 Image copyright
US Court of Appeals
Image caption
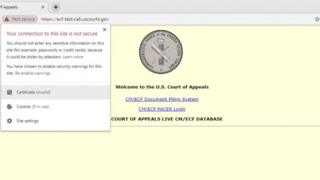
Some government websites are telling users not to enter sensitive information
Image copyright
US Court of Appeals
Image caption
Some government websites are telling users not to enter sensitive information
The US government shutdown is making many official websites harder to access and potentially leaving users more vulnerable, tech experts are warning.
Affected websites include the US Department of Justice, the Court of Appeals and Nasa.
The shutdown, over a funding row for President Trump's wall, has left thousands of federal workers unpaid.
One of the side effects of this situation is that security certificates for websites are not being renewed.
Digital certificates ensure that communications between devices and websites are sent in an encrypted, secure manner and are an essential part of keeping IT infrastructure up and running. But, when issued, they are given an expiration date of anything between a few months and several years.
So why has the US government shut down? When out-of-date code causes chaosAccording to internet services website Netcraft, more than 80 security certificates used by .gov websites have expired.
This includes the US Department of Justice, which is using a certificate that expired in the week leading up to the shutdown and has not been renewed since.
The Department of Homeland Security's newly-created cyber-security and infrastructure security agency, is currently operating with less than half its staff, according to Suzanne Spaulding, a former under-secretary at the agency.
She said: "With each passing day, the impact of the government shutdown on our nation's security grows. Meanwhile, our adversaries are not missing a beat and the daily attacks on our systems continue.
"Cyber-security is hard enough with a full team. Operating at less than half strength means we are losing ground against our adversaries."
Security consultant Paul Mutton, writing in a blog for Netcraft, added: "With Donald Trump seemingly unwilling to compromise on his demands for a wall along the border with Mexico, and Democrats refusing to approve a budget containing $5.7bn (£4.46bn) for the wall, the hundreds of thousands of unpaid federal employees might not be the only ones hurting.
"As more and more certificates used by government websites inevitably expire over the following days, weeks - or maybe even months - there could be some realistic opportunities to undermine the security of all US citizens."
Netcraft suggests that the generic nature of some certificate error messages might make it easier for attackers to exploit users trying to access the sites with expired certificates.
Other cyber-security experts agreed that there was a limited risk to the public.
"An out-of-date certificate still provides for strong encryption, however it becomes harder for the user to verify the legitimacy of the web site and their connection to it," explained Ken Munro from Pen Test Partners.
And if users began ignoring alerts warning them the government sites appeared to be insecure, scammers might take advantage of this to lure victims to rogue pages, added Prof Alan Woodward.
"You could, for example, be subjected to a Man-in-the-Middle attack as a result," explained the University of Surrey professor.
"If you click past the warning you would be doing so at your own risk, and I don't think anyone would recommend it."

