Anti-Malware , Cybercrime , Fraud
Fallout Exploit Kit Has Also Reappeared, Distributing GandCrab Ransomware(euroinfosec) • January 18, 2019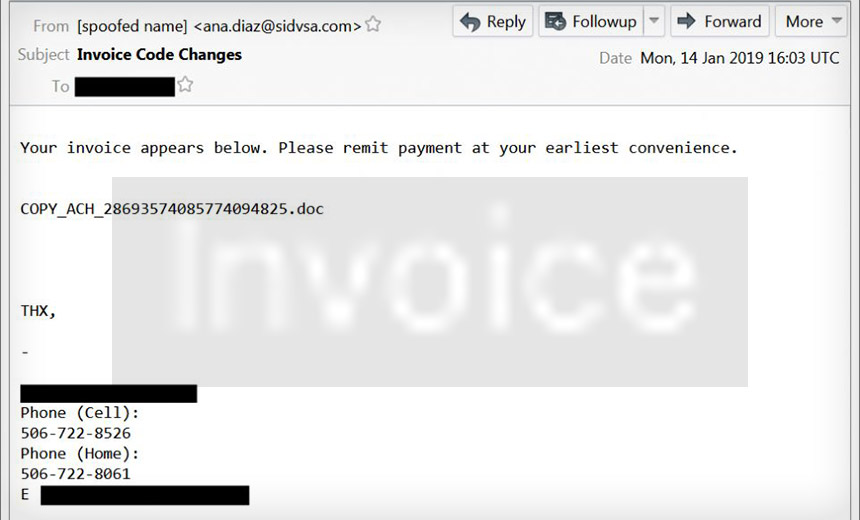 Spam email with an attached Microsoft Word document that contains a malicious macro designed to download and execute Emotet malware (Source: Brad Duncan)
Spam email with an attached Microsoft Word document that contains a malicious macro designed to download and execute Emotet malware (Source: Brad Duncan)Malware developers as well as their customers or subscribers often appear to take a vacation around the Christmas and New Year holidays, and last month was no exception.
See Also: Live Webinar: Building Secure Delivery Pipelines with Docker, Kubernetes, and Trend Micro
Following a December slowdown or hiatus, however, attacks involving Emotet - aka Feodo; Hancitor - aka Chanitor and Tordal; and Trickbot have resurged, reports Brad Duncan (@malware_traffic), a threat intelligence analyst for the Unit 42 research group at Palo Alto Networks, in a blog post for the SANS Institute Internet Storm Center.
Duncan says that among today's most widespread malware campaigns, "Emotet is by far the most active" in terms of attacks, as well as being frequently updated by its developers.
"Dozens of indicators are discovered every day as vectors for Emotet infections. Emotet also acts as a distributor for other families of malware," he says. "So far in 2019, I've seen Emotet retrieve Gootkit and the IcedID banking Trojan. As 2019 progresses, I expect to find examples of Emotet distributing other families of malware like Qakbot and Trickbot, something we saw in 2018."
Emotet Evolves
Emotet was a banking Trojan when it first appeared in 2014. But it has continued to wield new tricks, including serving as a dropper - aka downloader and installer - for other strains of malware, including not only Trickbot but also Zeus Panda Banker (see: Malware Moves: Attackers Retool for Cryptocurrency Theft).
In July 2018, the U.S. Computer Emergency Readiness Team warned: "Emotet continues to be among the most costly and destructive malware affecting [state, local, tribal, and territorial] governments. Its worm-like features result in rapidly spreading network-wide infections, which are difficult to combat. Emotet infections have cost SLTT governments up to $1 million per incident to remediate."
The group behind Emotet, called Mealybug, has been using the malware to distribute other malicious code, which has included Ryuk ransomware, since the middle of 2018 (see: Connecticut City Pays Ransom After Crypto-Locking Attack).
Modular Threat
Besides serving as a malware-distribution engine, Emotet remains dangerous in its own right. "It is a highly modular threat with a variety of payloads being delivered," says Edmund Brumaghin, a threat researcher at Cisco's Talos security group. He notes that the addition of new features and capabilities seems to have made Emotet especially popular with cybercriminals.
A spamming module built into Emotet, for example, recently gained the ability to check "if the compromised system's IP address is currently found on many spam-related blacklists including those hosted by SpamCop, Spamhaus and SORBS, among others," he says. Spammers can use that information to focus their efforts on using PCs that are not yet on a blacklist to distribute spam.
Cybercrime Goal: Profits
That's a reminder that for most criminals who use malware, time is money.
