 Verifications.io remains offline since it was informed that it had internet-exposed 763 million records. (Source: Internet Archive)
Verifications.io remains offline since it was informed that it had internet-exposed 763 million records. (Source: Internet Archive)Verifications.io, a self-described "big data email verification platform," has suffered a data breach exposing some 763 million records.
See Also: Live Webinar | Passwords: Here Today, Gone Tomorrow? Be Careful What You Wish For.
The breach was discovered by security researcher Bob Diachenko, who worked with fellow researcher Vinny Troia to count the number of exposed records and identify who was exposing them. They say the trail quickly led them to Verifications.io, a site that offers an "enterprise email validation" service.
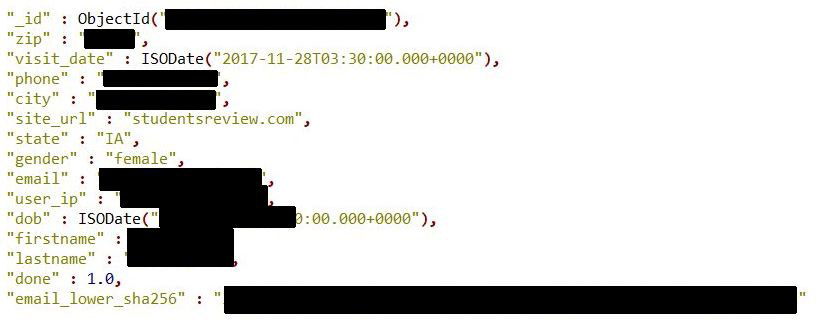 Source: Bob Diachenko
Source: Bob DiachenkoExposed data across 763 million records included email address, name, gender, IP address, phone number and other personal information, Diachenko reports.
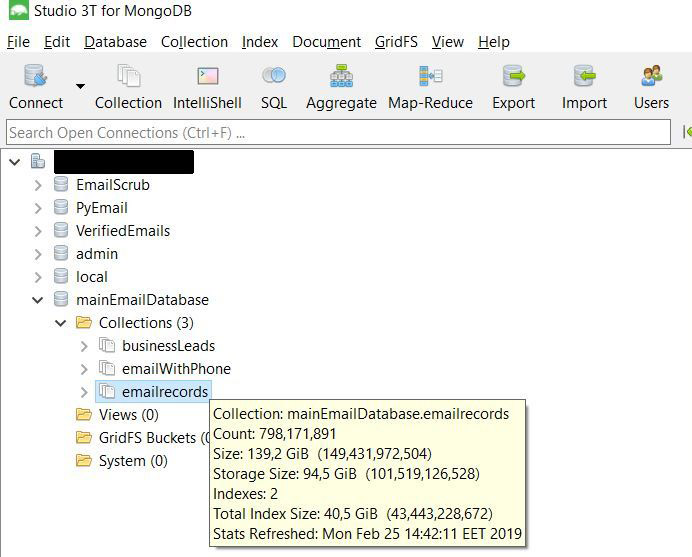 Source: Bob Diachenko
Source: Bob Diachenko
"On Feb. 25, I discovered a non-password protected 150 GB-sized MongoDB instance," Diachenko writes in a Thursday blog post. "This is perhaps the biggest and most comprehensive email database I have ever reported. Upon verification, I was shocked at the massive number of emails that were publicly accessible for anyone with an internet connection. Some of data was much more detailed than just the email address and included personally identifiable information."
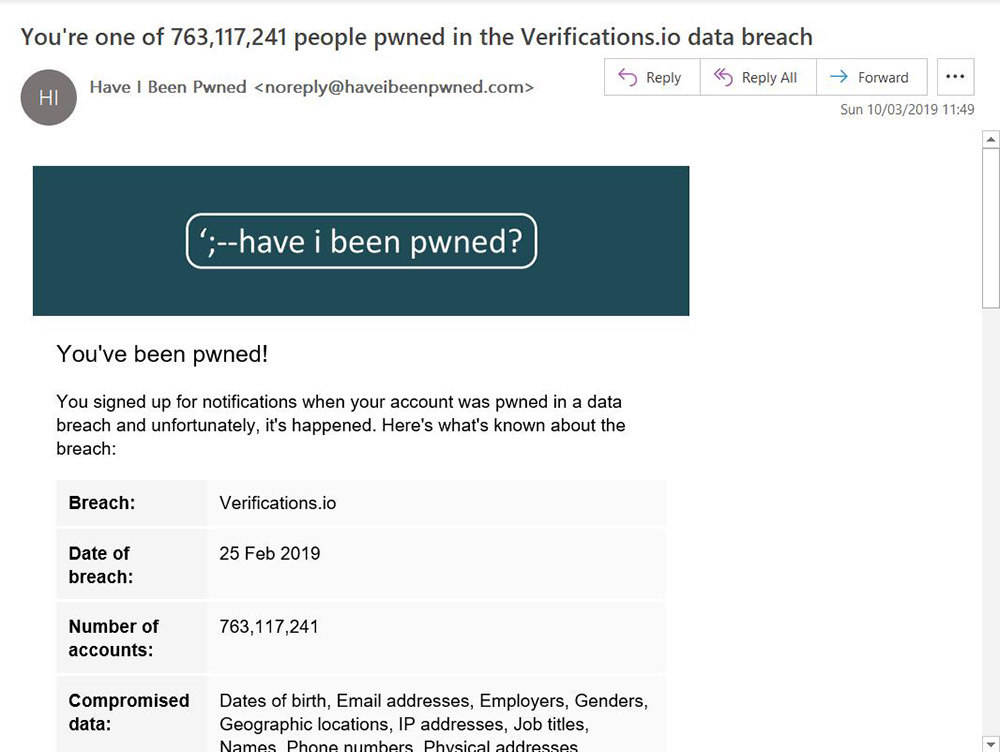
On Sunday, Have I Been Pwned, a free breach notification service, began warning subscribers about the breach. The service allows individuals to register their email address and then receive an alert to that address whenever it appears in a data dump.
