Governance , Identity & Access Management , Identity Governance & Administration
Researchers Say Other Flaws Also Remain Unpatched(jeremy_kirk) • January 15, 2019 Source: PDC IDenticard
Source: PDC IDenticardResearchers from Tenable Security claim they have found what is essentially a skeleton key for an ID and access control system that could open the doors for anyone, plus other less severe but nonetheless zero-day vulnerabilities.
See Also: Key Drivers to Enable Digital Transformation in Financial Services
Tenable says it has made its findings public after the company that sells the system, PDC IDenticard of Manheim, Pennsylvania, allegedly didn't respond and has not issued patches.
PDC IDenticard, which is part of the Brady Corporation, says on Tuesday that it missed Tenable's communications but that it does plan to fix the problems.
"Regrettably, we overlooked the communication attempts from Tenable," according to a statement from John Fox, a senior product manager. "This is unacceptable for us, and we are currently reviewing our inbound communication practices to ensure it does not happen in the future. We welcome any engagement from Tenable regarding this matter."
PDC IDenticard says it has tens of thousands of customers worldwide, "including Fortune 500 companies, K-12 schools, colleges and universities, medical centers, factories and local, state and federal government agencies and offices."
The skeleton key is a hard-coded credential - a security disaster - within IDenticard's PremiSys software, which is used for creating ID cards, remotely managing physical access, viewing access log records and feeds from on-site video surveillance cameras and many other functions, according to Tenable.
"As it turns out, this hard-coded backdoor allows attackers to add new users to the badge system, modifying existing users, delete users, assign permissions and pretty much any other administrative function," writes James Sebree, a senior researcher with Tenable, in a blog post.
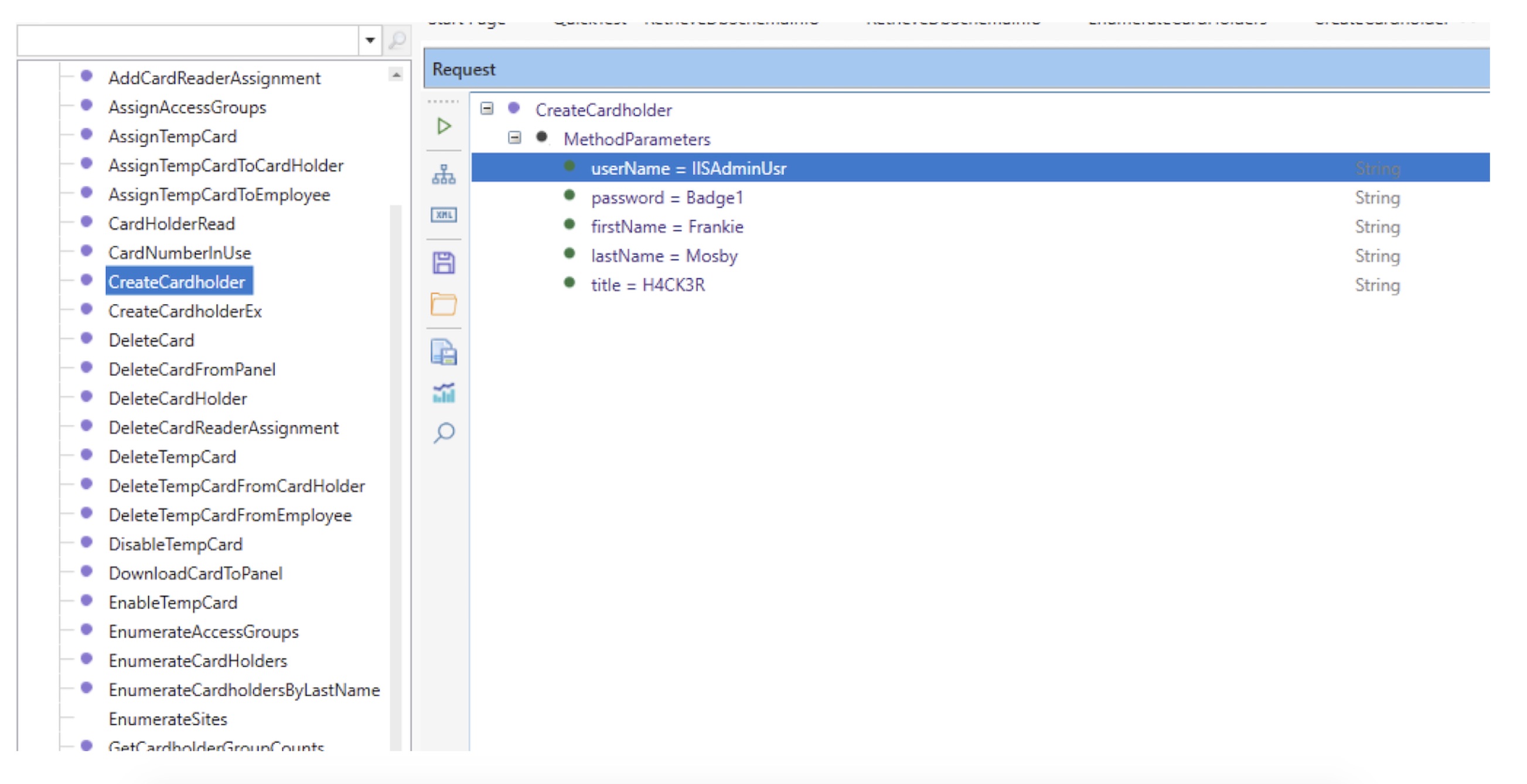 Tenable says the hard-coded credentials could allow someone to add new users to the badge system. (Source: Tenable)
