Cybercrime , Cybercrime as-a-service , Fraud
Offerings Abound on Darknet Forums; The Dark Overlord Seeks Multilingual Hackers(euroinfosec) • January 14, 2019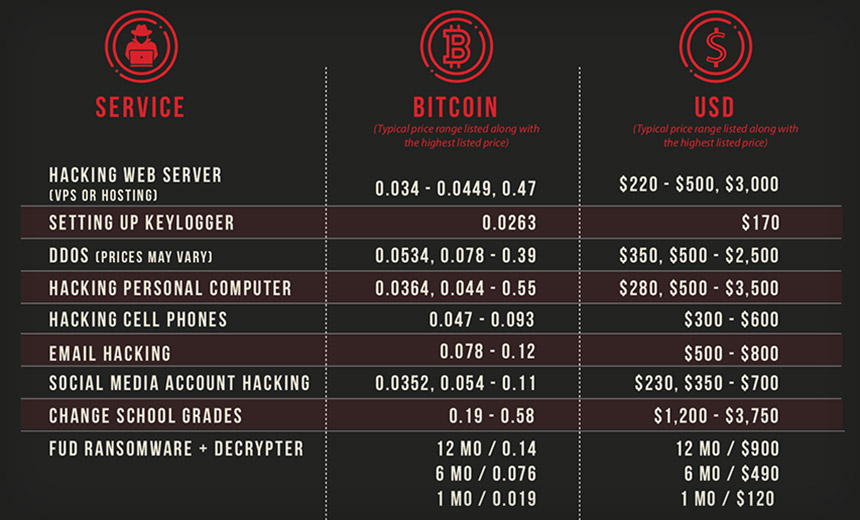 Prices for services on a major darknet cybercrime forum, including for "fully undetectable" ransomware, found in October 2018, reflecting exchange rates in effect at that time (Source: WatchGuard)
Prices for services on a major darknet cybercrime forum, including for "fully undetectable" ransomware, found in October 2018, reflecting exchange rates in effect at that time (Source: WatchGuard)Calling all hackers for hire: Do you have what it takes to send "violent and graphic" emails and text messages to schoolchildren's parents, blackmail healthcare organizations, manufacturers, technology companies and law firms, or leak unaired episodes of "Orange is the New Black," preferably while also being fluent in Arabic, Chinese or German?
See Also: Live Webinar: Building Secure Delivery Pipelines with Docker, Kubernetes, and Trend Micro
Or in the words of a November 2018 job offering from the international hacking group that calls itself The Dark Overlord: "Do YOU want to get Rich? Come work for us!"
The Dark Overlord is a notorious online extortion gang that regularly steals data and then attempts to ransom it back to victims. Anyone who doesn't comply gets threatened with the full data set being leaked, with the group often trying to increase the pressure on victims by trickling out the stolen data (see: Ransom Moves: The Dark Overlord Keeps Pressuring Victims).
The gang is one of innumerable cybercrime players that continue to use darknet forums to seek fresh recruits, sell stolen data, advertise hacking services, or some combination thereof. Darknet - or dark web - sites refer to ".onion" websites that can only be reached via the anonymizing browser known as Tor, which can confer a degree of anonymity on buyers and sellers, especially if they also use pseudonymizing cryptocurrencies, such as monero, to complete their transactions.
Apparently, The Dark Overlord has also been using a darknet forum as part of a hiring campaign. As CyberScoop first reported, the job advertisement was spotted by cybersecurity firm Digital Shadows on KickAss Forum, a paid, members-only dark web cybercrime forum and marketplace. A supposed representative for The Dark Overlord first appeared on the forum in September 2018, when the group used KickAss to announce the launch of its "dark web sales campaign" for stolen data and information.
