Application Security , Breach Response , Data Breach
Android App Left User Data Open Without Authentication or TLS/SSL(jeremy_kirk) • February 18, 2019 Source: Facebook
Source: FacebookFor years, Facebook allowed app developers liberal access to user data. It served as powerful bait to draw developers to Facebook's platform, which in turn helped the social network develop one of the internet's largest user bases.
But the implications of that sharing became clear after the Cambridge Analytica scandal. The defunct voter-profiling firm obtained data for 87 million profiles from a researcher who created a personality quiz app that was deployed around 2013 (see Facebook and Cambridge Analytica: Data Scandal Intensifies).
The ensuing outrage over the situation, driven in part by Cambridge Analytica's work with U.S. President Donald Trump's campaign, drew scrutiny into Facebook's policies around collecting user data.
Facebook launched an audit of app developers and in early 2018 suspended more than 200 apps. In April 2018, Facebook opened the hunt for loose user data, creating a bug bounty program for information on data that may have been misused.
One of those bug reports has been revealed. On Thursday, the cybersecurity consultancy Nightwatch Security wrote that it discovered an Android app that had been storing Facebook user data in two unsecured places, a Firebase database and an API server.
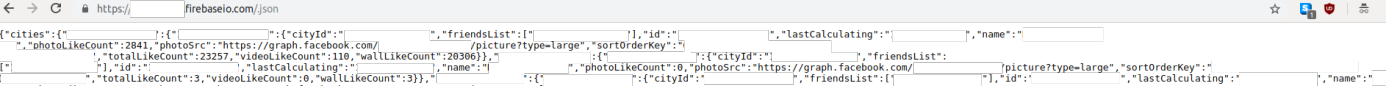 A screenshot showing some of the data fields collected by the Android app. (Source: Nightwatch Security)
A screenshot showing some of the data fields collected by the Android app. (Source: Nightwatch Security)Neither location required authentication or was protected by TLS/SSL. The Firebase database has been configured in a test mode, which allowed anyone to visit it by entering its URL, Nightwatch writes.
"This would allow an attacker to mass download the user data accumulated by the application from its users," Nightwatch Security writes in a bog post. The company received an unspecified bounty from Facebook.
Facebook officials queried in Sydney on Monday did not have an immediate comment.
Data: Sensitivity Unknown
The name of the app, which first appeared in Google's Play Store in early 2017, hasn't been made public. Nightwatch Security wrote on Twitter that it engaged with Facebook and not with the app developer directly. Nightwatch says it stumbled across the problem in the context of investigating something else.
The app "purported to provide additional statistical information about the logged-in user's Facebook account. There is a privacy policy within the application but it is ambiguous about the transfer of data," Nightwatch writes.
It's unclear exactly what data from a person's profile was exposed, as Nightwatch Security wisely pulled back after making the discovery. But according to Facebook's rules for qualifying for a bounty, data that is "already public" is out of scope, which suggests the information went beyond a Facebook user's public profile.
"Once we saw there was personal data, we did not explore further," Nightwatch Security tells ISMG.
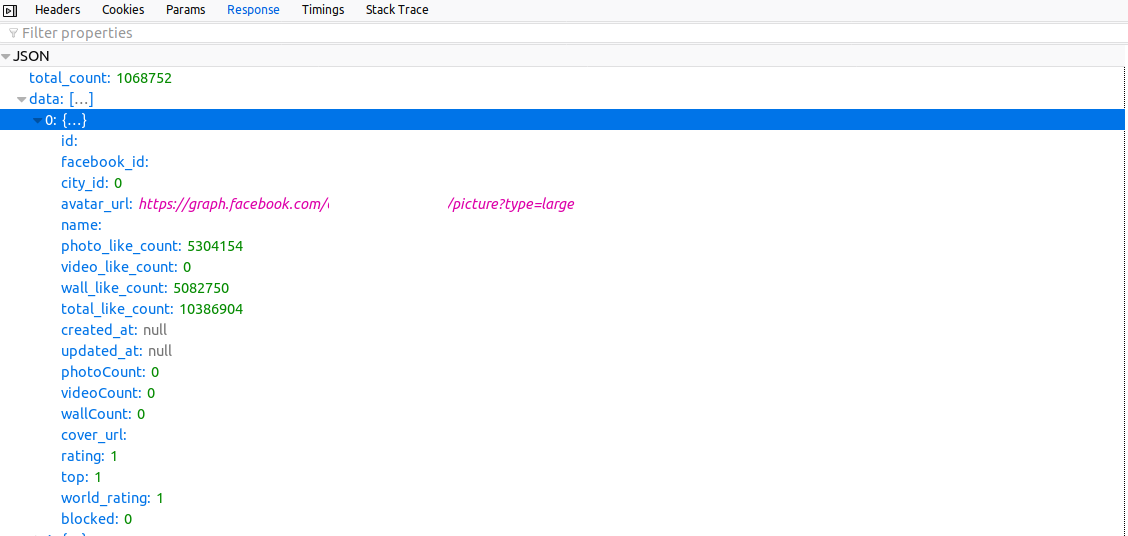 A screenshot that shows another view of the data fields exposed by the Android app. (Source: Nightwatch Security)
A screenshot that shows another view of the data fields exposed by the Android app. (Source: Nightwatch Security)More than 1 million people downloaded the app, which is still in Google's Play Store. Nightwatch writes it has contacted Google. However, the app is no longer allowed access to Facebook's platform. Nightwatch wrote on Twitter that it suspects its access to Facebook's APIs may have been cut off.
Nightwatch writes that it notified Facebook in September 2018, but the two locations where the data was stored weren't secured until November 2018.
It's unclear why the data continued to sit in the open for that long. But Facebook advises on its bug bounty page that investigations could take months. Also, the social networking company may have been dependent on some cooperation by the app developer to take it down.
"An investigation of a breach of data use rules is a lengthy process that involves technical, legal and organisational efforts which all differ depending on country and market," Facebook writes. "As such, we estimate that reports could take [three to six] months to fully investigate, but sometimes longer."
Continuing Legal Troubles
The kind of data that app developers can obtain has become more restrictive since Facebook introduced changes to its platform in April 2014. Before then, Facebook allowed app developers to collect not only information for direct users of their app, but also data for those users' friends.
Only 300,000 users downloaded the personality quiz that was the focus of the Cambridge Analytica scandal. But that opened a door to their friends, pushing the exposure up to 87 million profiles.
Since those users didn't concede to their data being collected, Facebook has faced numerous regulatory and legal actions.
The FTC and Facebook are reportedly in negotiations over what could be a record-breaking fine. Facebook has been under an FTC consent decree since 2011, when the agency alleged it shared data without users' consent with third-party apps. The fine could be in the billions (see Report: Facebook Faces Multibillion Dollar US Privacy Fine).
Also, Washington, D.C., filed a federal lawsuit in December 2018 alleging that the social network violated consumer protection law. Facebook, the lawsuit says, deceived users with privacy controls that made users believe their data wouldn't be shared (see Facebook Sued in US Over Cambridge Analytica).
In the U.K., regulators fined Facebook over Cambridge Analytica Facebook £500,000 ($645,000) in October 2018. Facebook is appealing the fine, the highest the regulator is allowed to levy (see Facebook Slammed With Maximum UK Privacy Fine).

