Endpoint Security , Fraud Management & Cybercrime , Ransomware
Crypto-Locking Extortion Targets Internet-Exposed D-Link Devices(euroinfosec) • March 15, 2019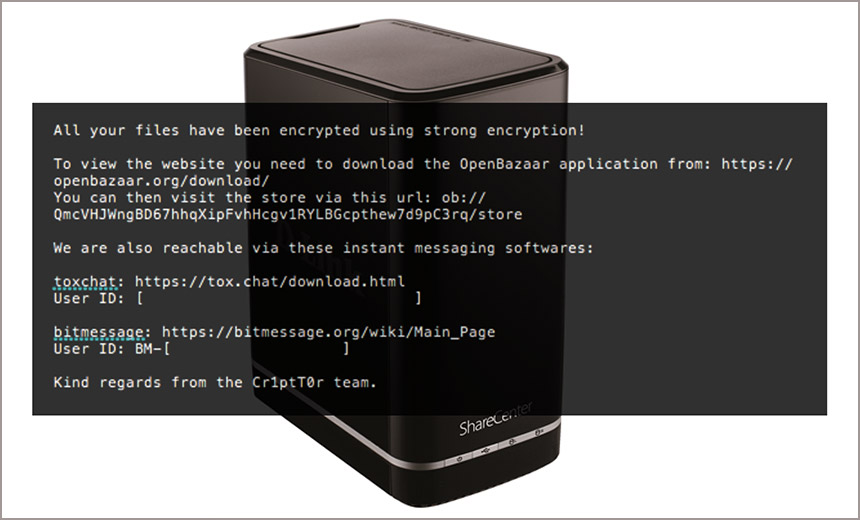 Internet-connected D-Link devices, including network-attached-storage enclosures, are being crypto-locked by Cr1ptT0r ransomware. (Sources: Coveware, D-Link)
Internet-connected D-Link devices, including network-attached-storage enclosures, are being crypto-locked by Cr1ptT0r ransomware. (Sources: Coveware, D-Link)Criminals wielding a new strain of ransomware called Cr1ptT0r are targeting network-attached storage users.
See Also: Webinar | The Future of Adaptive Authentication in Financial Services
The NAS-targeting ransomware campaign was first discovered in February after owners of D-Link DNS-320 network storage enclosures took to the forums of Bleeping Computer to report that their devices had been crypto-locked.
As the publication reported, while D-Link still supports the two-bay NAS product, the vendor last issued a firmware update in 2016 to fix a known security flaw. Older versions of the firmware have a hard-coded backdoor attackers can use to remotely access the device.
Sensing a business opportunity, attackers wielding Cr1ptT0r ransomware have come calling. Services such as Shodan allow would-be attackers to search for internet-connected devices that may sport known vulnerabilities, then target them directly (see: Hacked MicroTik Routers Serve Cryptocurrency-Mining Malware).
