Authentication , Data Loss , Forensics
Popular Password Managers for Windows Fail to Tidy Up Before Locking Up Shop(jeremy_kirk) • February 20, 2019
An audit of some popular password managers for Windows has revealed concerning weaknesses. Luckily, none of the problems are showstoppers that should put people off using such applications.
See Also: Live Webinar: Building Secure Delivery Pipelines with Docker, Kubernetes, and Trend Micro
Baltimore-based Independent Security Evaluators on Tuesday released the results of their look into the Windows versions of LastPass, KeePass, Dashlane and 1Password. The researchers found that the applications failed to scrub bits of data left in memory, which pose a risk if an attacker has physical access to the machine.
"We were surprised in the inconsistency in secrets sanitization and retention in memory when in a running unlocked state and, more importantly, when placed into a locked state," ISE writes in its report. "If password managers fail to sanitize secrets in a locked running state, then this will be the low hanging fruit that provides the path of least resistance to successful compromise of a password manager running on a user's workstation."
Password managers are incredibly valuable tools in the age of data breaches. Most have built-in password generators, which can create and manage a unique password for every different site or service a user uses. That's important because account takeovers are often caused by people reusing passwords that have already been stolen by hackers. Many information security experts also recommend that everyone use a password manager.
But as with any software, there are risks. Password managers usually get unlocked with a master password, which is the key to all of the other sensitive data and thus a potential single point of failure. Like any application, password managers also interact with a computer's operating system and memory, so it's important for maximum security that the applications leave as few digital traces behind as possible.
The developers of password managers do care about security and have hardened their infrastructure and properly use strong cryptography, says Adrian Bednarek, a senior security analyst and researcher with ISE. But clients and users remain the weakest link, which is why traces of password data on a computer could pose a risk if it was compromised, he says.
"We wanted to bring to light that password managers running on users computers should employ all possible defenses to protect them against existing and emerging threats," Bednarak says.
1Password: Not Enough Scrubbing
So here's the good news, in short form, first: All of the tested applications adequately protected their stored passwords and master passwords when they were not running. Even if an attacker had access to a local machine, no useful information could be collected.
Less encouraging, however, was a look at when password managers had either been unlocked or else unlocked and locked again.
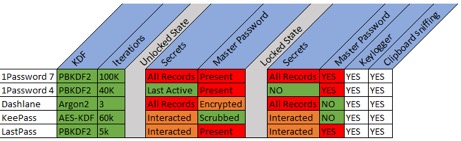 ISE found all of the tested password managers left data in memory. (Source ISE)
ISE found all of the tested password managers left data in memory. (Source ISE)Versions of 1Password appear to have had the most problems. ISE found 1Password4 leaves an obfuscated version of the master password in memory after the application has been unlocked. Although it was obfuscated, ISE was able to reverse two strings to reveal the clear text.
The current release, 1Password7, was more problematic. The lock mechanism was essentially ineffective, ISE writes.
"We found that 1Password7 scrubs neither the individual passwords, the master password, nor the secret key (an extra field introduced in 1Password6 that combines with the master password to derive the encryption key) from memory when transitioning from unlocked to locked," ISE writes.
The only way to clear that data is to quit 1Password7 completely, which then flushes the data from memory. ISE also stumbled across a kernel mode exception bug in 1Password7 caused by an unrelated hardware issue.
"While examining this memory dump file, we came across our secrets that 1Password7 held cleartext [sic], in memory, in a locked state when the stop error occurred," ISE writes.
1Password had to make development tradeoffs that limited its ability to clear data from memory immediately, says Jeffrey Goldberg, who is 1Password's chief defender against the dark arts.
Long term, we may not need to make such a tradeoff," Goldberg tells ISMG. "But given the tools and technologies at our disposal, we have had to make a decision as to how best to keep our users secure. I stand by our decision."
Goldberg says that the realistic threat from the issues are limited. Further, no application can run safely on a computer where an attacker has access to memory. 1Password addressed the research on it forum.
"This is a well-known issue that's been publicly discussed many times before, but any plausible cure may be worse than the disease," Golderberg says.
Dashlane, KeePass, LastPass
Dashlane also exposes its full password database in a locked and unlocked state, ISE found. Usually, only the last password a person has used is left in memory. But for some reason, ISE found that if a user updated an entry, the entire database is exposed in clear text in both a locked and unlocked state.
Dashlane CEO Emmanuel Schalit tells ISMG that the risk outlined by the research - where someone gains local control of a machine and accesses data in memory - is a weakness shared by any application on a computer. He warned that the research shouldn't put off people from using password managers, as the benefits outweigh the risks.
"It is generally well known in the world of cybersecurity that the above scenario is an extreme one, in the sense that no mechanism can protect the digital information on a device if that device is already entirely compromised," Schalit says.
KeePass exposes some clear text data in memory, but on the positive side, the master password is unrecoverable. Although KeePass is supposed to wipe out data, ISE writes that KeePass indicated that Windows OS APIs "may make copies of various memory buffers which may not be exposed to KeePass for scrubbing."
 Password managers are used by tens of millions of users, making their security critical. (Source: ICE)
Password managers are used by tens of millions of users, making their security critical. (Source: ICE)Decrypted passwords also continue to live in memory in LastPass version 4.1.59, which is not the latest version. The master password also "leaked into a string buffer in memory and never scrubbed, even when LastPass is placed into a locked state," ISE writes.
KeePass's developer, Dominik Reichl, says what ISE found is a well-known issue with password managers. KeePass discusses it in its technical notes.
LastPass has already addressed the findings.
On Wednesday, a LastPass spokeswoman said the bugs have been addressed in an update for LastPass for Applications, which is a paid-for feature for LastPass. She added that the version tested by ISE is used by less than 0.2 percent of its users and that "we have no indication or reason to believe that any sensitive LastPass user data has been compromised."
The spokeswoman also said that attackers would need local and administrator access to a compromised computer. That's an important point that applies to all of the problems found by ISE. None of the weaknesses found by ISE could be remotely exploited over the internet, which would be a far more dangerous scenario.
Still, ISE points out that it's common for administrators to image machines that have been compromised by malware as part of incident response. That means memory files, crash logs or debugging logs may be copied and stored in other places. If this happened to someone running 1Password7, for example, the person "should assume that all secrets have been compromised," the report says.
Bednarek adds: "A locked password manager should not expose secrets, and we're glad to see steps are being taken to reduce the likelihood of sensitive information exposure to adversarial activity."

