Cloud Security , Data Breach , Data Loss
Data Aggregator Exposed 44.3 Million Individuals' Details via Unsecured Servers(euroinfosec) • November 29, 2018 The Data & Leads website remains offline after the company exposed 44.3 million individuals' personal details online. (Source: Wayback Machine)
The Data & Leads website remains offline after the company exposed 44.3 million individuals' personal details online. (Source: Wayback Machine)Another day, another "Have I Been Pwned" alert, this time involving 44.3 million individuals' personal details, which were exposed by Toronto-based data aggregator Data & Leads.
See Also: Live Webinar | Levers of Human Deception: The Science and Methodology Behind Social Engineering
Have I Been Pwned is the free service created by Australian information security expert Troy Hunt, which allows anyone to register their email address. Anytime that registered email address is found in a data dump, Hunt's service automatically emails to alert them. At the very least, anyone who has been pwned should change their password with the service, when possible (see: Troy Hunt Discusses His Data Breach Message to Congress).
Unfortunately, that's not possible with a new breach that's been found, which appears to have resulted from a marketing services firm having left its open source Elasticsearch servers publicly exposed and unprotected by passwords or other forms of authentication.
So says security researcher Bob Diachenko, director of cyber risk research for security firm HackenProof, who reports that he found 73 GB of sensitive data during a routine search of publicly exposed servers using Shodan, a search engine for internet-connected devices.
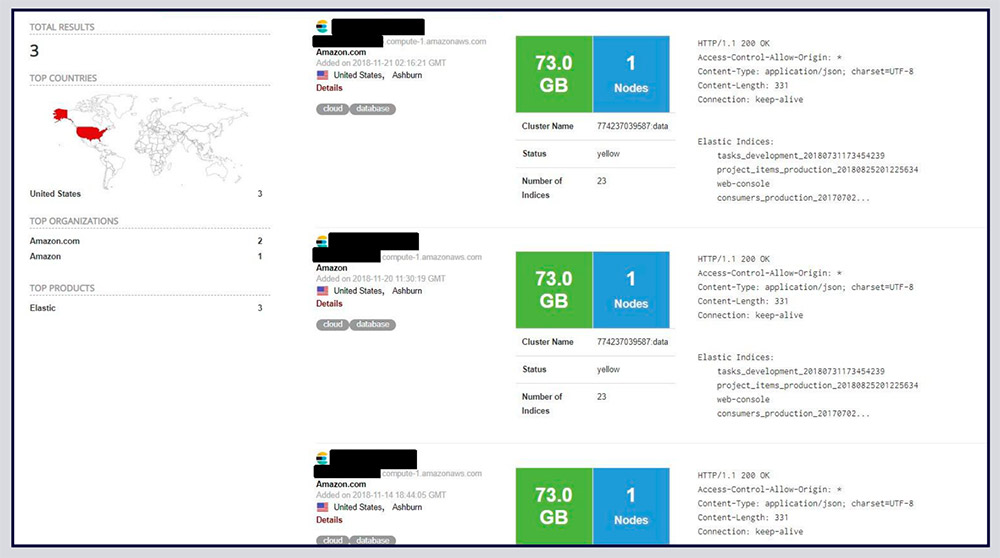 Shodan search results identified three open Elasticsearch servers. (Source: Bob Diachenko)
Shodan search results identified three open Elasticsearch servers. (Source: Bob Diachenko)"While the source of the leak was not immediately identifiable, the structure of the field 'source' in data fields is similar to those used by a data management company Data & Leads Inc. However, we weren't able to get in touch with their representatives," he says in a blog post. "Moreover, shortly before this publication Data & Leads website went offline and now is unavailable."
Diachenko says the first of three publicly exposed Elasticsearch instances, indexed by Shodan on Nov. 14, exposed what appeared to be personal information for 56.9 million U.S. citizens, "with information such as first name, last name, employers, job title, email, address, state, ZIP, phone number and IP address." The information appears to have been scraped from third-party sources.
