Endpoint Security , Endpoint Security , Geo Focus: The United Kingdom
Tool Hides Virtual Volumes But Leaves Linux Looking 'Bit-for-Bit' Normal(euroinfosec) • December 28, 2018 Photo: Fanghong, via Wikimedia Commons
Photo: Fanghong, via Wikimedia CommonsSteganography is the practice of hiding messages or information in plain sight, especially inside other data or images. And a new toolset, which debuted earlier this month at the Black Hat Europe conference in London, suggests steganography is going to get much more difficult to spot in the future.
See Also: Live Webinar | Levers of Human Deception: The Science and Methodology Behind Social Engineering
Digital steganography has already been put to use by bad actors. In 2013, for example, Russian security firm Kaspersky Lab and Budapest-based CrySyS Lab discovered an online espionage campaign that used attack code called MiniDuke, which looked to specified Twitter accounts to retrieve command-and-control instructions.
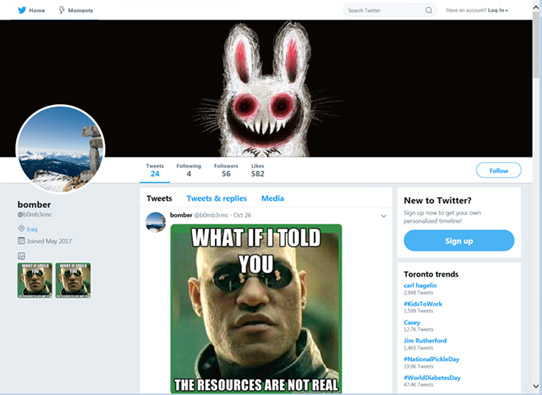 Trend Micro recently discovered that Twitter memes were being used to remotely control PCs infected with Berbomthum malware. (Source: Trend Micro)
Trend Micro recently discovered that Twitter memes were being used to remotely control PCs infected with Berbomthum malware. (Source: Trend Micro)More recently, security firm Trend Micro reported finding an attack campaign that used a meme drawn from the 1999 science fiction film "The Matrix" to send remote-control instructions for PCs infected with Berbomthum malware (see Twitter Sees Signs of State-Sponsored Attack).
Steganography, however, has also been used to help people operating in repressive regimes to more safely transport sensitive information; to protect journalists and their sources; to safeguard against industrial espionage when crossing borders; and for intelligence agencies undertaking deep-cover operations.
Speaking earlier this month at Black Hat Europe in London, Dominic Schaub, a researcher at a Canadian firm called Discrete Integration, noted that many types of digital steganography may be revealed if investigators look at a PC on which such tools are installed and find encryption tools.
Regardless of intentions, it looks like steganography is going to get more difficult to spot in the future. That's thanks to Schaub building a new approach to digital steganography, in the form of a "fast, stable and functional" toolset that he says functions as "a self-concealing, perfectly deniable encryption/steganography suite."
 Dominic Schaub's brief history of steganography. (Source: Perfectly Deniable Steganographic Disk Encryption)
Dominic Schaub's brief history of steganography. (Source: Perfectly Deniable Steganographic Disk Encryption)Russian Doll Steganography
The suite of tools he built creates a hidden, encrypted partition on a disk, while leaving no digital forensic traces, thus making so-called Russian doll steganography - hiding something inside something that looks whole - much easier.
"Deniable encryption and steganography nominally safeguard sensitive information against forced password disclosure by concealing its very existence," Schaub says in an overview of his research. "However, while the presence of sensitive information may be 'plausibly' denied, the possession of steganographic software - e.g. suspiciously configured VeraCrypt - is readily detected and regarded as a 'smoking gun' that invalidates such deniability."
VeraCrypt, for example, includes the ability to create hidden volumes with their own operating system.
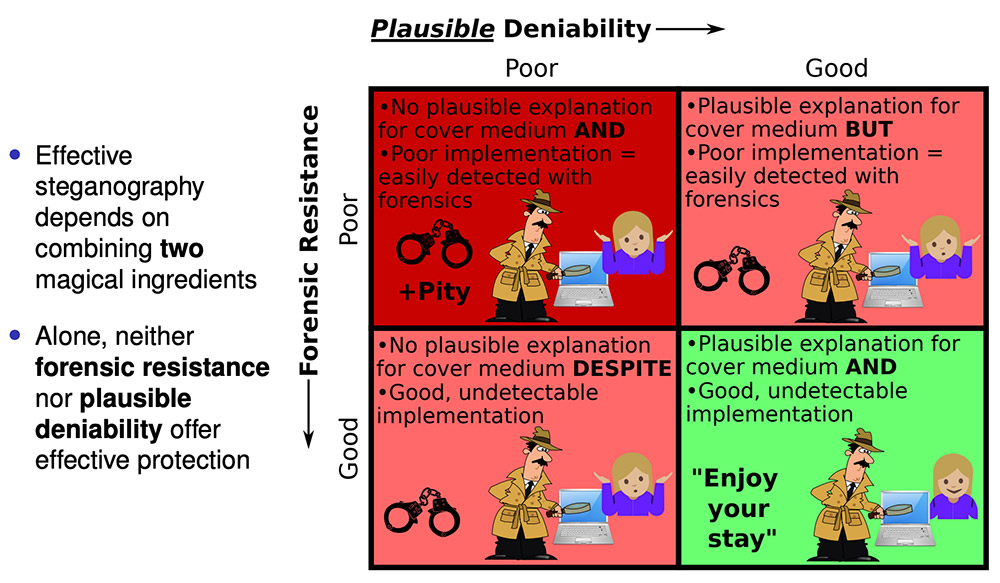 Effective steganography requires plausible deniability and forensic resistance, says Dominic Schaub. (Source: Perfectly Deniable Steganographic Disk Encryption)
Effective steganography requires plausible deniability and forensic resistance, says Dominic Schaub. (Source: Perfectly Deniable Steganographic Disk Encryption)But Schaub says there's a way to address that shortcoming, via what he calls self-concealing steganography, as The Daily Swig first reported.
"In this new paradigm, steganographic tools hide themselves in a self-recursive manner that renders them forensically invisible," he says. "Moreover, upon cryptographic activation by an authorized user, these hidden tools can bootstrap themselves into existence without generating any incriminating forensic evidence. Provided that requisite cryptographic conditions are met, such steganography can be considered 'perfectly deniable.'"
A bootstrap is the program that initializes an operating system during its startup.
'Bit-for-Bit' Normal Linux
Schaub says that his approach enables the creation of a decoy system that "appears bit-for-bit as a normal Linux system" that has been created using entirely out-of-the-box, default Ubuntu parameters.
Schaub says his tool spans about 30,000 lines of code, including a "main kernel module, userspace utilities - for installation, diagnostics, etc. - and various components of [the] bootstrap system."
Although the tool remains in development, he's also tested that it works well on various combinations of Arch and Ubuntu, and has confirmed that VirtualBox for Windows - a free, open source hypervisor - "works very well" on the hidden system.
Numerous Applications
The rise of digital steganographic tools that are tougher to spot is good news for people operating in repressive regimes, or others attempting to safeguard themselves against bad actors.
But of course, tools built for good often get repurposed for illicit purposes, and digital steganography looks set to make life more difficult for law enforcement agencies.
"Perfectly deniable steganographic disk encryption is going to be a nightmare when it comes to gathering digital evidence," says Alan Woodward, a professor of computer science at the University of Surrey, via Twitter.