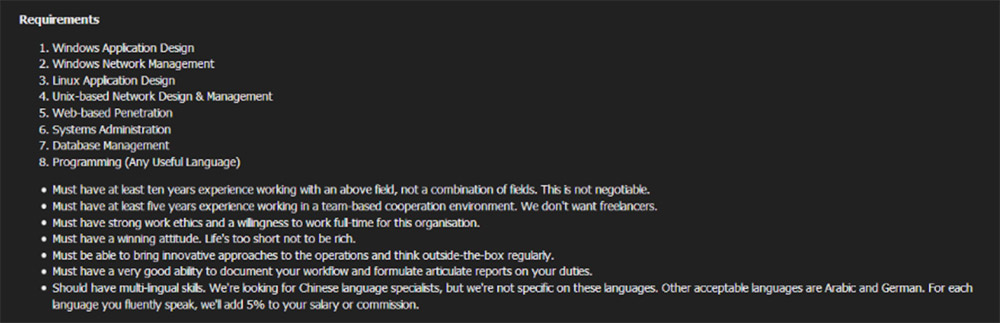
The Dark Overlord's November 2018 job advertisement said it was looking for four individuals who had at least 10 years of experience in a specified area, including Windows application design, Windows network management, Linux application design, systems administration or "programming (any useful languages)," according to a copy of the job advertisement Digital Shadows found.
Desirable Knowledge: Network Administration, Programming
"Must have at least 10 years experience working with an above field, not a combination of fields. This is not negotiable," the job advertisement reads. "Must have at least five years experience working in a team-based cooperation environment. We don't want freelancers. Must have strong work ethics and a willingness to work full-time for this organization. Must have a winning attitude. Life's too short not to be rich. Must be able to bring innovative approaches to the operations and think out-the-box regularly. Must have a very good ability to document your workflow and formulate articulate reports on your duties."
In return, the hacking group offered to pay new, full-time employees a monthly salary of £50,000 ($64,500), likely rising to £70,000 ($90,000) after two years, CyberScoop reported.
Candidates with multilingual skills were desirable, with The Dark Overlord offering to "add 5 percent to your salary or commission" for fluency in every additional language, with Chinese, as well as Arabic and German, being especially desirable.
"Must have a winning attitude," the advertisement reads.
 Source: Digital Shadows
Source: Digital ShadowsOf course, what the job advertisement doesn't say is that The Dark Overlord may be advertising for additional members owing to law enforcement agencies putting more pressure on the group, including arresting at least one suspected member and another alleged accomplice, all of which may have had an effect on the hacking group's employee retention rates (see: Noose Tightens Around Dark Overlord Hacking Group).
Needed: 'Local Advertising'
The Dark Overlord is recruiting for relatively experienced individuals seeking a life of cybercrime.
 In Russia and Ukraine, "many city blocks are covered with Telegram channel names and internet drug store titles, mostly understood only by the younger generation," SpiderLabs says.
In Russia and Ukraine, "many city blocks are covered with Telegram channel names and internet drug store titles, mostly understood only by the younger generation," SpiderLabs says.But not all of the job market is so specialized. Other positions being advertised on darknet forums are for individuals seeking "easy money" for disseminating "local advertising," which may include spray-painting Telegram - an encrypted messaging application - channel names for internet drug stores, according to an October 2018 report from Trustwave's SpiderLabs Research group.
Other menial jobs being advertised online include "data entry clerks" and "captcha solvers" able to handle the laborious task of registering for different online forums or services.
Such jobs can be lucrative, especially for students. In Ukraine, the minimum wage is about $140 a month, and the highest scholarship a university student could receive is about $63 per month, compared to many of these jobs promising to pay $15 per day, SpiderLabs says. "Within one work week, a student could earn more than a scholarship, and within two weeks more than a full month's salary at minimum wage - a very appealing offer for a part-time job," it says.
Desperately Seeking Droppers, Money Mules
Beyond the entry-level jobs, other cybercrime positions are also available.
For individuals who lack technical expertise but are willing to risk their physical security, a range of advertisements seek "cashouts" - aka money mules, ATM fillers - who are willing to use cloned ATM cards or interact with malware-infected ATMs to cash them out, in return for a percentage of the proceeds, SpiderLabs says.
Advertisements also regularly seek international "droppers," who are individuals willing to receive stolen goods or money and send it elsewhere to help disguise the flow of fraudulent goods and funds, SpiderLabs reports. Employees who work for the postal service appear to be especially desirable.
