Critical Infrastructure Security , Cyberwarfare / Nation-state attacks , Fraud Management & Cybercrime
Argentina and Others Suffer Power Outages; System Maintenance Disrupts Target(euroinfosec) • June 17, 2019 A Target store in Richmond, Texas (Photo: Target)
A Target store in Richmond, Texas (Photo: Target)Not all that crashes has been hacked. To wit, this past weekend there were multiple major outages. But none were due to cyberattacks.
See Also: 10 Incredible Ways You Can Be Hacked Through Email & How To Stop The Bad Guys
On Sunday at 7 a.m. local time, a massive power outage hit Argentina, leaving much of the country in the dark and disrupting train, traffic lights and water supplies, local media reported. Some other countries - including Uruguay, Paraguay and some cities in Chile - were also affected.
Also this past weekend, U.S. retailer Target suffered separate outages that left customers unable to pay for anything.
Dark in Argentina
The power outages in Argentina occurred just prior to local elections being held in many parts of the country. Suspicious, right? But not as suspicious as what experts say is the country's aging power infrastructure.
Indeed, Argentina's Clarín newspaper reports that the Argentinian government has blamed the "gigantic" outage on the country's electric power interconnection systems collapsing due to coastal storms. Officials also noted that the rolling blackouts had taken out not just Argentina, but large parts of Uruguay. Apparently, that's also what took out parts of Paraguay and Chile.
For the record, local elections in Argentina went ahead - even if the lights weren't on - and electricity was restored to many parts of the country by late afternoon.
Target Back Online After Outage
Also this past weekend, Target suffered twin outages, neither of which trace to a hack attack. On Saturday, customers were unable to buy any goods in stores or online as a result of an outage caused by what Target blamed on "an internal technology issue" that lasted about two hours.
"Our technology team worked quickly to identify and fix the issue, and we apologize for the inconvenience and frustration this caused for our guests," a Target spokesman said. "After an initial but thorough review, we can confirm that this was not a data breach or security-related issue, and no guest information was compromised at any time."
In a separate incident on Sunday, customers couldn't use their payment cards in some stores for a couple of hours. Target blamed that failure on the outage of a data center run by NCR, which Target uses to process payments.
NCR didn't immediately respond to a request for comment.
"We can confirm that this was not a security-related issue and no payment information was compromised," a Target spokeswoman told the Wall Street Journal.
Don't Bet on Hacking
What the Target and power outage episodes have in common is that none appear to have been caused by hackers.
But as with any outage, it appears that some commentators didn't hesitate to suggest that for the power grid outage at least, hackers might have been at work.
"There are some very irresponsible people with very large audiences claiming the electric grid outages in South America are a cyberattack with zero expertise or insight into the subject or case," said industrial control system expert Robert M. Lee, CEO of Dragos, via Twitter. "Please ignore these people as always."
As the security expert known as The Grugq tweeted, squirrels remain a much more likely explanation for any power outage than hackers.
Indeed, statistically speaking, not just squirrels, but also birds, snakes and even monkeys - not to mention human error - are much more likely causes of outages than any type of cyberattack (see: US Navy Collisions: Don't Bet on Hacking).
Power Grids: Good News
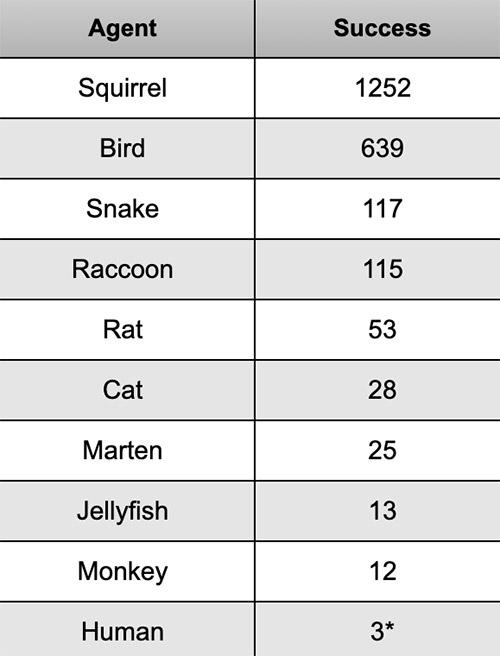 Cause of known disruptions as of Jan. 21 (Source: Cyber Squirrel 1)
Cause of known disruptions as of Jan. 21 (Source: Cyber Squirrel 1)
The good news about power grids, security experts have long told me, is that they're so heterogeneous - and often filled with equipment of drastically different ages - that crashing a country's entire electric grid would likely be incredibly difficult (see: How Triton Malware Targets Industrial Control Systems).
There's no one piece of malware that could accomplish the task. Instead, malware would have to be customized for each unique environment, and likely built using a physical recreation of every different target environment.
Given the myriad power providers across any given geographic region, knocking any country off the grid, using malware, likely remains a very difficult task (see: Xenotime Group Sets Sights on Electrical Power Plants).
Now for the Bad News
But what has reportedly lately been hacked - as in infiltrated, but not crashed - are power networks in Russia, by U.S. Cyber Command, which is the arm of the Pentagon that handles online offensive and defensive hacking operations, The New York Times reported on Saturday.
Following President Donald Trump issuing the still-classified National Security Presidential Memoranda 13 last summer, U.S. Cyber Command has been placing "implants" - pieces of software that can be used to eavesdrop or crash equipment - across the systems that run Russia's power grid, among other targets, the Times reports. While such surveillance has been underway since 2012, it reports, the recent moves represent an escalation in U.S. tactics.
Gen. Paul M. Nakasone, who heads U.S. Cyber Command, last August used his agency's expanded powers to authorize a hacking campaign that crashed the computer systems at Russia's Internet Research Agency, as one of four offensive campaigns timed around the midterm elections, the Times reported. Public details about any of those efforts, however, remain scant (see: Before Elections, US Cut Russian Trolls' Internet Access).
 Lt. Gen. Paul Nakasone appeared on March 1, 2018, before the Senate Armed Forces Committee, as part of his successful nomination by President Trump to serve as the director of the National Security Agency as well as U.S. Cyber Command. (Source: C-SPAN)
Lt. Gen. Paul Nakasone appeared on March 1, 2018, before the Senate Armed Forces Committee, as part of his successful nomination by President Trump to serve as the director of the National Security Agency as well as U.S. Cyber Command. (Source: C-SPAN)The latest moves are reportedly meant to serve as a warning to Russia over its hacking efforts, including its attempts to influence elections as well as conduct offensive espionage operations, such as attempting to steal nuclear power research from Westinghouse Electric Corp. in Pennsylvania (see: Dutch and British Governments Slam Russia for Cyberattacks).
Last July, meanwhile, the U.S. Department of Homeland Security warned that a Russian attack group known as Energetic Bear or Dragonfly, aka APT28, had amassed "hundreds of victims" as part of an ongoing campaign to infiltrate U.S. power companies, The Wall Street Journal reported.

