Breach Response , Cyberwarfare / Nation-state attacks , Data Breach
Tribune Media Suspects Ryuk Ransomware Hit Publishing and Production Systems(euroinfosec) • December 31, 2018 The Chicago Tribune, Los Angles Times and other newspapers' print editions have been disrupted by a malware outbreak. (Source: Kiosko.net)
The Chicago Tribune, Los Angles Times and other newspapers' print editions have been disrupted by a malware outbreak. (Source: Kiosko.net)Production of newspapers owned by Chicago-based Tribune Publishing have been disrupted after malware began infecting the company's publishing and printing systems.
See Also: Third-Party Cyber Risk Management - A Data-Driven Approach
Multiple sources quoted by Tribune newspapers have suggested that the malware infection, which began late on Thursday, involved ransomware known as Ryuk, which may tie to North Korean operators. But security experts say it's far too soon to label Tribune's ransomware outbreak as anything more than an opportunistic infection, and note that anyone can potentially obtain and use malware, irrespective of their identity, political affiliation or other motivations (see Stop the Presses: Don't Rush Tribune Ransomware Attribution).
Tribune Publishing says the malware infection, which it discovered on Friday, compromised no financial information and had no impact on its websites, but did disrupt systems that it uses to publish and print its newspapers. All of its newspapers were affected.
"This issue has affected the timeliness and in some cases the completeness of our printed newspapers," Tribune Publishing spokeswoman Marisa Kollias said in a statement released on Saturday, the Chicago Tribune reported. "Our websites and mobile applications however, have not been impacted."
Kollias said the company is "making progress" with restoring systems. "There is no evidence that customer credit card information or personally identifiable information has been compromised," she said.
Formerly known as Tronc, Tribune Publishing owns the Chicago Tribune, as well as Chicago suburban newspapers Lake County News-Sun and Post-Tribune; Los Angeles Times; The Baltimore Sun; the New York Daily News; Hartford Courant; Orlando Sentinel; the Capital Gazette in Annapolis, Maryland; The Morning Call in Allentown, Pennsylvania; and in Virginia, the Daily Press in Newport News, and The Virginian-Pilot in Norfolk.
The Chicago Tribune reported that its Saturday edition had been published "without paid death notices and classified ads," due to the malware infection, and that some Saturday newspapers in other markets were delivered in a "slimmed-down version" on Sunday.
The Los Angeles Times and San Diego Union-Tribune also reported experiencing disruptions due to the malware, resulting in delays in home deliveries, or no deliveries at all. Tribune sold both newspapers to biotech billionaire Patrick Soon-Shiong for $500 million in June. But as part of a transition arrangement, it's continuing to support the newspapers, including their printing operations.
"Because of a major computer breakdown that affected our printing and deliveries, many of you did not receive your copy of Saturday's Los Angeles Times," Norman Pearlstine, executive editor of the newspaper, and Chris Argentieri, its chief operating officer, said in an apology posted on Saturday.
"We are also aware that many of you have been unable to report your missed delivery," they wrote. "We apologize for the inconvenience and thank you for your patience as we actively work to resolve these issues and restore timely service to our customers."
The newspaper distribution problems also affected the west coast editions of The New York Times and The Wall Street Journal, which share the same printing presses.
Tribune said it has alerted the FBI to the incident. "We are aware of reports of a potential cyber incident affecting several news outlets, and are working with our government and industry partners to better understand the situation," DHS spokeswoman Katie Waldman said in a statement, Reuters reported.
Ryuk Infection Suspected
Citing unnamed source with knowledge of the investigation, multiple Tribune outlets have reported that the malware appeared to be ransomware called Ryuk, with one source noting that crypto-locked files having been renamed with a ".ryk" extension. But the sources have noted that no ransom demand had been received.
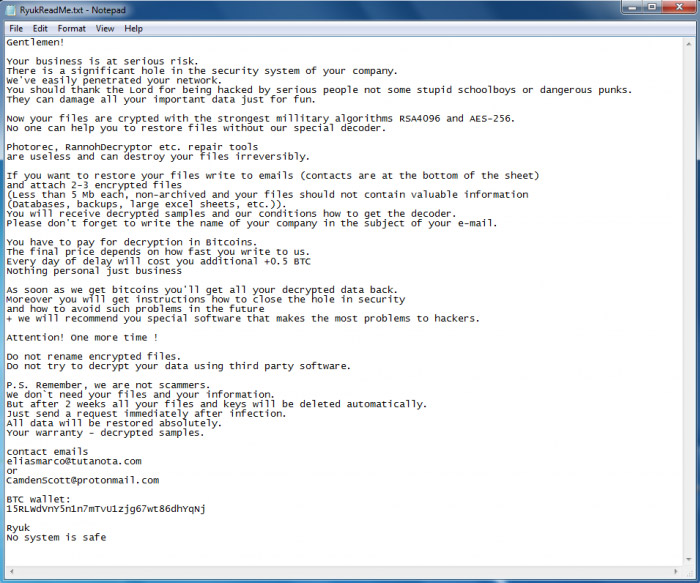 Ransom note left in some Ryuk attacks - although Tribune Media says it has seen no ransom note. (Source: Check Point)
Ransom note left in some Ryuk attacks - although Tribune Media says it has seen no ransom note. (Source: Check Point)Ryuk has been used to infect organizations across numerous verticals since it was first spotted on Aug. 13. "Our first discovery of Ryuk was during an incident response engagement involving a medical research equipment design and manufacturing company headquartered in the U.S., with locations in Europe," Tim Otis, a Check Point incident response leader, told Information Security Media Group in August (see Alert: 'Ryuk' Ransomware Attacks the Latest Threat). "We have had additional Ryuk cases involving other verticals, such as law firms and convenience store chains both in the United States and abroad."
—Check Point
Check Point in August released a report into Ryuk, later cited in a U.S. government alert, noting that the ransomware appeared to be based on the Hermes ransomware, which has been widely tied to Lazarus, which is a group of hackers, tools and attack campaigns that have suspected ties to the Pyongyang-based government of North Korea (see Lazarus 'FASTCash' Bank Hackers Wield AIX Trojan).
But the code similarity between Ryuk and Hermes is no smoking gun, Check Point cautioned. The similarity "leads us to believe that the current wave of targeted attacks using Ryuk may either be the work of the Hermes operators - the allegedly North Korean group - or the work of an actor who has obtained the Hermes source code," Check Point's report said.