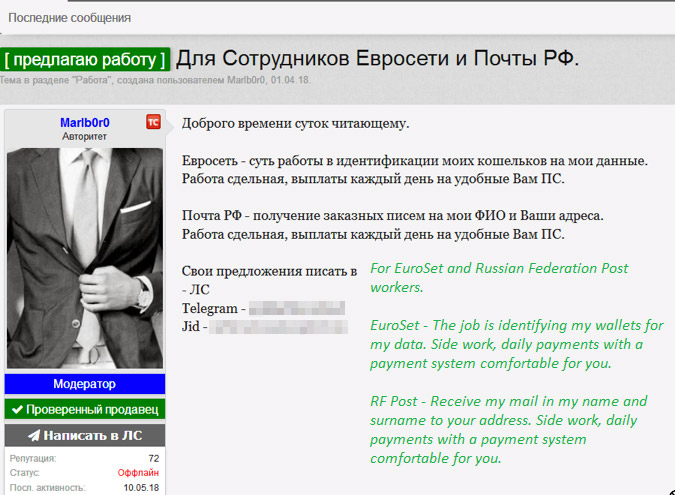 "Some actors in the underground also try to recruit post office workers to use as safe droppers, because as employees at the post office they can intercept certain packages for their employers and re-route them as necessary without raising much suspicion," SpiderLabs reports.
"Some actors in the underground also try to recruit post office workers to use as safe droppers, because as employees at the post office they can intercept certain packages for their employers and re-route them as necessary without raising much suspicion," SpiderLabs reports.Other advertisements target individuals who are willing to install card skimmers or "cutlets" - malware - in ATMs, SpiderLabs says. Typically, these job listing include no warning about "possible punishment from law enforcement," it says.
Fraudulent Shipping Labels as a Service
Reflecting the diversity of the cybercrime ecosystem, some listings don't just advertise dropper jobs, but also offer services for supporting a gang's droppers. Indeed, to make drops tougher to trace, some cybercrime groups and vendors hack into legitimate shipping service accounts and use them to fraudulently distribute goods, threat intelligence firm Flashpoint warned in an October 2018 report.
"Using the access afforded by those accounts and the shipping services' APIs, criminals are able to produce thousands of labels for customers; one recent review on an underground site raved that 99.9 percent of the labels were processed properly, ensuring that stolen goods reached the buyer or the drop network," Flashpoint said in a blog post. "Cybercriminals often use drop networks to obfuscate the destination and/or origin of stolen funds, or fraudulently purchased goods."
Darknet Markets Persist
Individuals hired via cybercrime job advertisements might work for a specific group, such as The Dark Overlord, that keeps all of its attacks and extortion attempts in-house.
But some cybercrime groups sell these services to others and advertise their offerings via various forums, including darknet sites such as Dream Market, Wall Street Market and Tochka Free Market.
Security experts say that while service providers may advertise on forums, takedowns of some of the world's biggest cybercrime forums - including AlphaBay, Dream, Hansa, Silk Road 2 and Trade Route - and subsequent prosecutions of alleged administrators, vendors and in some cases, buyers, has led to many cybercrime vendors being much more cautious (see: Bitcoin-Amassing AlphaBay Drug Barons Get US Prison Time).
Increasingly, they're using encrypted messaging apps, such as Telegram, to connect with potential customers or close deals (see: Cybercrime as a Service: Tools + Knowledge = Profit).
Professional Hacking Services and Attacks
What all is for sale? A review of listings on a major darknet site by the Threat Lab research team at security firm WatchGuard found that found service providers offering to deploy keyloggers for 0.0263 bitcoins - about $100, based on current exchange rates - as well as hack smartphones or email accounts, launch spyware or change school grades.
WatchGuard declined to name the specific darknet site that it had reviewed.
In addition, it found some service providers advertised "small jobs," such as hacking someone's Facebook account, for the bitcoin equivalent of about €250 ($285); medium-size jobs such as "ruining people" or launching a distributed denial-of-service attack against a larger site for €500 ($575); and larger jobs that encompass many smaller jobs or take multiple days, including "DDoS for protected sites," for €900 ($1,030).
Needless to say, selling or using these services, which are illegal, carries risks (see: UK Sentences Man for Mirai DDoS Attacks Against Liberia).
But at least some individuals, potentially located in jurisdictions where prosecutions for cybercrime are rare, appear willing and able to take these risks.
Indeed, Digital Shadows reported that not long after The Dark Overlord posted its job advertisement for four new team members, it reported that it had already filled three of the positions.
At least some people, apparently, continue to see cybercrime paying, at least in the short term.