Tenable says the hard-coded credentials could allow someone to add new users to the badge system. (Source: Tenable)In an advisory, Tenable writes that it tried several times to reach PDC IDenticard without a response. Tenable passed the four vulnerabilities onto the U.S. Computer Emergency Readiness Team.
The 90-day disclosure period, a grace period that allows a vendor to develop fixes, expired on Jan. 3. Tenable waited another 11 days before going public. Finders of security vulnerabilities often opt to go public in hopes that public pressure may prompt a vendor to take action.
More Hard-Coded Credentials
Sebree writes that he did not have access to physical badges or components, but instead reverse engineered PremiSys version 3.1.190, a .Net application, and looked at the decompiled codebase.
The hard-coded credentials were found within PremiSysWCFService, which Sebree says appears to be a dashboard for the primary application server and an internal Windows Communication Foundation endpoint for client devices.
But a closer look at the authentication routine found a function that can bypass authentication with the hard-coded credentials. In its advisory, Tenable writes that "users are not permitted to change these credentials."
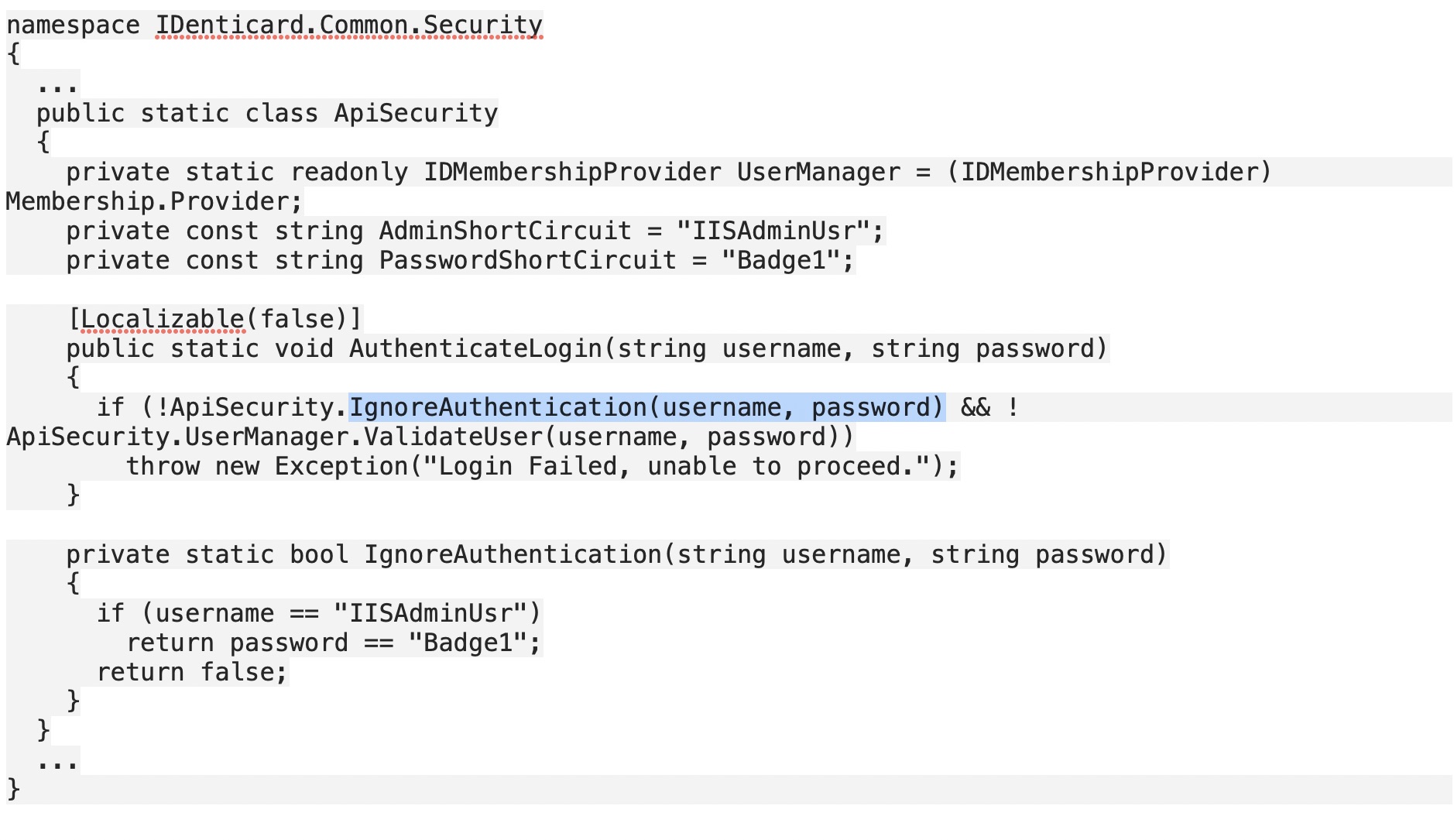 Tenable's James Sebree found a backdoor within the code that could allow an attacker to bypass authentication. (Source: Tenable)
Tenable's James Sebree found a backdoor within the code that could allow an attacker to bypass authentication. (Source: Tenable)"The only mitigation appears to be to limit traffic to this endpoint, which may or may not have further impact on the availability of the application itself," Tenable says. "These credentials can be used by an attacker to dump contents of the badge system database, modify contents, or other various tasks with unfettered access."
Sebree writes that he also found three other issues. PremiSys stores user credentials and other sensitive information as Base64 encoded MD5 hashes (CVE-2019-3907), a weak method, he says.
There's also another hard-coded password issue (CVE-2019-3908). Sebree writes that IDenticard backups are "are stored in an idbak format, which appears to simply be a password protected zip file. The password to unzip the contents is hard-coded into the application ('ID3nt1card')."