"The goal of Emotet, as is the case with crimeware-based threats, is monetary," Brumaghin says. "Attackers use Emotet to deliver modular payloads [they] can use to monetize infections. Those payloads can include threats like banking Trojans, stealers, self-propagation, email harvesters and ransomware. The modules the attackers deploy are likely chosen based on the way they can best monetize infected systems and the environments in which those systems reside."
Security experts say Emotet is being distributed in two ways: via emails that have attached Microsoft Word documents with malicious macros and via emails with malicious links. If a user opens the attachment and enables macros, or follows the link, it can result in the Emotet payload being downloaded and executed on their system.
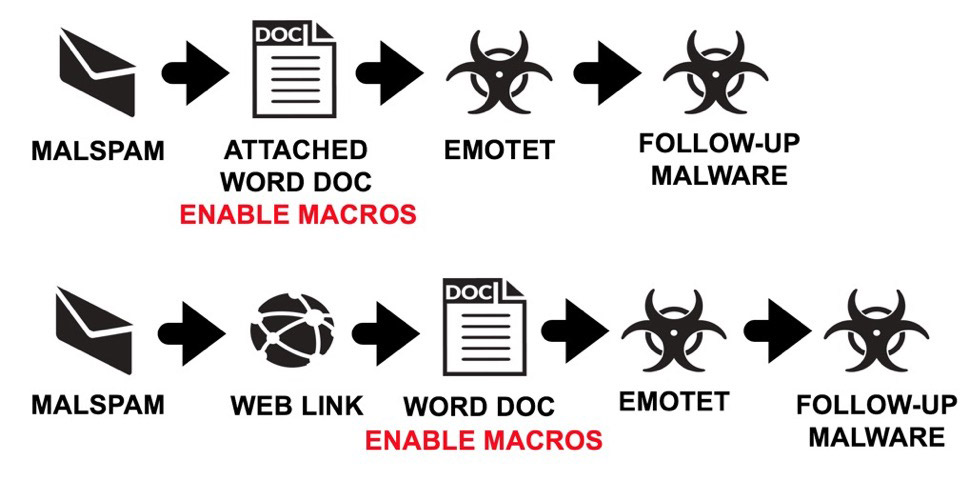 Emotet is being distributed in two ways: by spam emails with malicious Word documents attached, and via spam emails with malicious links to payload downloaders. (Source: Brad Duncan)
Emotet is being distributed in two ways: by spam emails with malicious Word documents attached, and via spam emails with malicious links to payload downloaders. (Source: Brad Duncan)"Malicious code embedded in the malicious attachment functions as a downloader for the Emotet malware," says Brumaghin at Cisco Talos. "When this code is executed, PowerShell is invoked, which reaches out to the Emotet malware distribution server, downloads the malicious payload, and executes it, thus infecting the system.
Spam Themes: Shipping, Invoices
Cisco Talos says that unlike many previously seen attack campaigns via email, Emotet appears to be able to cycle through a large number of different subject lines, although it often focuses on invoices or shipping. The campaigns are also being run in multiple languages.
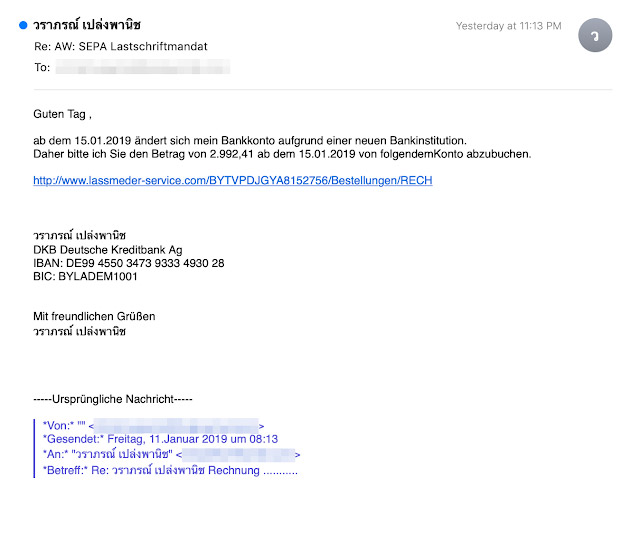 Emotet campaign: This German-language spam email includes a link that downloads the Emotet payload. (Source: Cisco Talos)
Emotet campaign: This German-language spam email includes a link that downloads the Emotet payload. (Source: Cisco Talos)Emotet Avoids Russia
Cybercrime expert Peter Kruse, who heads the eCrime Unit at CSIS Security Group in Denmark, says Emotet does not appear to target - or likely to work at all in - Russia, based on there being no Emotet command-and-control servers located there.