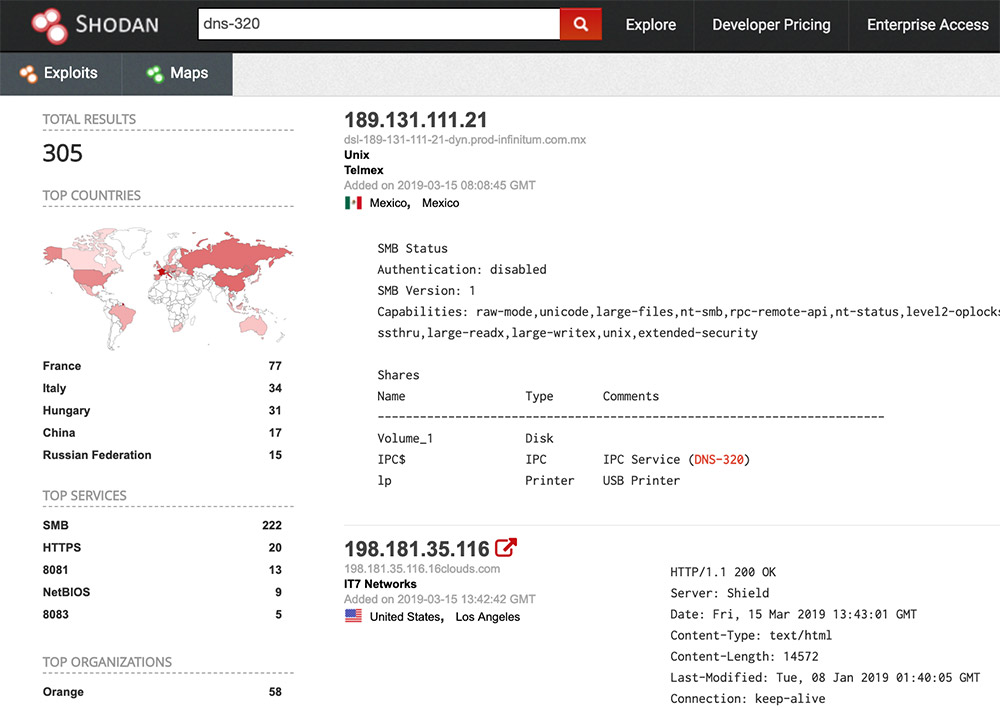 A basic Shodan search for internet-connected devices returns header information that includes "DNS-320," which is just one type of network attached storage device being targeted by attackers with Cr1ptT0r ransomware.
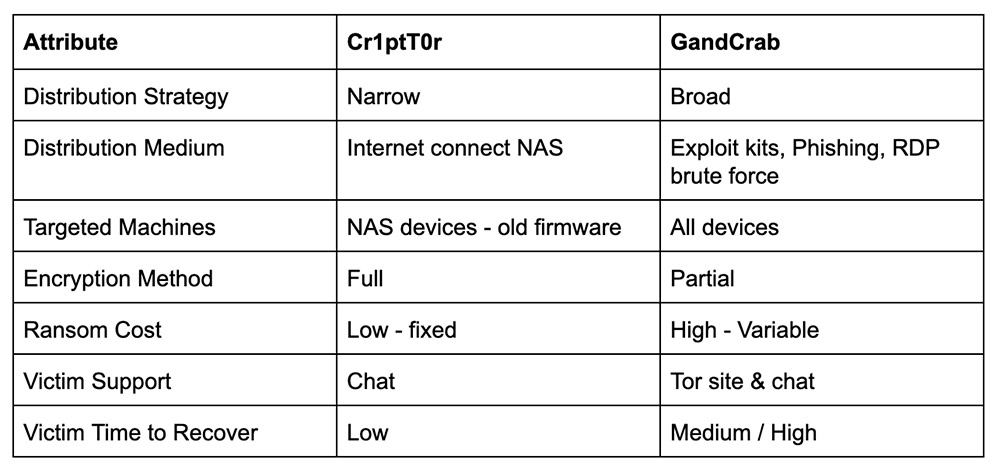
A basic Shodan search for internet-connected devices returns header information that includes "DNS-320," which is just one type of network attached storage device being targeted by attackers with Cr1ptT0r ransomware."While it is common for NAS devices to get swept up in a ransomware attack, Cr1ptT0r is unique in that the distributors have limited their attacks to just NAS devices," ransomware incident response firm Coveware says in a research report. "The distribution strategy stands in stark contrast to broadly distributed ransomware like GandCrab, where the developers appear to be focused on becoming the most prevalent strain of ransomware."
The GandCrab operation focuses on volume, partnering with malware-distribution gangs and giving the "affiliates" who infect victims a customized version of the crypto-locking code, then guaranteeing that for every victim who pays a ransom, the affiliate will receive a portion of the payment.
 Source: Coveware
Source: CovewareGandCrab victims must go to a TOR site to pay - in bitcoin or dash cryptocurrency - and receive a decryption tool. "The GandCrab TOR site is very reliable and delivers a decryptor tool if you pay," Coveware said in a recent research report.
