Cybercrime , Cyberwarfare / Nation-state attacks , Data Loss
Monica Witt Allegedly Aided Spear-Phishing Attacks Against US Military(jeremy_kirk) • February 14, 2019 Source: FBI
Source: FBIA former U.S. Air Force counterintelligence agent has been indicted together with four Iranians for coordinating spear-phishing campaigns that sought to compromise the computers of other U.S. intelligence agents. The charges were revealed by the U.S. Department of Justice on Wednesday.
The former agent, Monica Elfriede Witt, defected to Iran in 2013, the DOJ says. She also stands accused of revealing the identity of a highly classified U.S intelligence program and an intelligence officer. Witt has been charged in federal court in Washington with three counts of espionage.
Witt's indictment marks another serious security breach by an insider. The U.S. government over the past several years has struggled to contain leaks of classified information.
Iran has a well-developed offensive cyber capability. Private security companies have developed profiles for groups suspected to be connected with Iran and linked them to campaigns that have sought to compromise Western companies and organizations.
In January, the Department of Homeland Security warned of attacks that sought to modify Domain Name System settings and issued an emergency directive warning agencies to check for tampering. The computer security firm FireEye has seen similar attacks, which it said appeared to have an Iranian nexus (see: DHS Issues More Urgent Warning on DNS Hijacking).
Also last month, U.S. Director of National Intelligence Dan Coats warned that Iran, Russia, China and North Korea remained a looming threat to the U.S. government and private companies (see: Intelligence Chiefs Expect More Cyberattacks Against US).
Target Packages
The Justice Department says it took years of investigation to build its case against the 39-year-old Witt. She served in the U.S. Air Force from August 1997 though March 2008 and had clearance for secret and top secret material, including the identity of clandestine agents.
Her path to Iran started after she attended an anti-American conference there in 2012. It was run by the New Horizon Organization, which prosecutors say is connected to the Iranian Revolutionary Guard Corps. That unit is responsible for unconventional warfare, including assassinations and cyberattacks, according to the indictment.
Witt is accused of developing target packages, or background data that would help attackers track people. That could include their location, position and possible vulnerabilities that could be taken advantage of, according to the indictment.
Witt speaks Persian Farsi as the result of her military training, and she also deployed to the Middle East. In early 2012, she appeared in videos broadcast on Iranian media where she criticized the U.S. She also converted to Islam in a ceremony that appeared on Iranian TV.
She apparently returned to the U.S. in mid-2012, where FBI agents warned her that she was a target for recruitment by Iranian agents. Witt allegedly told agents that she wouldn't speak of her Air Force work if she returned to Iran.
Another Edward Snowden?
But Witt allegedly indicated her disenfranchisement with the U.S. during communications with an Iranian-American identified in the indictment as "Individual A."
Prosecutors say that in June 2013, she wrote to that individual, saying "if all else fails, I just may go public with a program and do like Snowden :)" and indicated she possibly might contact WikiLeaks. Edward Snowden was a former National Security Agency contractor who leaked thousands of sensitive documents in 2013 documenting U.S. and British cyber capabilities.
In August 2013, Witt defected to Iran. The Iranian government provided her with housing and computer equipment, prosecutors allege. Witt began conducting searches for U.S. agents on Facebook via fictitious accounts to create the target packages.
DOJ alleges the targeting information was then used by the four Iranian nationals who were also indicted: Mojtaba Masoumpour, Behzad Mesri, Hossein Parvar and Mohamad Paryar. The men have been charged with three counts of computer crime, including hacking.
 The four indicted Iranian men (Source: FBI)
The four indicted Iranian men (Source: FBI)Mersi is accused of targeting U.S. agents via a company he ran, as well as contracting with the three other men for technical support for malware.
The attacks often first involved sending friend requests to U.S. agents on Facebook, then sending messages or email with malicious attachments, according to DOJ. Some agents accepted because the accounts appropriated the identities of other agents. Other accounts were fake, including one going by the name "Bella Wood."
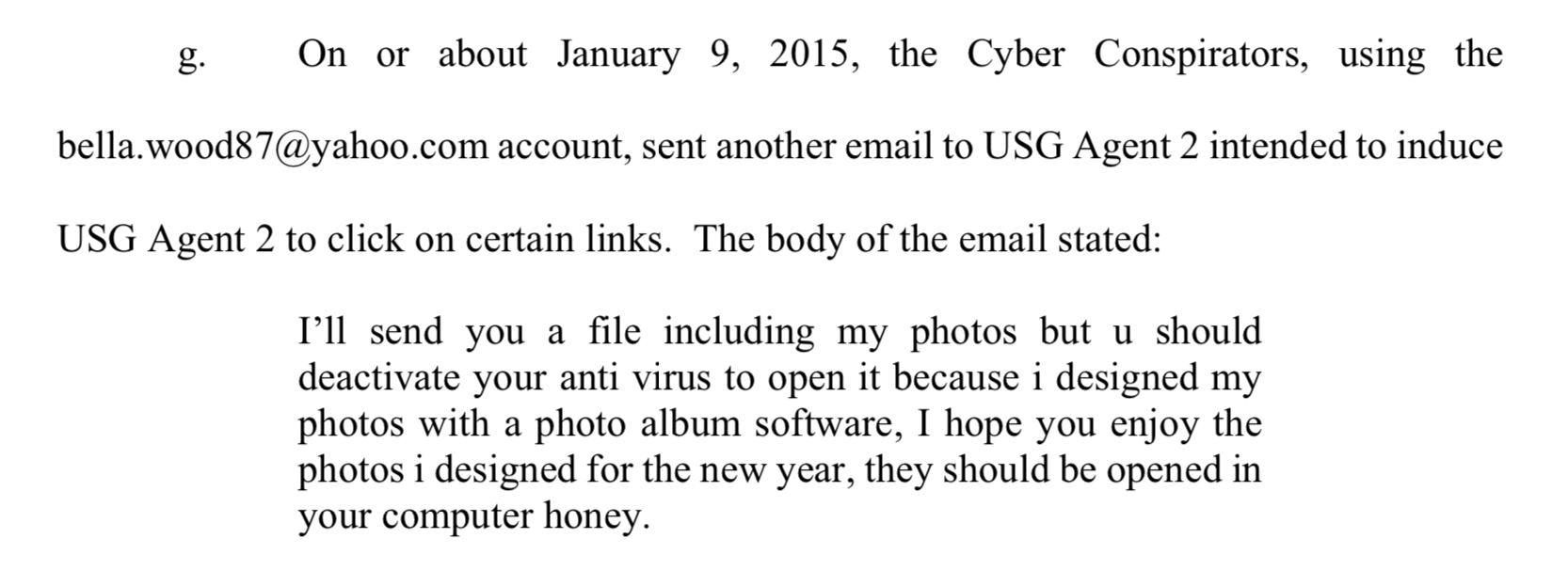 An excerpt from an email sent by "Bella Wood" to a U.S. government agent
An excerpt from an email sent by "Bella Wood" to a U.S. government agentIt's unclear if any of the attempts were successful, but at least one of the messages sent by the group would have immediately raised suspicion. It asked the recipient to disable anti-virus software before opening what was purportedly a photo album.


