Business Continuity/Disaster Recovery , Cybercrime as-a-service , Endpoint Security
But GandCrab Gang Appears to Already Be Testing New Decryptor-Proof Version(euroinfosec) • February 19, 2019 A new, free decryptor available via No More Ransom will unlock systems infected with GandCrab, up to version 5.1
A new, free decryptor available via No More Ransom will unlock systems infected with GandCrab, up to version 5.1Good news for many victims of GandCrab ransomware: There's a new, free decryptor available from the No More Ransom portal. And it will unlock systems that have been crypto-locked by the latest version of the notorious, widespread ransomware.
"In addition to versions 1, 4 and early versions of 5, the new tool resolves infections with version 5.0.4 through 5.1 - the latest version developed by the cybercriminals," says the EU's law enforcement intelligence agency, Europol.
No More Ransom is a public/private portal that was launched in 2016 by Europol and Dutch National Police, together with Kaspersky Lab and McAfee. It's hosted by Amazon Web Services and Barracuda Networks. The effort now has many more partners.
The latest GandCrab decryptor, for example, was developed by the Romanian Police, working with security firm Bitdefender and Europol, which says the effort also received notable support from law enforcement authorities in Austria, Belgium, Cyprus, France, Germany, Italy, the Netherlands, U.K. and Canada, as well as from the FBI.
Romanian Police and Bitdefender have declined to comment about how their decryptor works so they don't tip their hand to the GandCrab gang. But experts say that previous versions of the decryptor exploited the poor quality of GandCrab's cryptographic implementation.
GandCrab appears to have a solid marketing team. The gang built buzz last September by announcing a "crypter competition" to help decide which malware crypter service it should partner with, according to McAfee. A service called NTCrypt eventually won.
But security experts say GandCrab's software developers are not the world's finest. "The group behind GandCrab has achieved cult status in underground forums; the authors are undoubtedly confident and have strong marketing skills, but flawless programming is not one of their strengths," researchers at McAfee said in a blog post last October.
Ransom Demanded in Dash or Bitcoin
Police say that anyone whose system gets crypto-locked by GandCrab is then faced with a ransom demand that can range from $300 to $6,000. Payments are only accepted in either dash or bitcoin cryptocurrency, to make the transactions tougher for authorities to trace. Anyone who pays in bitcoin, however, is charged a 10 percent premium, because dash is tougher to trace (see: Ransomware Victims Who Pay Cough Up $6,733 (on Average)).
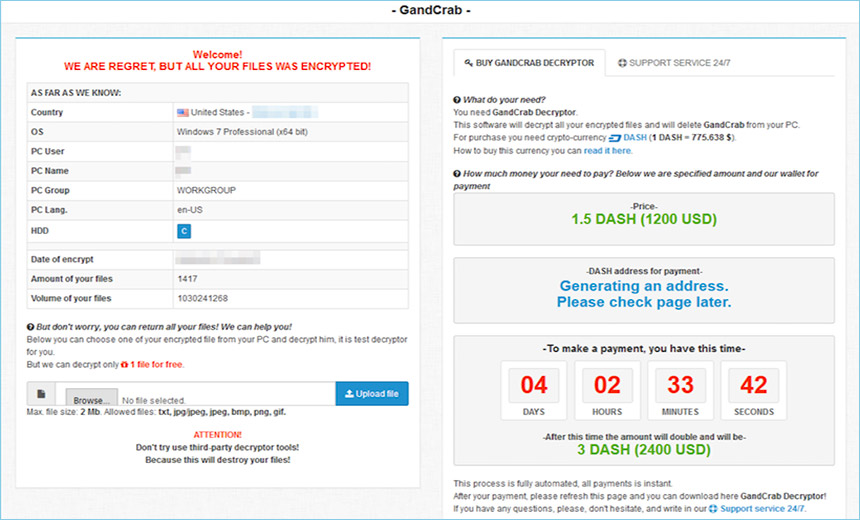 A GandCrab ransom-payment page, reachable only via a hidden TOR site (Source: Malwarebytes)
A GandCrab ransom-payment page, reachable only via a hidden TOR site (Source: Malwarebytes)GandCrab remains a top threat because of its ability to not just encrypt PCs but also network shares, and it also recently gained the ability to automatically map network shares, Adam Kujawa, director of Malwarebytes Labs, told Information Security Media Group last month.
"It also uses some pretty serious RSA encryption, so it's not just some cheap junk, like in the first version," he said. "It's definitely now a far more difficult encryption scheme to crack."
Cat-and-Mouse Games Continue
This is the third such GandCrab decryptor to have been developed. The first tool was released in February 2018, and a second last October, which covered all but two versions of the malware that had been found in the wild (see: Fresh GandCrab Decryptor Frees Data for Free).
"Downloaded more than 400,000 times so far, these two tools have helped close to 10,000 victims retrieve their encrypted files, saving them some $5 million in ransomware payment," Europol says.