That's a clue to the identity of the group behind the malware. Cybercrime groups operating from Russia can often avoid running afoul of Russian authorities if they ensure that none of their attacks hit individuals living in Russia or neighboring countries. Russia has also never extradited a citizen for alleged cybercrime offenses (see: Russian Cybercrime Rule No. 1: Don't Hack Russians).
Fallout Exploit Kit Returns
Attack campaigns using Emotet, Hancitor and Trickbot aren't the only ones to have returned after going quiet last month.
Following a brief hiatus through early January, the Fallout exploit kit has also reappeared, says Jérôme Segura, a security researcher at Malwarebytes, in a blog post.
"Fallout EK is distributed via malvertising chains (one of them we track under the name HookAds), especially through adult traffic. Since Jan. 15, Fallout EK activity has been picking up pace again to deliver the GandCrab ransomware," Segura says (see: Ransomware Claims to Fund Child Cancer Treatments).
Fallout has also been updated to target a vulnerability in Adobe Flash Player, designated CVE-2018-15982, found in all versions of Flash up to 31.0.0.153. Adobe patched the vulnerability on Dec. 5 via a software update. Last month, Malwarebytes reported that the Underminer exploit kit was targeting the same flaw.
Subsequently, the security researcher known as Kafeine first spotted Fallout targeting the same Flash flaw on Wednesday, via in-the-wild attacks, some of which are installing GandCrab.
A recent advertisement for Fallout posted on the Associated Advert underground forum advertised the ability to target CVE-2018-15982 and also said the exploit kit is available to rent for $400 per week or $1,300 per month, Kafeine says in a blog post.
5 Most Prevalent Malware Strains
In terms of sheer prevalence, however, Emotet and its ilk still take second place to many types of malware that are designed to surreptitiously steal CPU - and sometimes GPU - cycles on a system to mine for cryptocurrency.
In December, Check Point Software Technologies listed the following as being the top five most prevalent strains of malware:
Coinhive: JavaScript that gets planted on websites to mine for monero cryptocurrency "without the user's knowledge or approval, and without sharing the profits with the user"; XMRig: Open source software also designed to mine for monero using the infected systems's CPU, first spotted in the wild in May 2017; Jsecoin: JavaScript cryptocurrency miner that can be embedded in websites; Cryptoloot: A cryptominer that competes with Coinhive - in part by taking a smaller share of mining proceeds - and which uses a victim's CPU or GPU power; Emotet: As noted above, this advanced malware often also distributes other malware. "It uses multiple methods for maintaining persistence and evasion techniques to avoid detection. In addition, it can be spread through phishing spam emails containing malicious attachments or links."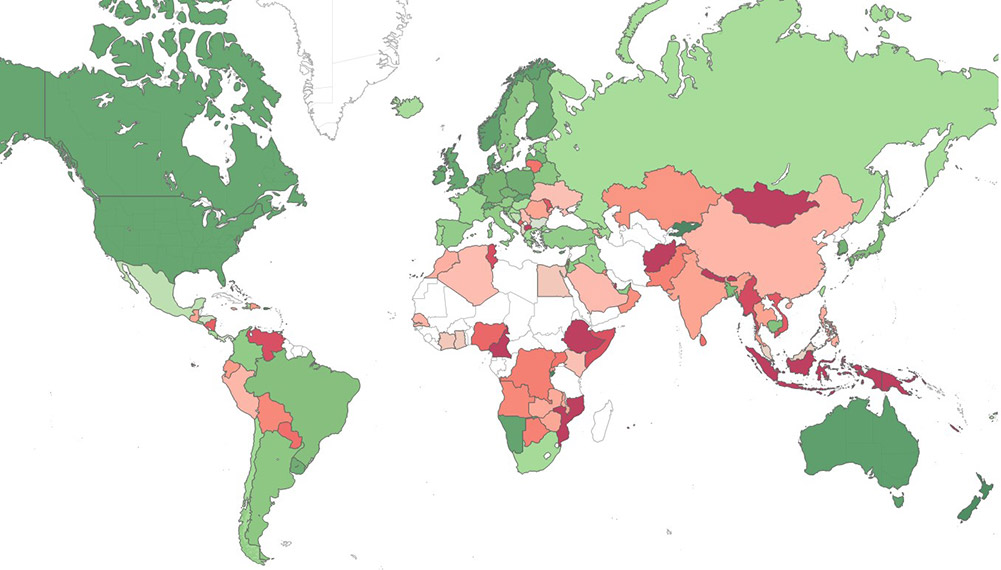 Check Point's world map of malware hotspots based on risk of infection (green for low risk, red for high, and gray indicating insufficient data).
Check Point's world map of malware hotspots based on risk of infection (green for low risk, red for high, and gray indicating insufficient data).