Troy Hunt, who runs Have I Been Pwned, says the leak appears to be the second largest breach in history and the biggest-ever leak of data that traces back to a single source, rather than a compilation of credentials from multiple sources. Hunt says that 66 percent of the email addresses exposed in the breach had already appeared in a previous breach logged by Hunt's notification service.
The largest known data breach in history involved the massive collection of breached data, known as "Collection #1," that came to light in January (see Data Breach Collection Contains 773 Million Unique Emails).
Diachenko says the information he discovered in the exposed MongoDB instance does not appear to have been culled from previous data breaches. "As part of the verification process I cross-checked a random selection of records with Troy Hunt's HaveIBeenPwned database," he says. "Based on the results, I came to the conclusion that this is not just another 'collection' of previously leaked sources but a completely unique set of data. Although not all records contained the detailed profile information about the email owner, a large amount of records were very detailed. We are still talking about millions of records. "
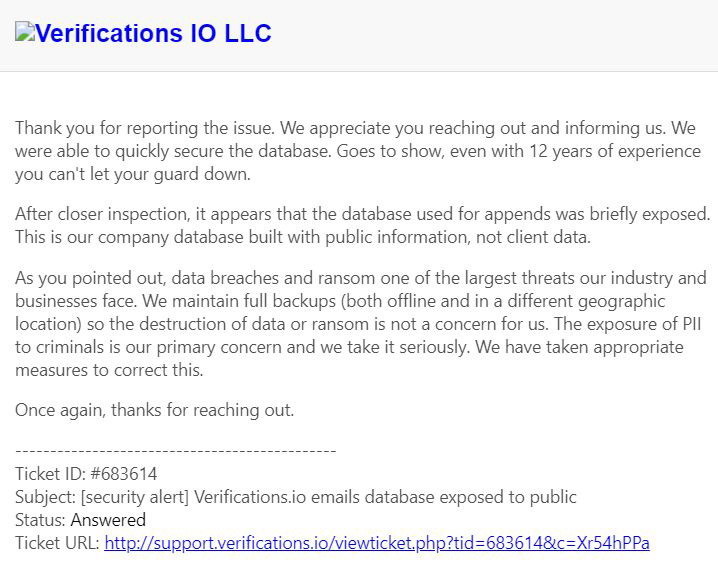
Diachenko says he alerted Verifications.io to the exposed MongoDB instance, and that the company confirmed the problem and said it had been mitigated the same day it received his warning. The company also claims that the information it was storing had been amassed from public sources.
 Source: Bob Diachenko
Source: Bob DiachenkoVerifications.io's website says the company is based in Tallinn, Estonia. Some of the company's press releases, however, suggest it is based in Boca Raton, Florida.
Regardless, the site has remained offline since March 4, Wired reports.
Diachenko says the Verifications site appeared to allow users to validate targets' email addresses. He said this could have been abused by threat actors to help refine their phishing or brute-force attack campaigns.
"The database(s) included email accounts they use for sending mail as well as hundreds of SMTP servers, email, spam traps, keywords to avoid, IP addresses to blacklist and more," he said. "This is why I initially thought they were potentially engaged in spam-related activities. It turns out that technically they actually are sending unwanted and unsolicited emails. This is the worst kind of spam because they send millions of completely worthless 'hello' emails that no one can understand."
Verifications.io didn't immediately respond to a request for comment.
Searching for Sources
The company's website says its service is designed to "remove abuse and improve ROI [return on investment] on email campaigns."
Hunt and other security experts, including Alan Woodward, a professor of computer science at the University of Surrey, have noted that it's not clear how Verifications.io amassed all of this data.
But some breach victims have begun offering clues. Developer Mark Holmes shared a list of where he'd used "bait email addresses" - meaning accounts created to use on low-value sites, potentially to help trace a breach when it occurs - that appeared in the breach.
"Interesting to see which of my bait email addresses made it into http://verifications.io breach: Macromedia, Domain registration (I use GoDaddy, http://Register.com ), Deluxe Check company, LinkedIn, TechNet Magazine, and what has to be a random spammer," he tweeted.
Hunt's Have I Been Pwned service, meanwhile, is fast becoming a service that tracks not just if someone's credentials have been exposed, but how many times. Hunt, for one, says Verifications.io triggered the 17th breach alert he's received from his own service.
Another measure of the problem: The Verifications.io breach takes the count of all records that have known to have been breached in history to a new, record high. In fact, the number is so large that it now exceeds the world's population.

