Business Continuity Management / Disaster Recovery , Business Continuity/Disaster Recovery , Cybercrime
Cybercrime Gang Wielding Ryuk Eyed as Culprit• March 12, 2019 Jackson County officials announced post-ransomware infection outages via Facebook
Jackson County officials announced post-ransomware infection outages via FacebookOfficials in Jackson County, Georgia, along with the FBI are investigating a ransomware attack that crippled IT systems over a two-week period. Struggling to recover from the outage, local officials reportedly paid a ransom worth $400,000 in bitcoins to restore IT systems and infrastructure.
Jackson County Manager Kevin Poe told Online Athens that the county government decided to cough up the ransom late last week after IT systems had been offline since about March 1, forcing officials to use paper and pen to complete numerous task, although police radios and the 911 system continued to function.
See Also: Live Webinar | Passwords: Here Today, Gone Tomorrow? Be Careful What You Wish For.
Suspects in criminal cases could still be booked in the local jail, but deputies needed to fill out all paperwork by hand, Jackson County Sheriff Janis Mangum told StateScoop.
County officials could not be immediately reached for additional comment.
A post on the county's Facebook page dated March 6 informs residents that the email systems remain down and that anyone seeking help should call the numbers listed on the website. It was not clear as of Tuesday if all systems had returned to normal.
Ryuk Strikes Again
While the ransomware outbreak remains under investigation, Poe told Online Athens that the ransomware was "Ryunk." He speculated that it was likely the work of an Eastern European group.
It appears likely, however, that the ransomware is actually Ryuk, which several law enforcement agencies and security firms started tracking at the end of 2018. It affected the printing presses of the Tribune Publishing company a few days after Christmas last year.
Similar to other strains of ransomware now being used in many types of attacks, such as SamSam, Ryuk targets specific systems within a network. Criminal organizations using these types of attacks appear more willing to map a network for days or even months before unleashing crypto-locking code. This appears to be the case in Jackson County as well.
After the county paid the ransom, the attackers sent it the decryption tool that could restore files and data, according to the published reports.
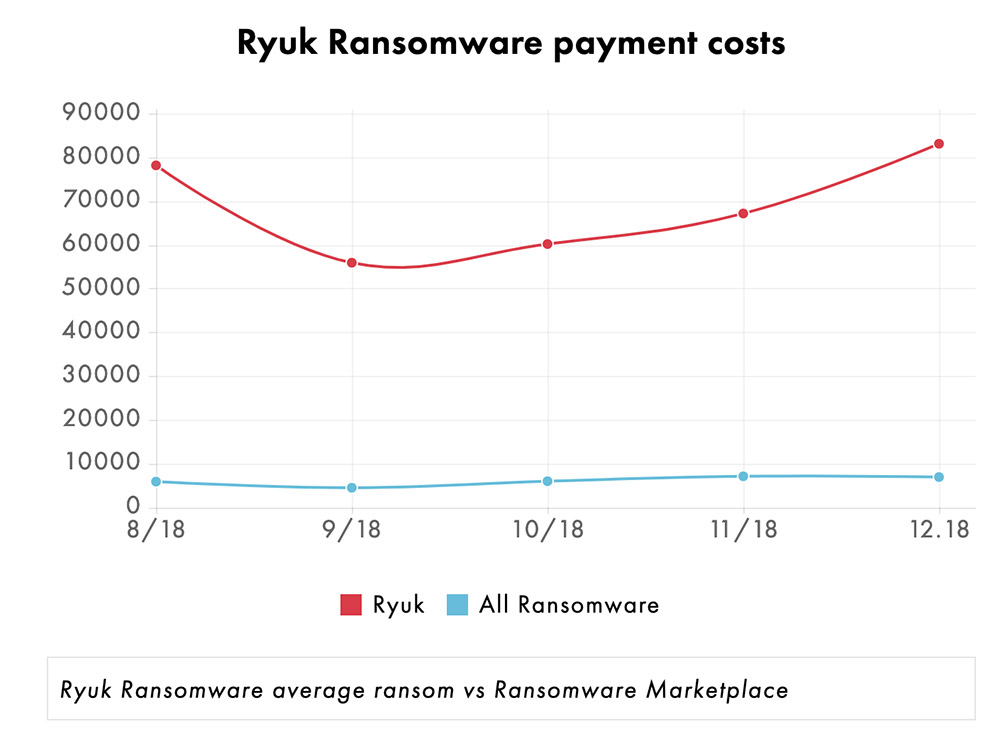
If the ransomware that hit Jackson County was indeed Ryuk, the county may still have a long road to recovery ahead of it. Ransomware incident response firm Coveware says that on average, the Ryuk decryptor tool only manages to restore 60 percent of the data that it has crypto-locked (see: Ransomware Victims Who Pay Cough Up $6,733 - on Average).
