Cybercrime , Fraud , Fraud Management & Cybercrime
Separately, Texas City's Operations Disrupted by Crypto-Locking Ransomware(euroinfosec) • January 15, 2019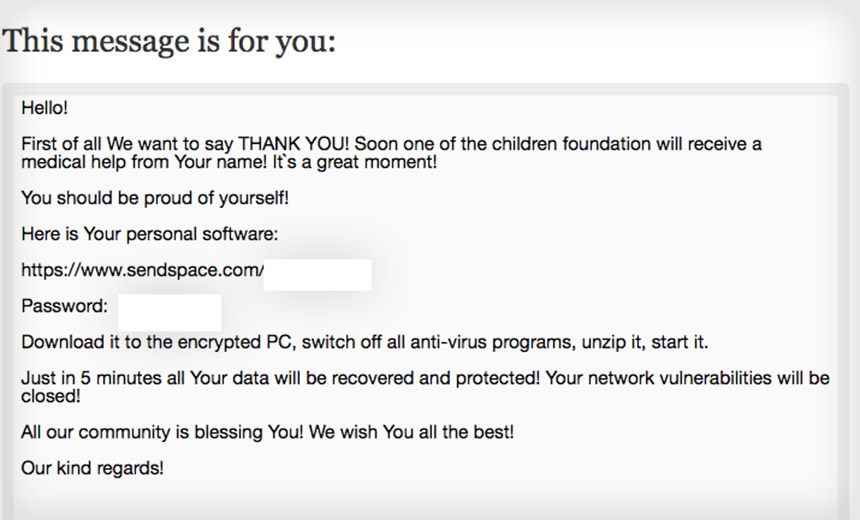 Attackers using CryptoMix ransomware falsely claim that ransoms go toward paying ill children's medical treatments. (Source: Coveware)
Attackers using CryptoMix ransomware falsely claim that ransoms go toward paying ill children's medical treatments. (Source: Coveware)Ransomware attacks continue, with yet another city saying its operations have been disrupted by crypto-locking malware. As that demonstrates, ransomware remains a formidable threat, with attackers continuing to score notable victims, including Chicago-based Tribune Publishing, which was hit last month by a suspected Ryuk ransomware infection (see: Suspected Ransomware Outbreak Disrupts US Newspapers).
See Also: Live Webinar: Building Secure Delivery Pipelines with Docker, Kubernetes, and Trend Micro
Ryuk is one of numerous types of ransomware - including SamSam - that have been seen before, demonstrating that many existing strains of crypto-locking malware continue to be able to shut down organizations and municipalities. Also, the notorious GandCrab ransomware-as-a-service offering, which was a dominant strain of ransomware seen throughout 2018, has recently been getting installed in the noisy second phase of information-stealing attacks.
Some criminals have been recycling attack tactics too. Attackers wielding CryptoMix, for example, have been continuing to claim in fresh attacks that victims' ransom payments will be used to fund medical treatments for seriously ill children, which is a lie.
On the good-news front, however, technology giant Cisco has released a free decryptor for some types of PyLocky ransomware infections, and cryptographic flaws in previously seen strains of CryptoMix, which means that such infections can also be potentially cracked for free.
Ransomware Comes to Del Rio
One of the latest high-profile ransomware victims to come to light was the city of Del Rio, Texas - population: 36,000. On Thursday, city officials issued a press release warning that the city had fallen victim to a crypto-locking ransomware outbreak that disabled servers at city hall.
"The first step in addressing the issue was for the City's M.I.S. (Management Information Services) Department to isolate the ransomware which necessitated turning off the internet connection for all city departments and not allowing employees to log into the system. Due to this, transactions at City Hall are being done manually with paper," the city said. "The second step the city took was to go to the FBI to report the ransomware, after which the city was referred to the Secret Service."
City officials couldn't immediately be reached for comment about whether they restored systems from backups, considered paying attackers, or why the FBI referred officials to the Secret Service, although one obvious explanation would be the ongoing government shutdown (see: Government Shutdown: Experts Fear Deep Cybersecurity Impact).
