Remember the December 13 email blast that threatened to blow up buildings and schools unless recipients paid a $20,000 ransom? It triggered mass evacuations, closures, and lockdowns in the US, Canada, and elsewhere around the world.
An investigation shows the spam run worked by abusing a weakness at GoDaddy that allowed the scammers to hijack at least 78 domains belonging to Expedia, Mozilla, Yelp, and other legitimate people or organizations. The same exploit allowed the scammers to hijack thousands of other domains belonging to a long list of other well-known organizations for use in other malicious email campaigns. Some of those other campaigns likely included ones that threatened to publish embarrassing sex videos unless targets paid ransoms.
Distributing the malicious emails across such a broad swath of reputable domains belonging to well-recognized organizations was a major coup. The technique, known as snowshoe spamming, drastically increased the chances the emails would be delivered because it weakened the reputation metrics spam filters rely on. Rather than appearing as fringe content sent by one or a handful of sketchy domains, the snowshoe technique gave the emails an air of legitimacy and normalcy. The technique gets its name because, like snowshoes, it distributes the heavy load evenly across a wide area.
Commandeered by Spammy Bear
Domains that sent the December bomb threats included wotdonate.com, wothome.com, wotlifestyle.com, wotnetwork.com, and wotscooking.com, which whois records show are all owned by Expedia. Other domains included Yelpmarketingservices.com, virtualfirefox.com, and blueestatescoffee.com, which are registered to Yelp, Mozilla, and food service giant Aramark, respectively. In all, Ars knows of 78 domains used to send the threats, although the total number is likely higher.
Meanwhile, the number of domains hijacked by the same person or group and used in other campaigns is much higher still. An analysis of historical Internet records compiled by independent researcher Ronald Guilmette shows that in the last few years, that person or group has commandeered almost 4,000 domains belonging to about 600 people, companies or organizations. The list of registered domain holders—to name a small few—include Facebook, MasterCard International, Hilton International, ING Bank, Dignity Health, the Church of Scientology, Warner Bros. Entertainment, Massachusetts Institute of Technology, McDonalds Corporation, and certificate authority DigiCert.
“The domains that I have identified as being stolen are *not* simply ones that some bad actor has put entirely fraudulent WHOIS data in for,” Guilmette wrote in a preliminary report sent to a handful of reporters. “The WHOIS data *is* correct, most probably on 100% of the suspect domains I have identified. The domains *do* belong to the people and companies reflected in the WHOIS records. They have just been temporarily commandeered by Spammy Bear, as I've said from the beginning.”
It wasn’t immediately clear from the evidence provided by Guilmette if the domains in this much larger set of hijackings have been used in spam runs, but it would hardly be surprising if they were. Evidence unearthed by Guilmette and other researchers links the December bomb threats to clusters of other email scams, including a massive sextortion campaign that has been active since July and scams involving fake parking tickets and failed package deliveries. Researchers have yet to identify the person or group behind the scams. Guilmette has dubbed the entity "Spammy Bear," because the hijacked domains tend to use IP addresses from Russia-based hosting provider reg.ru.
After noticing that virtually all of the affected domains were receiving domain-resolution service from GoDaddy prior to being hijacked, Guilmette theorized that a system-wide vulnerability was somehow involved. Last Friday, Ars asked GoDaddy if it was the source of the domain hijackings. On Tuesday evening, the company responded with the following statement:
After investigating the matter, our team confirmed that a threat actor(s) abused our DNS setup process. We’ve identified a fix and are taking corrective action immediately. While those responsible were able to create DNS entries on dormant domains, at no time did account ownership change nor was customer information exposed.
Beware of "orphan" domains
GoDaddy didn’t detail the weakness that was abused, but several pieces of evidence make a compelling case that it involved an industry-wide shortcoming that in the past has affected other providers of managed DNS services.
Exhibit A in building this case: as noted earlier, virtually all of the hijacked domains had name servers that listed domaincontrol.com, the domain for GoDaddy’s managed DNS service, just prior to them coming under Spammy Bear’s control. Despite name servers listing GoDaddy's DNS, virtually all of these domains were also unresolvable at the time they were hijacked. That’s an indication that the domain holders had allowed their DNS subscription with GoDaddy to expire but had failed to update the domains' name servers to reflect this change.