 Source: Coveware
Source: Coveware"Because of the extremely high ransom demands, and highly problematic decryption tool, a Ryuk attack can be fatal to a business that is intolerant of downtime and does not have easily restored backups," says Bill Siegel, CEO of Coveware.
 Excerpt from a Ryuk ransom note (Source: McAfee/Coveware)
Excerpt from a Ryuk ransom note (Source: McAfee/Coveware)Tracking Origins
What makes Ryuk unusual is that it shares some of the same source code as Hermes, which some believe points to North Korea and a state-sponsored advanced persistent threat group being behind the attacks. However, further analysis by several security firms, including McAfee, concluded the ransomware is being used by criminals.
Last week at the RSA Conference 2019 in San Francisco, Raj Samani, chief scientist of McAfee, and John Fokker, McAfee's head of cyber investigations, told Information Security Media Group that based on their firm's research, backed by information shared by Coveware, the group behind Ryuk does not appear to be backed by a nation-state, as some researchers have suggested, but rather a cybercrime gang, or even two separate gangs (see: 11 Takeaways: Targeted Ryuk Attacks Pummel Businesses).
Fokker also repeated Coveware's warning about Ryuk's decryptor, saying it was so poorly coded that it often failed for trivial reasons. When it did restore files, he said that all files might be restored to a single directory, breaking file hierarchies. As a result, incident responders often face a restoration process that requires grueling amounts of manually restoring decrypted files to their rightful location.
To Pay or Not to Pay
Law enforcement officials and security experts regularly counsel ransomware victims to never pay ransoms to attackers, since it directly funds further criminal activities and may lead to victims being targeted multiple times. But some businesses and government agencies do pay ransoms, especially when they have no defenses in place, their backup systems have failed or the attack leaves their business or operations at risk of folding.
Jackson County used a third-party firm to contact the attackers and arrange the payment, according to published reports. While paying might encourage other ransomware schemes, Steve Durbin, the managing director of the Information Security Forum, a London-based authority on cybersecurity and risk management, tells ISMG that often, victims lack a backup plan, so paying the ransom is perceived to be the only option.
"When it comes to ransomware in particular, one question that I'm asked frequently is: 'Should I pay?' Ultimately, this is up to the discretion of the individual or the organization," Durbin says. "Most will say that you should not pay. Others will say that it is OK. But remember, you could end up with a target on your back. The bottom line is that if you can't do without the information, and you don't have a backup, then paying is the only alternative you have left to recapture your information. Therefore, prevention is the way to go to better protect yourself."
Georgia on My Mind
The attack again Jackson County marks the second time that the state has been hit with a major ransomware attack .
Atlanta was targeted by two Iranian nationals wielding SamSam ransomware, a U.S. Justice Department indictment recently alleged. The attack left Atlanta with a recovery bill that stretched to millions of dollars.
The group behind that attack also hit several other public organizations, including Newark, New Jersey; the Colorado Department of Public Transportation; the Port of San Diego as well as several hospitals. The Justice Department said the attackers collected a total of about $6 million in ransom payments.
Executive Editor Mathew Schwartz contributed to this report.