For Cr1ptT0r, the business plan seems to focus not on volume but rather targeted attacks and one-size-fits-all simplicity.
"The developers of Cr1ptT0r are ... constraining distribution to a single device type, standardizing the extortion payment process - fixed prices for a device or a file - and keeping the decryption simple to minimize their support costs," Coveware says.
The Cr1ptT0r gang is targeting a number of types of D-Link devices that are connected to the internet in a manner that is not secure and that have known vulnerabilities or do not sport the latest firmware or security patches, Coveware CEO Bill Siegel tells Information Security Media Group.
D-Link did not immediately respond to a request for comment.
Gang Won't Negotiate
Coveware says the Cr1ptT0r gang does not negotiate with victims - a time-saving process for attackers that saves them money in support costs (see: Ransomware Gangs Take 'Customer Service' Approach). Instead, the price to decrypt a device infected by Cr1ptT0r is set at a fixed $1,200, Coveware says, which is relatively low (see: Ransomware Victims Who Pay Cough Up $6,733 - on Average). Or victims can select à la carte pricing, at $19.99 per file.
Victims who pay the ransom must provide the Cr1ptT0r operator with the type and firmware version of their device. Then they receive a script to run to decrypt the files on their device, Coveware says, noting that restoration can take a long time. That's because unlike other ransomware, Cr1ptT0r is designed to encrypt absolutely everything on a device - everything, that is, except for the ransom note it leaves as well as a text file that adds a line to log every file on the device that it's encrypted until the final line reads "done."
No Free Decryptor
Coveware is part of the No More Ransom initiative, which provides free decryptors for many strains of ransomware. Thanks in no small part to security firm Bitdefender and Romanian Police, last month, No More Ransom released a free decryptor for many versions of GandCrab (see: Police Push Free Decryptor for GandCrab Ransomware).
Unfortunately, so far there's no free decryptor for Cr1ptT0r ransomware.
If victims are not using their NAS as their sole backup or supplemental storage device, they they can simply wipe the device and start over.
"If you are affected by Cr1ptT0r, at a minimum you should back up the data, format the drive and update the device," Coveware says. "Victims should not leave NAS devices open to the internet. Also, it should be noted that NAS devices that are not properly partitioned should not be used as backup devices. If there are no other options for recovering your data, paying the ransom should be the absolute last option."
Victims who do choose to pay, however, appear to be getting their data back.
"They [the attackers] are using full disk encryption, so while it is time consuming to decrypt, the keys provided work without damaging files," Coveware's Siegel says. "This is in contrast to a lot of branded ransomware, like Dharma and Ryuk, where the encryption process is very heavy and often corrupts certain files types and operating systems, leaving data recovery - even with a decryptor tool - impossible."
Essential Defenses
Coveware says that any business using NAS should ensure that at a minimum, they never directly expose any NAS device to the internet.
One way to restrict access is to first require users to access the network on which the NAS is sitting, for example, by using a remote desktop protocol connection.
Attackers, however, don't shy away from exploiting organizations via RDP, either by brute-forcing their way in or buying stolen credentials via cybercrime markets (see: Stolen RDP Credentials Live On After xDedic Takedown).
Recently published research from Coveware found that when ransomware victims were able to pinpoint the source of their infection, 85 percent traced it to RDP, 14 percent to phishing and 2 percent to another form of social engineering.
Coveware says organizations that allow access to their network via RDP should:
Change defaults: Change the default RDP port setting from 3389 to make it tougher for attackers to find. Whitelist access: Only allow a specified range of IP addresses - that need access - to have access. Use password lockouts: Set a lockout any time a remote user fails to log in after a small number of attempts to help block brute-force password-guessing attacks. Require VPN: Restrict RDP access to specified VPN connections. Employ multifactor: Make strong, two-factor authentication mandatory for anyone who wants to access a NAS via RDP.
