impact have been manageable," Raymond said during the June 4 press conference, adding he did not see the attack having a material impact on the city's 2020 municipal budget, which officially starts July 1. He did leave open the possibility, however, that the situation could cost more as the recovery continues.
The May 7 ransomware attack, which used malicious crypto-locking code, affected about 10,000 computers within the city's network. Sheryl Goldstein, deputy chief of staff for operations who is overseeing the recover for the Baltimore mayor's office, said during Tuesday's press conference that the IT department is working on re-authenticating user accounts with new usernames and passwords. She expected that work to be 90 percent complete by the end of this week.
While police, fire and other essential services are still functioning, the city is still having trouble accessing systems that control parking and traffic violations. as well as billing cycle for the water department. Other parts of the local government are being run with paper and pencil until IT services and back-up data are restored.
In addition to the recovery and forensic work, the attack remains under investigation by the FBI, and a final report is likely to be completed within the next month, Goldstein said.
RobbinHood
Almost immediately after the attack, city officials announced that Baltimore had been hit with RobbinHood, a relatively new variant of ransomware that has been showing up in various incidents since the beginning of the year and mainly targeting municipalities, such as Greenville, North Carolina (see: Baltimore Recovering From Second Ransomware Attack).
Not much is known about the person or persons behind RobbinHood, although some security researchers note that it mimics the SamSam extortion method, but uses a different payload and server-side attack. Vitali Kremez, a cybercrime researcher who has reverse engineered the malware, previously noted that RobbinHood will stop 181 Windows services, including anti-virus, database, mail server and others that could keep files open and prevent their encryption. The ransomware also disconnects all network shares, which allows the attacker to target individual machines.
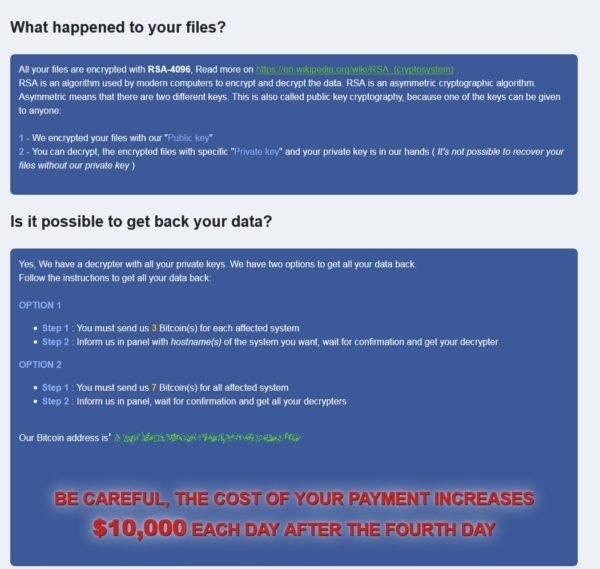 RobbinHood ransom note (Image: MalwareBytes)
RobbinHood ransom note (Image: MalwareBytes)"Most analysis of this ransomware doesn't really show anything special about it, compared with other ransomware families we've seen over the last few years," Adam Kujawa director of Malwarebytes Labs, tells Information Security Media Group. "The reason we keep seeing it may be due to the actors behind it, likely having developed it themselves - or created it from source code from other ransomware families - focusing on targets that get a lot more attention in the media."
Paying Up or Not
As part of the original ransom, the attackers asked for 13 bitcoins, or about $100,000 under current prices, to unencrypt all the Baltimore files and data. The attackers also taunted city officials through a now shuttered Twitter account.
Baltimore Mayor Bernard C. "Jack" Young has refused to pay and had published a video justifying his reasons to the public.
During the city's press conference, Young and other officials noted that the FBI requested that Baltimore not pay, but Kujawa believes that not paying isn't always the right answer. He believes the best method is to remediate the situations quickly, but if this can't be done, it might be easier and more cost effective to negotiate.
The key is having a plan in place long before the attack happens.
"This is something the cybercriminals don't want you to do, they want you to react and pay rather than consider your options," Kujawa says. "However, if you have some kind of plan in place beforehand, like a policy on paying ransom, which has been discussed between city leaders and their security staff, then the shock of coming to work to find all the systems ransomed is slightly less stressful because you've got a plan in place."
EternalBlue or Something New?
In addition to the updates from city government, several reports published this week, including one on Krebs on Security, question whether the Baltimore ransomware attack was the result of the EternalBlue vulnerability still found in many Windows devices (see: Baltimore Ransomware Attack Triggers Blame Game).
In May, The New York Times reported that the RobbinHood attackers used the EternalBlue vulnerability, which had been developed by the U.S. National Security Agency and then leaked online by a group called the ShadowBrokers. Since then, attackers have used exploits to take advantage of this vulnerability to spread ransomware, including WannaCry (see: After 2 Years, WannaCry Remains a Threat).
Some argued that the federal government needs to take responsibility for the types of attacks affecting Baltimore and other cities since the NSA developed the exploits. However, Joe Stewart, a malware analyst who consults with security firm Armor, told Krebs and other publications that malware used in the Baltimore attack does not contain any Eternal Blue exploit code.
In his analysis, Kujawa also believes that EternalBlue was not used against Baltimore, but that a spear phishing attack focused on city employees is the likely initial infection point. After that, the attackers could move laterally through the network by manipulating Microsoft's PSExec, a legitimate administrator tool, before looking for files to encrypt.
Local Governments Under Attack
What the Baltimore incident does show is that cities and local municipalities are increasingly under attack by ransomware. In May, security firm Recorded Future released a study that found 53 different ransomware attacks targeting local governments in 2018, and at least 21 separate incidents this year so far (see: Ransomware Increasingly Hits State and Local Governments).
The reasons why attackers are targeting local governments vary, but Kujawa, who recently blogged about the issue, believes that these attackers take advantage of whatever opportunities present themselves.
"The attacks will absolutely continue" Kujawa tells ISMG. "Cybercriminals go after attacks of opportunity more than anything else, meaning that it may not have been a direct effort to infect Baltimore, but after spreading X amount of e-mails to [dot] gov addresses, somebody took the bait. As such, this is going to happen again, as long as there are networks vulnerable to attack, either via system holes or user error."