The final issue (CVE-2019-3909) concerns the IDenticard service, which uses a default username and password: PremisysUsr/ID3nt1card, Sebree writes. Also, there's a suggestion within the service to meet a longer password requirement by using "ID3nt1cardID3nt1card."
"Users cannot change this password without sending custom passwords to the vendor directly in order to receive an encrypted variant to use in their configurations," Sebree writes. "These known credentials can be used by attackers to access the sensitive contents of the databases."
PDC Identicard says it takes Tenable's findings "seriously" and plans to use the information for its product development cycle.
"The safety and security of our customers is our first priority," Fox says. "As part of our ongoing agile software development process, we anticipate releasing improvements in the near term and will keep our customers updated with how those improvements address Tenable's concerns."
Beware Default Configurations
All of this is really bad news if an organization has PremiSys directly facing the internet or has it linked to other internal systems that could be at risk of a breach.
"While bad systems should be isolated from the rest of the network, we all know that not everyone is going to follow best practices," Sebree writes.
There are broader concerns with how ID and badge systems are installed, Sebree writes. Contractors set up the systems with default settings and then leave.
"The customer uses what they need while leaving many features unused but still enabled," he writes. "This leads to unnecessary cyber exposure of critical physical security infrastructure, and a possible entry point into the digital infrastructure."
Sebree points out that administrators are unlikely aware of all of the features of such systems.
"In a production environment, the attack surface of this single service would be absolutely massive," Sebree writes. "If a company is depending on it for physical security, simple and critical software errors like these have to be taken seriously."