City spokeswoman Victoria Vargas told BleepingComputer that as a result of the attack, about 30 to 45 systems had been deactivated, which led to employees digging out typewriters from closets to keep records. Unusually, Vargas said attackers didn't include a cryptocurrency wallet or email address with their ransom demand, but rather a phone number.
Extortionists Claim Ransoms Fund Treatments
Separately, attackers wielding an obscure type of ransomware called CryptoMix have been attempting to coerce victims into paying ransoms by feeding them children's medical details.
Ransomware response firm Coveware says that recent ransom notes from attackers wielding CryptoMix crypto-locking ransomware claim that payments will go to what turns out to be a fictitious charity for children with cancer. But to make their cover story look real, the attackers have lifted real details from crowdfunding sites devoted to helping to fund medical treatments for children who have cancer.
"We identified legitimate crowdfunding pages for the children whose images matched those in the ransom notes," Coveware says in a blog post. "We also notified the families of the children whose images could be positively identified. Despite the upsetting nature of the news, we felt that the families had a right to know."
Any CryptoMix victim who emails the attackers, using the contact information contained in the ransom note left on their PC, will receive a message back via a site called OneTimeSecret, sharing the bitcoin wallet to which the victim should send their ransom payment, as well as providing more information about the supposed charity, Coveware says.
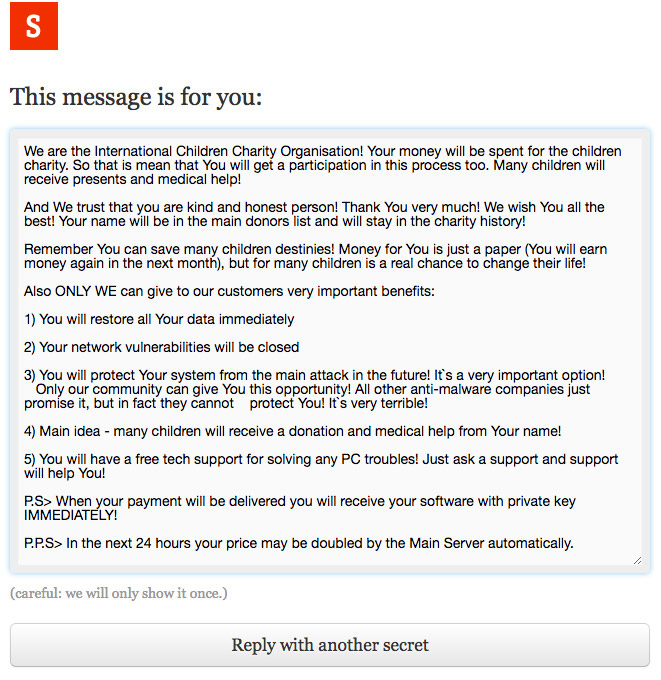 Message sent by the attackers behind CryptoMix to ransomware victims (Source: Coveware)
Message sent by the attackers behind CryptoMix to ransomware victims (Source: Coveware)Such tactics again demonstrate how criminals so often attempt to manipulate psychological levers that an be used to prey on victims' subconscious impulses (see: Crime: Why So Much Is Cyber-Enabled).
"We are guessing this tactic is meant to assuage the moral hazard associated with paying a ransom," Coveware says. "It goes without saying that these cybercriminals did think this through. It is poignantly obvious that the charity is fake, and that the details of the child's case are lifted from other sites."
CryptoMix Cracked by CERT.PL
This isn't the first time that CryptoMix attackers have attempted to socially engineer victims.
In 2017, Poland's Computer Emergency Response Team, CERT.PL, warned that CryptoMix - aka CryptFile2, Zeta, CryptoShield - ransomware, at the time being served by the Rig-V exploit kit, was being used by attackers who also claimed to be working on behalf of a charity that sponsors "presents and medical help for children," Jarosław Jedynak, an IT security engineer for CERT.PL, said in a blog post.
