Anti-Malware , Cybercrime , Endpoint Security
Attackers Combine Off-the-Shelf Hacking Tools With Legitimate Admin Utilities(euroinfosec) • January 21, 2019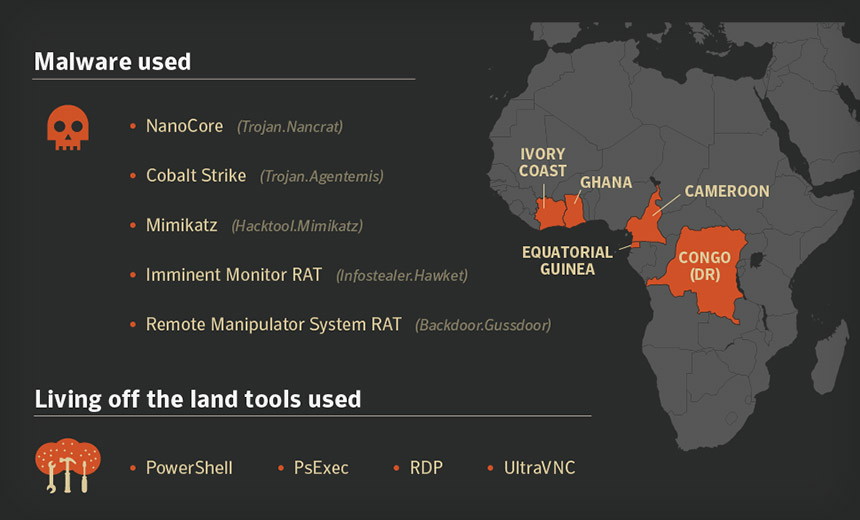 Source: Symantec
Source: SymantecSecurity firm Symantec warns that at least four online attack campaigns, which all may be the work of one group, have been targeting banks in West Africa since mid-2017.
See Also: Live Webinar | Sunset of Windows Server 2008: Migrate with Docker
The attack campaigns have targeted banks in Cameroon, the Democratic Republic of Congo, Equatorial Guinea, Ghana and Ivory Coast, researchers at Symantec say in a blog post.
In a reminder that hackers often do not need to reinvent the wheel, the security firm notes that all of the attacks appear to be using commonly available, off-the-shelf attack tools, together with "living off the land" tactics, which refers to using legitimate tools on an already compromised system to help disguise the attack.
"Commodity malware is readily available on the cyber underground," Symantec says. "While it may not be as powerful or stealthy as custom-developed tools, it does add a certain level of anonymity to attacks, making it harder to link attacks together and attribute them to any one group of attackers."
Previously, Symantec said that it saw few, if any, attackers targeting financial services institutions in West Africa. But in the past 18 months, it's seen an uptick as at least one group - and potentially more than one - has begun targeting organizations in the region.
Four Attack Campaigns Hit West Africa
To date, Symantec says it has seen four distinct attack campaigns targeting West Africa that are continuing and include the use of the following commodity tools or tactics:
NanoCore Trojan: Since at least mid-2017, attackers have targeted organizations in Equatorial Guinea and Ivory Coast with NanoCore malware and have also used the legitimate Microsoft administrator tool PsExec to execute processes on infected systems. "Lure documents used by the attackers referred to a West African bank which has operations in several countries in the region," Symantec says. "Some tools used in these attacks are similar to tools mentioned in a 2017 SWIFT alert, indicating the attackers may have been attempting to perform financial fraud." PowerShell: Beginning in late 2017, attackers targeted organizations in Cameroon, DR Congo, Ghana and Ivory Coast using "malicious PowerShell scripts to infect their targets and also used the credential-stealing tool Mimikatz," Symantec says. Attackers also used an open source, remote administration tool for Windows called UltraVNC, then infected systems with Cobalt Strike malware, which can also provide backdoors onto PCs and download additional malware. "Communication with the C&C server was handled by dynamic DNS infrastructure, which helped shield the location of the attackers." Remote Manipulator System RAT: Also known as Gussdoor, this malware was used by attackers, together with Mimikatz and two custom remote desktop protocol tools, to attack a single organization in Ivory Coast, Symantec says. "Since Mimikatz can be used to harvest credentials and RDP allows for remote connections to computers, it's likely the attackers wanted additional remote access capability and were interested in moving laterally across the victim's network." Imminent Monitor RAT: Also known as Hawket, Symantec says attackers wielding this remote access Trojan in December 2018 began to target banks in Ivory Coast.Symantec could not be immediately reached for comment about the extent to which these attacks were successful, the losses that targeted organizations suffered or how attackers may have stolen funds - potentially, for example, via fraudulent SWIFT messages generated by hacked PCs (see: Malaysia's Central Bank Blocks Attempted SWIFT Fraud).
