Authentication , Endpoint Security , Fraud Management & Cybercrime
Politicians' All-Star Password Picks: '123' and 'ILoveYou'(euroinfosec) • January 11, 2019 Source: SplashData's "Worst Passwords of 2018"
Source: SplashData's "Worst Passwords of 2018"Never ascribe to advanced hackers that which can be adequately explained by the anger of a young man who turns poor password choices to his advantage.
See Also: Live Webinar | Sunset of Windows Server 2008: Migrate with Docker
That's one obvious takeaway from the "hackerangriff" - hacker attack - that resulted in the leak of personal contact details and other information for 1,000 German politicians, celebrities and journalists (see: German Police Identify Suspect Behind Massive Data Leak).
The dox - data leak - included private mobile phone numbers for some of the country's top political figures, as well as copies of sensitive chat messages and photographs of children, among other sensitive material.
The culprit appears to be what so many information security experts predicted: Not an "advanced persistent threat" - APT - hacker crew working from Russia or another nation-state, but rather the functional equivalent of an "advanced persistent teenager."
Indeed, police say that a 20-year-old man that they arrested on Sunday confessed to the crimes on Monday. Due to the suspect's age, he's set to be tried in juvenile court, where he faces a maximum three-year prison sentence (see: Germany's Mega-Leak Takeaway: Noisy Young Hacker Got Caught).
Give credit to German police for quickly identifying a suspect, as well as declining to guess about who might have been involved before they did so. That's a far cry from the anonymous government sources who in other countries remain so ready to ascribe every new bank hack to Russia and every mass data theft to China (see: Reports: China Suspected in Marriott Database Breach).
"There are enough security challenges in our industry without incidents being overhyped in order to gain media attention or sales leads," Brian Honan, who heads Dublin-based cybersecurity consultancy BH Consulting, tells me.
Breached: Email, Cloud, Social Media
Germany's interior ministry last week said that the attacker likely acquired the data by breaching victims' email and social media accounts and cloud services, says Thomas Rid, a professor of strategic studies at Johns Hopkins University, via Twitter.
An unnamed investigator told German weekly news magazine Der Spiegel that the suspect apparently didn't understand the impact that his actions might have.
If so, the 20-year-old student is hardly the first would-be hacker to seemingly not comprehend the potential impact of his crimes (see: Satori Botnet's Alleged Developer Rearrested).
Reminder: Pick Strong Passwords
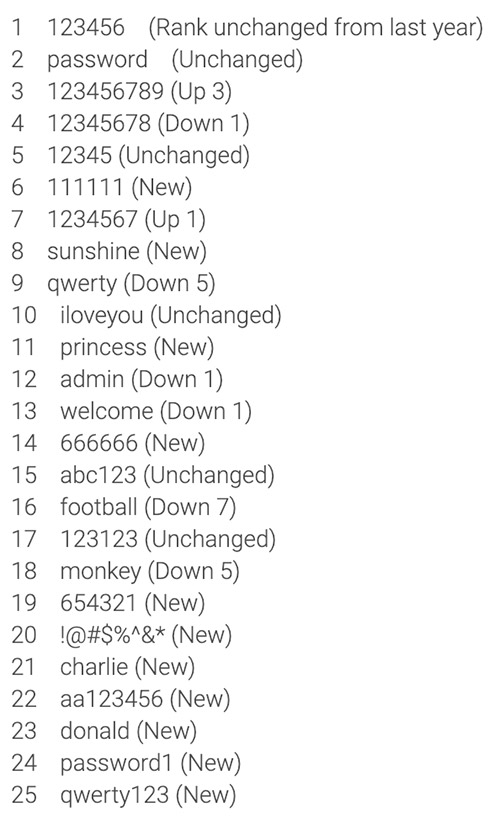 SplashData's "worst passwords of 2018," based on its review of 5 million passwords that leaked on the internet last year, compared to their prevalence in 2017 data dumps
SplashData's "worst passwords of 2018," based on its review of 5 million passwords that leaked on the internet last year, compared to their prevalence in 2017 data dumpsThis incident should remind everyone - public figure or not - that if they don't take cybersecurity seriously, they may pay a data security cost, potentially at the hands of an angry 20-year-old.