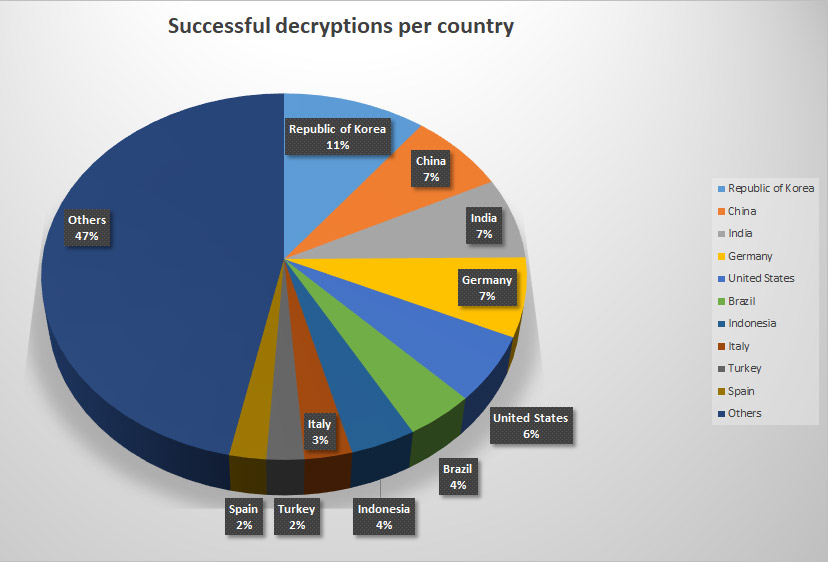 Successful GandCrab decryptions prior to Feb. 19, 2019 (Source: BitDefender)
Successful GandCrab decryptions prior to Feb. 19, 2019 (Source: BitDefender)Law enforcement authorities likely will wind up releasing more decryptors as attackers update their code.
Public Ransomware Enemy No. 1
Ransomware may be less widespread than it used to be, thanks to the rise of crypto-mining malware. But crypto-locking malware remains a threat, and GandCrab was the most prevalent strain seen in 2018, notching up more than 500,000 victims since it first appeared in January 2018, Europol says.
Whereas earlier, multiple ransomware families competed, in 2018 "GandCrab basically took over the whole market of ransomware as a service," thanks to its marketing prowess, Tamas Boczan, a senior threat analyst at VMRay, told ISMG in November 2018.
Boczan, who has been tracking the evolution of GandCrab, said that while it began as very basic ransomware, it's evolved to the point where it now "uses multiple exploits and anti-reversing tricks."
Boczan says he's verified that the latest decryptor works with version 5.1 of GandCrab, which is the one that Europol says is now being seen in the wild. But he says that on Monday, he began seeing GandCrab version 5.2 getting uploaded to VirusTotal.
"I haven't verified if it was used in the wild yet," he tells ISMG, but says the timing of the release is notable. "I think they were aware that a decryptor was coming."
Affiliate Program
GandCrab is run as an affiliate program. The core gang creates the code and gives every "affiliate" who signs up a customized version of the ransomware to distribute; it contains a unique affiliate ID. Anytime a victim pays, the gang takes their cut and remits the rest to the affiliate.
Affiliates have continued to refine how they infect victims. "Last year, some GandCrab affiliates began attacking organizations via exposed remote desktop protocol instances, or by directly logging in with stolen domain credentials," Bogdan Botezatu, a senior e-threat analyst at Bitdefender, says in a blog post. "After authenticating on a compromised PC, attackers manually run the ransomware and instruct it to spread across the entire network. Once the network is infected, the attackers wipe their traces clean and contact the victim with a decryption offer."
More recently, some attackers have also exploited vulnerabilities in remote IT support software to install GandCrab inside victim networks, ZDNet has reported.
VMRay's Boczan says the increased use of RDP as an attack vector makes it more complicated to know exactly which version or versions of GandCrab might be prevalent in the wild (see: Stolen RDP Credentials Live On After xDedic Takedown). "They like targeted attacks these days - via RDP - so it's more difficult to tell than for spam campaigns," he says.
Prevention Remains Best Defense
For anyone who hasn't yet been hit by ransomware and learned valuable information security lessons the hard way, Europol says prevention remains the best defense.
"Users are strongly advised to use a security solution with layered anti-ransomware defenses, regularly back up their data and avoid opening attachments delivered with unsolicited messages," Europol says.
Experts say these data backups should be stored offline - off the network and not on any always-on cloud services - because many strains of ransomware can crypto-lock a system and everything else to which it connects.
"If you have a security solution, make sure it is up to date and has layered defenses against ransomware," says Bitdefender's Botezatu. "The better it is at detection, the lower your chances of infection. Also, make sure you are running the latest version of your OS and third-party software. If you don't have a security solution, get one now. It helps a lot, and it's way less expensive than a $600 ransom payment."