Hackers Hit Africa
If West Africa had been relatively unscathed by bank hackers, the same cannot be said about all of Africa.
Last October, U.S. cybersecurity firm FireEye warned that a gang of North Korean government hackers, known as APT38, had been waging a sophisticated hacking campaign against banks in Africa and Asia, resulting in the theft of more than $100 million via fraudulent transfers through SWIFT, the global money-transfer network (see North Korean Hackers Tied to $100 Million in SWIFT Fraud).
Also last year, the U.S. Computer Emergency Readiness Team warned in an alert about "malicious cyberactivity by the North Korean government" - which it refers to as Hidden Cobra - that tens of millions of dollars had been stolen from financial services firms in Africa and Asia as part of what US-CERT refers to the "FASTCash" campaign.
US-CERT's alert says the attack campaign, which has been operating since 2016, uses malware designed to "remotely compromise payment switch application servers within banks to facilitate fraudulent transactions."
Publicly Available Hacking Tools
Some bank attacks employ malware that has been customized for the targeted environment. In the case of the $81 million heist from the New York Federal Reserve account of Bangladesh's central bank in February 2016, for example, attackers used custom-designed malware designed to alter SWIFT transactions as well as hide them from printouts. That attack has been widely attributed to North Korean hackers.
But many online attacks, including against banks, continue to use commoditized malware and legitimate administrator tools, according to the U.K.'s National Cyber Security Center, which is part of the GCHQ signals intelligence agency.
In October 2018, NCSC released a joint report on publicly available hacking tools written by cybersecurity authorities in Australia, Canada, New Zealand, the United Kingdom and the United States.
Experts in all five countries warn that the best way to blunt any online attacks today is to monitor for and block commonly used hacking tools.
"Experience from all our countries makes it clear that, while cyber actors continue to develop their capabilities, they still make use of established tools and techniques," according to the report. "Even the most sophisticated groups use common, publicly available tools to achieve their objectives."
Block 5 Common Attack Tools
The report calls out five types of commodity tools that organizations should address:
Remote access Trojans: "A RAT is a program which, once installed on a victim's machine, allows remote administrative control," the report says. "In a malicious context it can, among many other functions, be used to install backdoors and key loggers, take screenshots and exfiltrate data." Commonly seen examples include Adwind RAT, JBiFrost and Gh0st RAT. Web shells: "Web shells are malicious scripts which are uploaded to a target host after an initial compromise and grant an actor remote administrative capability," the report says. "Once this access is established, web shells can also be used to pivot to further hosts within a network." One common example is China Chopper, which the report notes can be spotted because every one of its actions will generate an HTTP POST. In fact, many Web shells appear to be very noisy, which can be used to help spot them. Credential stealers: Mimikatz is a tool first developed in 2007 that's designed to harvest Windows credentials. Its use by attackers remains widespread. "Our cyber authorities have observed widespread use of Mimikatz among hostile actors, including organized crime and state-sponsored groups," the report says. Some defenses against Mimikatz include using up-to-date Windows hardware and software, which includes security features that better protect credentials, as well as never reusing passwords across different administrator accounts, to make them more difficult to crack. Lateral movement frameworks: Designed as a legitimate penetration testing tool in 2015, the PowerShell Empire framework is now used by attackers "to escalate privileges, harvest credentials, exfiltrate information and move laterally across a network," the report says, noting that it "has become increasingly popular among hostile state actors and organized criminals." Organizations can put a range of defenses in place, including removing all old versions of PowerShell, logging all PowerShell usage and using "a combination of script code signing, application whitelisting and constrained language mode." Command and control obfuscators: To disguise their location, attackers may use C2 obfuscators, for example, in the form of the Tor anonymizing network. A tool that first debuted in 2009, called HUC Packet Transmitter, or HTran, is also in wide use. "HTran is a proxy tool used to intercept and redirect Transmission Control Protocol (TCP) connections from the local host to a remote host," the report says. "This makes it possible to obfuscate an attacker's communications with victim networks." To block such activity, network monitoring and firewalls can help.But the report is careful to note that when it comes to network defense, these recommendations should be treated only as starting points. "The individual tools we cover in this report are limited examples of the types used by malicious actors," it says. "You should not consider it an exhaustive list when planning your network defense."