Below is a historical record for virtualfirefox.com, the Mozilla-owned domain that was used to send bomb threats. Notice how from 2013 to 2017 it resolved to its intended IP address of 74.80.210.168. Then, in November 2017 it became unresolvable even as the name server history shows its name server continued to point to DNS service from GoDaddy’s domaincontrol.com. Then last December it suddenly resolved to 194.58.58.70, an IP address that’s registered to reg.ru and that a variety of security services warn has a history of serving malicious content.
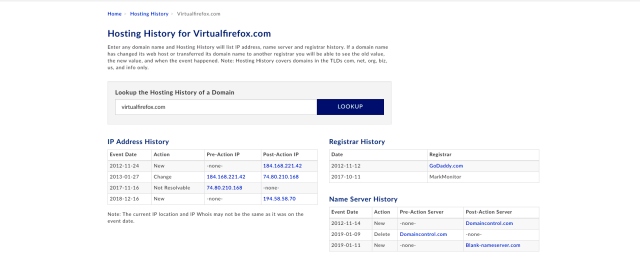
Enlarge / A historical record of virtualfirefox.com.
Matthew Bryant
Exhibit B is a blog post published in December 2016 by independent researcher Matthew Bryant. In it, Bryant reported a weakness he found in managed DNS services provided by Google Cloud, Amazon’s Route 53, Rackspace, and DigitalOcean that left control of more than 120,000 domains up for grabs.
The weakness, Bryant reported in 2016, presented itself when a domain’s name server continued to point to one of these services even after the owner had deleted the zone file, closed the DNS account, or allowed trial or billing for the DNS hosting service to expire. Bryant described domains that met this threshold as “orphaned,” because while they still pointed to a valid DNS provider, they remained unresolvable. The researcher went on to explain that it was trivial for anyone to take control of orphaned domains—simply by creating a new zone file on the managed DNS service listed in the domains’ name server.
Last Thursday, Ars emailed Bryant and asked if orphaned domains pointing to GoDaddy’s DNS service might be vulnerable to the same hijacking attack. With less than an hour of investigation, he determined it was. Interestingly, he found it didn’t cost attackers anything to exploit the weakness against GoDaddy because free accounts provided a larger pool of domaincontrol.com subdomains than paid accounts.
“I am confirming they have the issue, and it doesn't cost anything to exploit,” Bryant wrote in an email. “You actually get a pair of XXpdns.domaincontrol.com nameservers when you upgrade to premium DNS which would limit your ability to exploit most of these. It's better to have the free accounts as they will allow you to take over the most amount of domains.”
In all, Guilmette has catalogued 3,971 domains that he says have been hijacked by Spammy Bear. Some, but not all, of the 78 domains known to have sent the December bomb threats overlap with that list. Bryant, the independent researcher who discovered the DNS weakness in 2016, reviewed the list and pseudo-randomly picked a handful of domains. All of them met the criteria for being hijacked.
In an email, a Mozilla representative said the organization took ownership of virtualfirefox.com in September 2017 following a trademark dispute and didn't get around to securing the DNS records until earlier this month. "This oversight created a state where the DNS pointed to a server controlled by a third party, leaving it vulnerable to misuse," the representative wrote. "In addition to addressing the immediate problem, we have reviewed the entire catalog of properties we own and are taking steps to ensure this does not happen in the future."
Ars has emailed both Expedia and Yelp for comment but has not yet received a response.
Half a million domains up for grabs
Two nights ago, Guilmette downloaded a complete copy of the zone file for domains ending in .com and identified 34 million that pointed to GoDaddy DNS servers. Then he checked to see how many of them weren't resolvable. The answer: almost 262,000. When considering the 74 million domain names GoDaddy says it manages, Guilmette estimates GoDaddy's weakness left more than 553,000 domains vulnerable to hijacking.
The take-away from all of this is that for two years GoDaddy’s DNS service has supplied some of the most nefarious scammers on the Internet with an almost unlimited number of high-value domains. While the abuse relied on domain holders not properly locking down their DNS records, Bryant made a compelling argument that it was the DNS providers who are ultimately responsible for the abuse of their services.
“A lot of providers say: ‘It’s not our fault. It’s a user mistake,’” Bryant explained. “But if the case is that the user is going to make this mistake every time, it’s still a problem and it causes very real issues. Everybody can say: 'It’s this person’s responsibility. It’s not ours.’ But at the end of the day, it’s the providers who are going to have to take responsibility to get it fixed.”