Unusually, rather than using an automated payment portal, attackers told victims to email them to arrange payment and decryption. Together with the ransom demand - for a massive six bitcoins - Jedynak said this was evidence of what looked like a poorly planned and technologically unsophisticated effort, "especially considering that CryptoMix is really primitive under the hood."
CERT.PL reported that at least one supposed victim who paid had never received a decryption key, based on an online post they made:
we were infected and they asked for 10 bitcoins, after some negotiations the price was lowered to 6 bitcoins. they provided 1 decrypted file to prove concept. we paid 6 bitcoins and they asked for another .6 as the c&c server will not provide the key due to late payment. after promptly paying another .6 bitcoins (about $4800 in total) there has been no communication from them! its been 2 weeks and nothing.
WHATEVER YOU DO, DO NOT TRUST THEM, THEY WILL NOT DECRYPT YOUR FILES!!!!
"We can't verify if this is true, but it sounds plausible - if someone is desperate enough to pay 6 bitcoins for his files, he probably can be coerced into paying even more," Jedynak said. "As usual, we discourage anyone from supporting the criminals by paying the ransom."
Due to a cryptographic flaw in how the developer behind CryptoMix implemented encryption, CERT.PL said it was able to automatically decrypt CryptoMix, but only in some cases.
Working with Czech security firm Avast, there's also a free decryptor, first released in 2017, for systems that were cryptolocked by CryptoMix while they were offline.
"Once CryptoMix infects a machine, it tries to communicate with its Command and Control (C&C) server to establish a key to encrypt files (the AES-256 algorithm is used). However, if the server is not available or if there is a connection issue (e.g. blocked communication by a firewall), the ransomware will encrypt files with one of its fixed keys, or 'offline key,'" said malware analyst Jakub Kroustek, who leads Avast's threat intelligence team, in a blog post.
"Our decryption tool for CryptoMix can decrypt files that were encrypted using the 'offline key,'" he said. "In cases where the offline key was not used to encrypt files, our tool will be unable to restore the files and will not modify any files."
Cisco Releases Free PyLocky Decryptor
In other ransomware decryption news, Cisco's Talos security team has released a free decryptor for PyLocky ransomware, developed by one of its security researchers, Mike Bautista.
"PyLocky is a family of ransomware written in Python that attempts to masquerade as a Locky variant," Ashlee Benge, a threat research engineer for Cisco Talos, says in a blog post (see Ransomware Crypto-Locks Port of San Diego IT Systems).
After crypto-locking a system, PyLocky leaves a ransom note demanding payment in bitcoin for the promise of a decryption key.
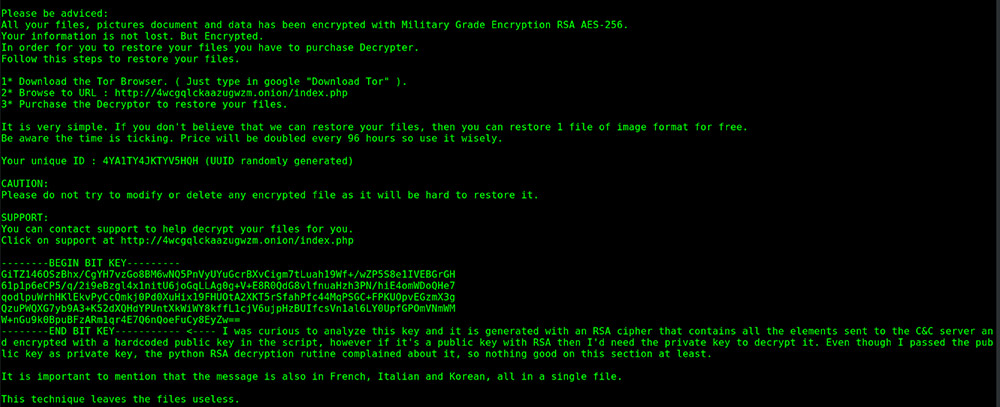 Sample of a PyLocky ransom note (Source: Cisco Talos)
Sample of a PyLocky ransom note (Source: Cisco Talos)Cisco's decryption tool can crack the ransomware, but it carries a significant caveat. "Because our tool requires the capturing of the initial PyLocky command and control (C2) traffic of an infected machine, it will only work to recover the files on an infected machine where network traffic has been monitored," Benge says. "If the initial C2 traffic has not been captured, our decryption tool will not be able to recover files on an infected machine. This is because the initial callout is used by the malware to send the C2 servers information that it uses in the encryption process."