"Bad passwords were one of the reasons he had it so easy," Minister of the Interior Horst Seehofer told reporters on Tuesday, the Guardian reported. "I was shocked at how simple most passwords were: 'ILoveYou', '1,2,3.' A whole array of really simple things."
In an ideal world, people wouldn't have to rely on passwords anymore to secure their information. But this is 2019, and that's not the world we live in (see: Why Are We *Still* So Stupid About Passwords?).
"Victim blaming is pointless; human behavior should be central to security design, and as humans we all do the same things that can be exploited by hackers," says Alan Woodward, a professor of computer science at the University of Surrey. "Our worst sin is that we are all slightly lazy with regard to security because we think it will never happen to us."
Industry Failure
Honan, who founded Ireland's first computer emergency response team and advises the EU's law enforcement intelligence agency Europol, says he's not surprised that many of the German victims appeared to have picked poor passwords.
"Many people do not see their email or social media accounts as high-value assets, and as a result may practice poor security hygiene," he tells me. "We as an industry have failed to provide users with the user experience and tools to make and maintain their online personas in a secure manner. As an industry we need to provide more secure means, both technical and educational, for people to secure their accounts and systems."
Secure More, Remember Less
Woodward says one essential resource for anyone who uses a password or who programs systems that require them is the "spot on" password guidance issued by the National Cyber Security Center, the public-facing component of U.K. intelligence agency GCHQ (see: Successful Security? Stop Blaming Users).
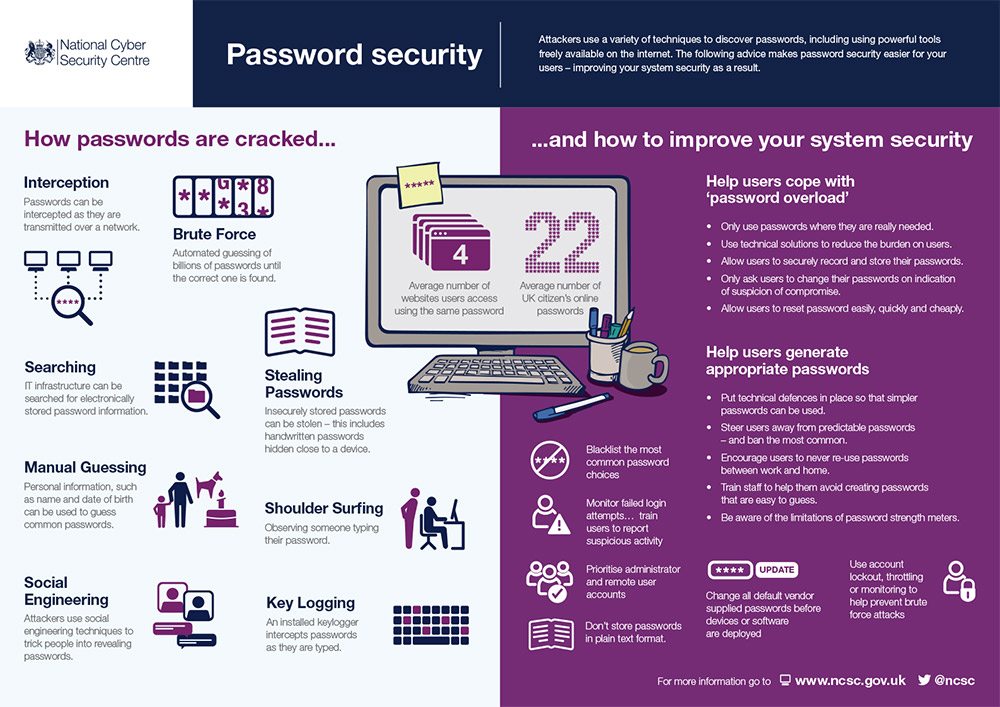 Source: NCSC
Source: NCSCOne thing anyone who wants to avoid becoming a victim of these types of attacks should do is ensure they always use a unique, relatively complex password for every online service. Once picked, it need never be changed, unless the site or service gets breached.
"I also personally recommend using a password manager - it means you can have truly strong passwords that you'll never remember, which are always the best passwords," Woodward tells me.
"Yes, password managers can be a single point of failure, but choose a really strong password for that and you have to remember only the one," he adds. "And yes if the provider were breached we'd all be in the poo; but you have to do due diligence and pick one you trust."

