Breach Preparedness , Breach Response , Data Breach
Analysis of Pre-GDPR Breach Reports in UK Reveals Attack Trends(euroinfosec) • March 13, 2019 British breach trends: Most hackers strike on Saturday; most businesses report breaches on Friday.
British breach trends: Most hackers strike on Saturday; most businesses report breaches on Friday.If you had to guess what day of the week a hacker will hit your organization, the answer might seem obvious: Hackers prefer to strike on Saturday.
See Also: Webinar | The Future of Adaptive Authentication in Financial Services
Research conducted by managed security service provider Redscan confirms it. The firm filed a freedom of information request with the U.K.'s privacy watchdog, seeking anonymized information on cyber incidents reported to the regulator.
Based on information submitted by 181 organizations to the U.K. Information Commissioner's Office for the 12 months leading up to April 2018 - one month before the EU General Data Protection Regulation went into effect - Redscan reported finding five notable data breach detection and reporting takeaways.
1. Hackers Heart Saturday
Attackers were more likely to strike on a Saturday than any other day. This makes obvious sense, since organizations are likely to have fewer employees minding the shop. After a successful attack, hackers would also have more time to explore a network before employees returned to work on Monday.
One caveat, however, is that in some parts of the world, the weekend begins on a Friday. In Bangladesh, for example, Friday is a Muslim day of prayer. Not coincidentally, that's the day attackers hit Bangladesh Bank.
2. Victims Notify on Friday
Want to bury bad news? One age-old strategy long practiced by businesses and politicians in the U.s. is to release bad news on a Friday, after markets have closed, in the hope that it will be old news by Monday. Many breached businesses, likely not coincidentally, publish their first public data breach notification on a Friday (see: Chipotle: Hackers Dined Out on Most Restaurants).
Redscan found that half of all breach reports were submitted to the ICO on a Thursday or Friday, suggesting that this ethos exists in the U.K. as well. "This might be overly cynical, but I suspect that in many cases, breach disclosure on these days may have a deliberate tactic to minimize negative publicity," Mark Nicholls, Redscan's director of cybersecurity, says in a blog post.
3. Detection Delays Common
Redscan found that legal firms were the best at spotting breaches, requiring just 25 days on average, compared to financial services firms, which required 37 days, and organizations classified as "general business," which took 138 days. On average across all three sectors, businesses required 60 days to discover a breach.
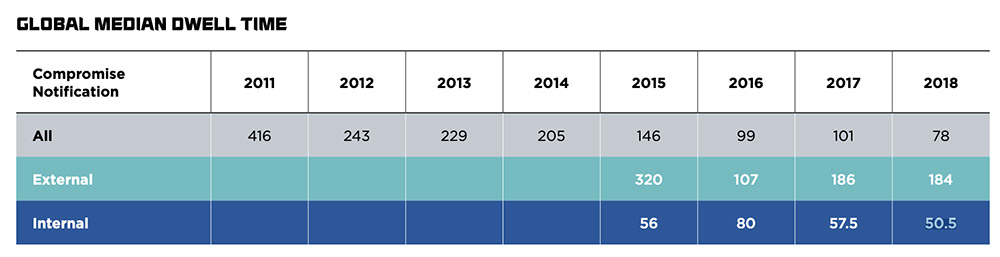 Source: FireEye's Mandiant M-Trends 2019 report
Source: FireEye's Mandiant M-Trends 2019 reportCompare that finding to FireEye's Mandiant 2019 M-Trends report, which found that for breaches that an organization self-discovered in 2018, attackers had been inside the network for an average of 50.5 days. When an organization was tipped off to the breach from an external source, however, attackers had already been inside the network for an average of 184 days.
4. Many Reports Offer Scant Details
Of the breach reports submitted to the ICO, 91 percent lacked critical details, such as the date of the incident and what data attackers stole, Redscan found. For example, 21 percent of firms didn't report a breach incident date to the ICO - suggesting they might not know - and 25 percent failed to disclose when they discovered the breach.
In this respect, the U.K. breach reports mirror U.S. breach reports, which often fail to disclose what got stolen. Perhaps it's because organizations don't know because they've failed to put logging and other monitoring systems in place that would give them the answer.
5. Average Reporting Time: 3 Weeks
Of the 181 data breaches reviewed by Redscan, it found that after a business learned it was breached, it took 21 days, on average, for the organization to file a breach report to the ICO, although one organization took 142 days.
That finding is relevant because only 25 percent of businesses would have complied with GDPR's 72-hour reporting requirement, had it been in effect.
Caveat: GDPR Wasn't in Effect
Until May 2018, the ICO was enforcing Britain's Data Protection Act 1998. But last year, the law was updated - in the form of the DPA 2018 - to include the EU's General Data Protection Regulation, which went into full force on May 25, 2018. The tough new privacy law allows regulators to bring serious fines to bear on organizations that fail to take seriously their responsibility to keep Europeans' data secure, and to only handle it in an approved manner (see: Data Breach Reports in Europe Under GDPR Exceed 59,000).
As noted, the data obtained by Redscan predates GDPR. That's an important point, because before GDPR, many types of organizations did not have to report breaches or comply with a 72-hour notification deadline.
"Given that the data relates to breaches that would fall under the Data Protection Act 1998, it is perhaps unsurprising that the average reporting time was 21 days," Seaton Gordon, an attorney of Pinsent Masons who specializes in cyber law and risk, says in a blog post.
"In the absence of a mandatory requirement to notify the ICO of a breach, it is arguably reasonable for an organization to take adequate time to determine its position prior to notifying a 'serious breach' - this being the relevant threshold when the ICO expected to be notified."
72 Hours or Bust
Under GDPR, however, organizations must report breaches to regulators within 72 hours. Of course, it remains to be seen how well organizations that may have previously spent several weeks preparing their ICO breach notification will comply with this new rule.
 Under GDPR, organizations that suffer certain types of breaches must inform the ICO within 72 hours of learning that they have been breached.
Under GDPR, organizations that suffer certain types of breaches must inform the ICO within 72 hours of learning that they have been breached.
What is clear is that organizations that violate GDPR face fines of up to 4 percent of their annual global revenue or €20 million ($22.6 million) - whichever is greater - as well as other potential sanctions, including losing their ability to process personal data. Separately, organizations that fail to comply with GDPR's reporting requirements also face fines of up to €10 million ($11.3 million) or 2 percent of annual global revenue.
The ICO has been clear that it expects to see more than "something happened and we're still investigating" in that time frame. Organizations that fail to deliver required breach details within 72 hours could also face fines.
 U.K. Information Commissioner Elizabeth Denham
U.K. Information Commissioner Elizabeth Denham
"If, within the 72-hour time limit, a U.K. organization has no clue as to the who, the what, the how of a breach, then it is clear that they do not have the required accountability data checks and balances in place - as required by law," U.K. Information Commissioner Elizabeth Denham said in a speech last December (see: GDPR: 8,000 Data Breach Reports Filed So Far in UK).
"I believe that data breach reporting drives companies to invest in better security and better data governance," she said. "For this reason, I believe breach reporting to be one of the most significant upgrades in the new law."