As always, security experts note that the best defense against ransomware is to have security tools in place to block it, as well as up-to-date backups stored on disconnected servers, in the event that systems do become infected, so they can be wiped and restored. "Talos encourages users never to pay an attacker-demanded ransom, as this rarely results in the recovery of encrypted files," she says. "Rather, victims of this ransomware should restore from backups if their files cannot be decrypted."
Vidar Loads GandCrab
In other ransomware news, security firm Malwarebytes warns that an attacker has been using the Fallout exploit kit to distribute new malware called Vidar, which is in turn pushing a ransomware-as-a-service offering called GandCrab that security experts say was particularly aggressive throughout 2018 (see: GandCrab Ransomware: Cat-and-Mouse Game Continues).
An in-depth Vidar analysis published last month by security researcher Fumik0_ i reported that the malware, which appears to be based on previously seen malware called Arkei, includes the ability to grab screenshots, search for specific documents, steal two-factor authentication credentials and numerous types of cryptocurrency wallets, as well as load additional malware.
Vidar retails for $250 to $700 on cybercrime forums, Fumik0_ reported.
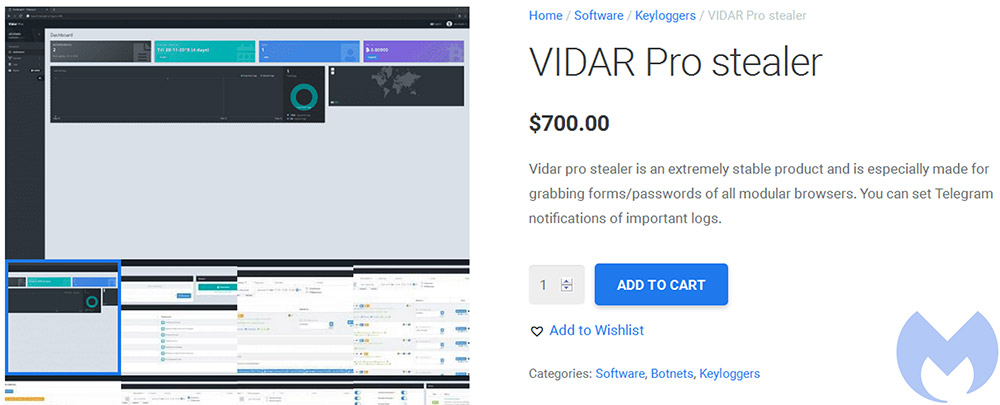 Advertisement for Vidar on a cybercrime forum (Source: Malwarebytes)
Advertisement for Vidar on a cybercrime forum (Source: Malwarebytes)This isn't the first time that GandCrab has been pushed via malware distributed by the Fallout exploit kit (see: GandCrab Ransomware Partners With Crypter Service).
In this case, however, GandCrab appears to get installed via Vidar, which is being pushed via malvertising, aka malicious advertising, Jérôme Segura, a security researcher at Malwarebytes, says in a blog post.
 Message left on a systems crypto-locked with GandCrab (Source: Malwarebytes)
Message left on a systems crypto-locked with GandCrab (Source: Malwarebytes)The intent appears to be a one-two punch: ransacking a system for valuable data, then attempting to further monetize the attack by seeking a ransom. "Victims get a double whammy," Segura says. "Not only are they robbed of their financial and personal information, but they are also being extorted to recover the now encrypted data."
Segura says the attacks are a reminder that while there may be fewer ransomware attacks - or new strains - than in previous years, "it remains a threat."

