Fraud Management & Cybercrime , Governance , Identity & Access Management
Botnet Scanning Internet for Vulnerable Windows Machines(@Ferguson_Writes) • June 7, 2019
A new botnet dubbed GoldBrute is using brute-force or credential-stuffing methods to attack vulnerable Windows machines that have exposed Remote Desktop Protocol connections, according to new research from Morphus Labs.
See Also: Webinar | Passwords: Here Today, Gone Tomorrow? Be Careful What You Wish For.
While the end-goal of the group controlling the botnet is not clear, it appears that GoldBrute is currently using brute-force methods to attack about 1.5 million Remote Desktop Protocol servers that have exposed connections to the open internet, Renato Marinho, the chief research officer with Morphus, writes in blog published Thursday.
A scan using the Shodan search engine shows that there are at least 2.4 million of these exposed Remote Desktop Protocol servers throughout the world. GoldBrute, however, seems to use its own list as part of the attacks and keeps expanding as that list grows, Marinho's research shows.
The news of this particular botnet comes as Microsoft and the U.S. National Security Agency have each issued a series of warnings concerning BlueKeep, a vulnerability within the company's Remote Desktop Protocol service that could enable attackers to use a worm-like exploit to take over devices running unpatched older Windows operating systems (see: Researcher Posts Demo of BlueKeep Exploit of Windows Device).
While there is not an immediate connection between BlueKeep and GoldBrute, it doesn't mean that the group controlling the botnet could not use that vulnerability in the future, Marinho tells Information Security Media Group.
"GoldBrute is a botnet that implements a distributed brute-force method to try to find its victims," Marinho says. "It does not exploit any RDP vulnerability like BlueKeep. However, it's true that they are continuously scanning and collecting open RDP addresses that could be handy in future attacks."
Assessing GoldBrute
Through his research, Marinho found that the GoldBrute botnet is controlled by a single command-and-control server, and that the various bots are communicating and exchanging data with that server using an AES encrypted WebSocket connection tied to port 8333.
Once a vulnerable Windows system is infected with malware, it is instructed to download the botnet code, according to the Morphus research. The code itself is rather large - about 80MB - since it contains a full Java runtime, and a Java class within that contains the actual bot code called "GoldBrute."
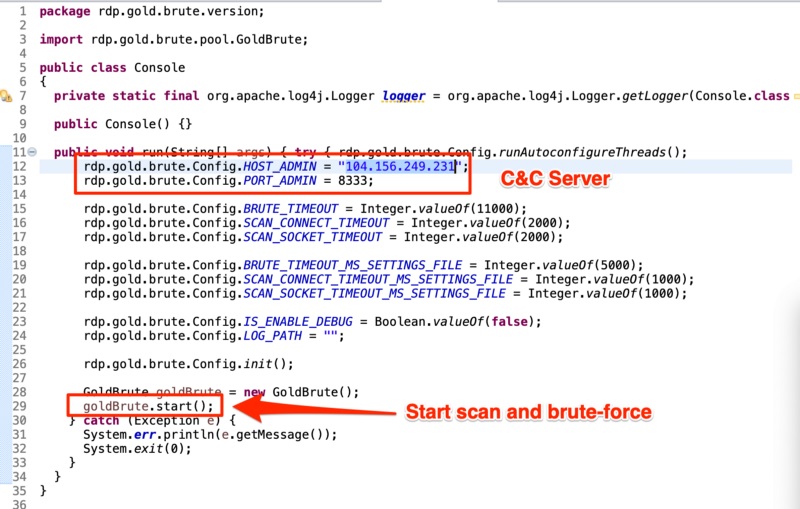 Malicious code associated with GoldBrute (Image: Morphus Labs)
Malicious code associated with GoldBrute (Image: Morphus Labs) Once a vulnerable Windows machine is infected, the bot starts scanning for other IP addresses that also have exposed Remote Desktop Protocol servers, according to Morphus.
When about 80 different IP addresses are found, that list is then sent back to the command-and-control sever. From there, the attackers pick specific machines and target those systems with brute-force methods and credential stuffing to guess the users names and passwords.
This could be a way to avoid detection since authentication attempts appear to come from different IP addresses, Marinho's research found.
While the end-goal of the group is not clear, Marinho speculates that the attackers behind the botnet could sell valid hosts and credentials on various dark web market places. It's also possible that the attackers could change their methods at some point.
"Brute-forcing RDP hosts may be just the current use of this botnet," Marinho says "It can change based on the objectives of the attacker or group behind it. Once they are controlling the nodes, they may change or update the malicious code."
Global Reach
During his analysis, Marinho found a way to modify the code that allowed him to save a list with all the "host+username+password" used by the GoldBrute botnet within his lab computer. This allowed Marinho to create a map that showed all the hosts targeted by the botnet throughout the world.
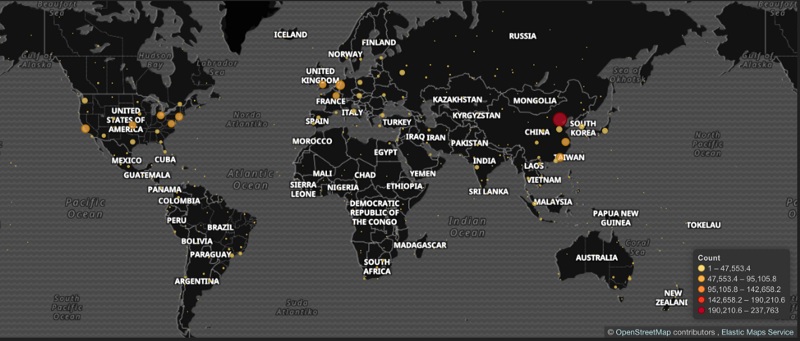 Hosts infected by GoldBrute botnet (Image: Morphus Labs)
Hosts infected by GoldBrute botnet (Image: Morphus Labs) "After 6 hours, we received 2.1 million IP addresses from the C2 server from which 1,596,571 are unique," Marinho writes in his blog post. "Of course, we didn't execute the brute-force phase."