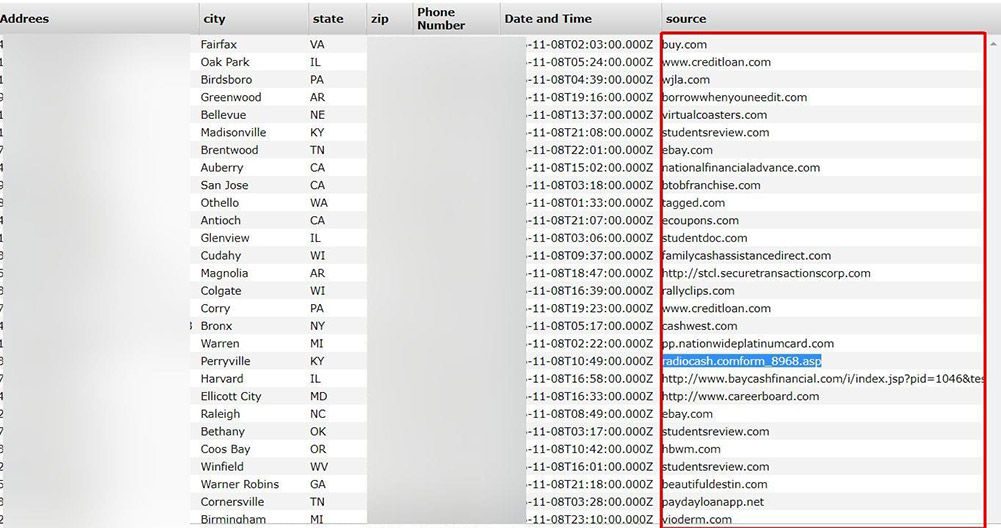 Source: Bob Diachenko
Source: Bob DiachenkoAfter Hunt reviewed and de-duplicated the data, the total number of individuals' details included in the database appeared to be 44.3 million, according to the Have I Been Pwned breach notification.
Another database, Diachenko says, included 25 million records containing corporate data, including company names and details, ZIP code, latitude/longitude and other information.
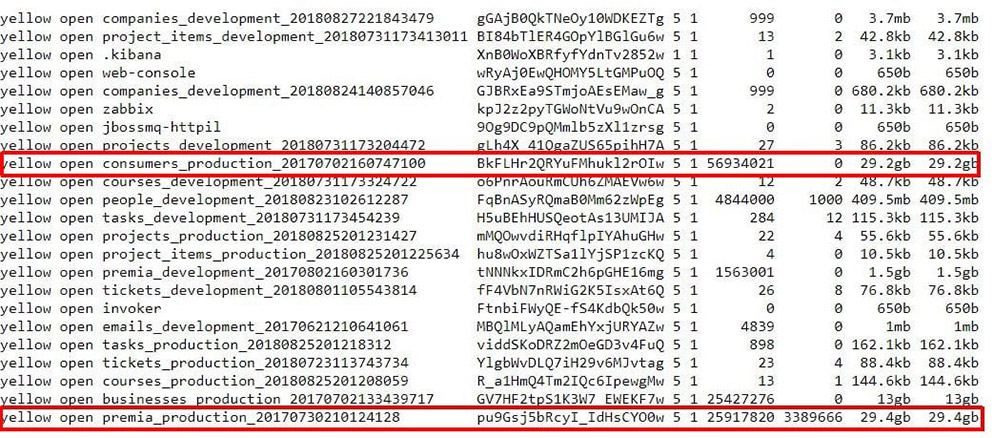 Source: Bob Diachenko
Source: Bob DiachenkoIt's possible this information was scraped from open, yellow pages types of sites.
Call It 'Data & Leak'?
Data & Leads describes itself as being "a data & lead solution company from Toronto, Canada," according to a cached version of the company's website.
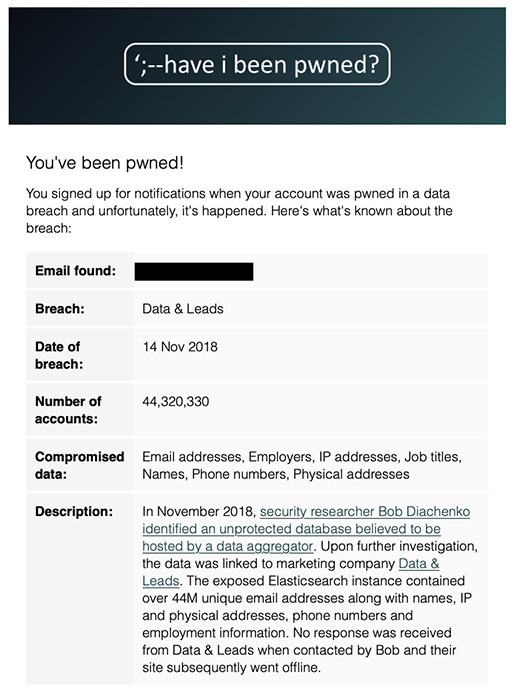 Email notification distributed on Wednesday by Have I Been Pwned to registered users whose email addresses were exposed by the unprotected Elasticsearch server apparently set up by Data & Leads
Email notification distributed on Wednesday by Have I Been Pwned to registered users whose email addresses were exposed by the unprotected Elasticsearch server apparently set up by Data & Leads"We have been providing business from all over the world with exclusive, high quality leads for the last 10 years," the website says. "Over this time, we have build [sic] a loyal customer and strong suppler base. No need is too big or small, and our large supplier network allows us to be a one stop shop for all your data and lead needs."
Diachenko tells me his efforts to contact the company have not been successful, except that they may have driven the company to take its website down.
As of Wednesday, "the database is no longer exposed to the public, however, it is unknown for how long it has been online before Shodan crawlers indexed it on November 14th and who else might have accessed the data," Diachenko says.
As of Thursday, the firm's website, including its grammar-challenged boilerplate, continues to remain offline, as does a contact form for the company. The cached version of the website lists no phone number or email address for making contact.
For too long, without a service such as Have I Been Pwned, many breaches that spilled individuals' personal details - especially outside the EU - would have never come to light.
In the EU, Europeans' personal details are now protected by the General Data Protection Regulation, which requires organizations to report certain types of breaches to authorities within 72 hours and penalizes organizations that fail to have sufficient data security processes and technology in place to protect individuals' personal information.
Breach reporting rules in Canada - the new Personal Information Protection and Electronic Documents Act, or PIPEDA - and in place in each of the 50 U.S. states offer less protection. But they typically at least do require organizations to alert consumers in a timely manner after their personal details get spilled (see: Canada's Mandatory Breach Notification Rules Now in Effect).
Canada's privacy watchdog, however, says that Data & Leads has yet to file a breach report. "At this point in time, our office has not received a breach report from the company. We are monitoring the situation and will follow up with the organization if appropriate," Corey Larocque, a communications adviser for the Office of the Privacy Commissioner of Canada, tells me.
"As you may know, organizations are now required to notify our office of serious breaches of security safeguards involving the personal information of Canadians," he says. "Generally speaking, in cases where a company determines that Canadian customers were affected by an incident and there is a real risk of significant harm, we would expect them to notify those individuals and our office."
Hackers' Open Season on Open Elasticsearch Instances
Many of these data breaches trace to cloud-based storage - especially Amazon's S3 Simple Cloud Storage Service buckets - that have been incorrectly configured, leaving stored data publicly accessible.
Diachenko regularly warns organizations when he finds open S3 buckets that have been configured to allow public access, which they do not do by default. He also reports regularly finding publicly exposed instances of Elasticsearch that are not password-protected, which unfortunately is their default.
Elastic, which develops the Elasticsearch stack, has said they're not meant to be publicly exposed, and that it's developers' responsibility to protect them using passwords or other authentication if they choose to expose them publicly.
"It is very important to secure all Elasticsearch instances, especially those that are accessible over the internet," Diachenko tells me. Attackers, he says, can easily abuse open instances of Elasticsearch to install ransomware or other types of malware on the server (see: Robocalling Firm Leaves Virginia Voter Data Online).
"The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges," he says in his blog post. "Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains."
Elasticsearch: 3 Security Essentials
For any organization that uses Elasticsearch, Diachenko advises they should always follow these three security rules:
Backing up: Back up all Elasticsearch data only to a secure location; Reconfigure: Only run Elasticsearch "on an isolated non-routable network"; Remote security: "If you must access the cluster over the internet, restrict access to your cluster from the internet via firewall, VPN, reverse proxy or other technology."When Data Aggregators Leak
Data and Leads' data aggregation practices resemble those of another data aggregator that also lost control of its data: Dun & Bradstreet.
In 2016, 33 million corporate U.S. individuals' names, physical addresses, email addresses, employers and job titles were leaked, apparently via someone who had obtained them from Dun & Bradstreet's NetProspex service.
Again, the breach came to light in part thanks to Hunt's efforts (see: Yes, I Have Been Pwned).
Dun & Bradstreet, however, declined to notify victims, saying that it was the type of information that it supplies to its customers on a daily basis. In other words, so long as they don't leak people's financial details, the penalty for firms that buy, sell, scrape or trade in U.S. and Canadian residents' personal information and then lose control of it appears to remain nil.
Updated with comment from Canada's OPC.

