Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
RiskIQ Says Attackers Apparently Are Manipulating Gift Cards(@Ferguson_Writes) • June 27, 2019
The cyberattack earlier this year against Indian outsourcer Wipro, as well as several of its customers, is part of a much larger, multiyear phishing campaign that involves many more companies used as jumping off points, according to an analysis by the security firm RiskIQ.
See Also: Webinar | The Future of Adaptive Authentication in Financial Services
The ultimate goal of the unknown group behind the campaign is not fully understood, but it appears that financial gain, especially through the manipulation of gift cards, is at least a major motivating factor, RiskIQ found.
The attackers' phishing campaign, RiskIQ says, is designed to target retailers, employee rewards programs and other organizations dealing in gift cards. Once they had access, the attackers used money transfer services, clearinghouses and other payment processing services to monetize the data they stole, according to the analysis.
"The actor group's phishing campaign looks to target company employees for the purpose of harvesting user credentials so that the actors can gain direct access to the organizations' infrastructure," Yonathan Klijnsma, head researcher at RiskIQ, tells Information Security Media Group.
"The common targeting profile across all organizations seems to align with specific targeting of gift cards. One hypothesis for this targeting approach is that the actor group is looking to gain access to money outside of traditional financial services," Klijnsma adds.
The group - tentatively named "Cardshark" - behind the campaign prefers to use commercially available open source software as part of its attack and as a way to cover its tracks, RiskIQ researchers determined. The group also uses PowerShell scripts to steal credentials and certificates, according to RiskIQ, which has conducted previous analyses of various skimmer attacks (see: New Skimmer Attack Steals Data From Over 100 E-Commerce Sites).
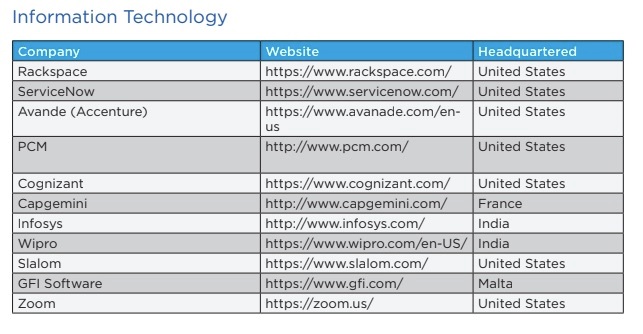 List of IT firms targeted in phishing campaign (Image: RiskIQ)
List of IT firms targeted in phishing campaign (Image: RiskIQ)In addition to Wipro, the attack group targeted Rackspace, possibly in an attempt to use that company's platform and other services to access its customers and third parties, RiskIQ says. Others that appear to have been victimized during this three-year campaign include retailers, such as Best Buy and Staples; employee rewards programs, such as Affinion Group and O.C. Tanner; gift card providers Greendot and BlackHawk Networks; and digital marketing firms SmartFocus and Insideview, among many others, according to RiskIQ.
Multiyear, Multipart Phishing Campaigns
The RiskIQ analysis found that the threat group appears to have started targeting victims in May 2016. During a three-year period, there were at least five separate campaigns that targeted companies in various sectors, including retail; gift card programs; point-of-sale and money transfer services; payment services; loyalty rewards programs; and IT vendors, researchers determined.
These attacks culminated in April, when Wipro, India's third-largest IT outsourcing company, acknowledged that it was investigating a multimonth intrusion and that its systems were being used as jumping-off points for digital phishing expeditions targeting the systems of a least a dozen of its customers.
Blogger Brian Krebs first reported on the Wipro case and brought the issue to the attention of RiskIQ as well as FireEye, which has conducted its own analysis of the attack.
RiskIQ's Klijnsma says that while the targets of the campaign don't seem connected, all touched on the gift card industry in some way, such as supplying the data or the infrastructure to support the financial services used by this particular market.
"Information technology companies were a bit of an outlier in the common gift card connection among all other organizations, but our hypothesis is that since the actor group was mainly targeting North American organization in the early stages of its attacks, Rackspace could be an infrastructure provider for other targets of interest," Klijnsma says. "Additionally, the Krebs reporting notes that once the actor group breached Wipro, they actively targeted Wipro customers associated with gift card infrastructure."
Tools of the Trade
As part of the attack, it appears that the group used legitimate email marketing and analytics tools to help disguise their scheme, according to the RiskIQ report.
At one point, it appears the attackers used some templates and artwork developed by the Swiss penetration testing firm Lucy Security, which markets a platform for organizations to conduct security and phishing-awareness training. In addition, Klijnsma notes that the attackers also appear to have compromised default Lucy SSL certificates as early as May 2016.
While RiskIQ notes that the attackers did not compromise Lucy Security's core software or platform, some of the assertions in the analysis were refuted by the company.
"Lucy Security has previously reported that hackers have copied some artwork from the Lucy phishing simulation software and used the designs as part of their phishing attacks. The hackers did not use the Lucy security platform to deliver these attacks," Lucy Security CEO Colin Bastable says. "Our technology generates unique and traceable links in order to track user susceptibility and awareness training participation. It is a security awareness training platform."
Some of the other legitimate tools that the RiskIQ analysis determined were used during this campaign included ScreenConnect, which can give an attacker remote control access of a computer, and EMOC Remote Installer, which allows for the deployment of any tool across a network.
Through a combination of stolen templates and legitimate tools, the group was able to craft its phishing emails that could avoid detection and security protections within the network and then get unsuspecting employees to click, according to RiskIQ. In most cases, these campaigns lasted only a few days to draw attention away from the attack, the analysis found.
BabyShark and North Korea
While the RiskIQ analysis could not pinpoint a specific sponsor of this group, the report noted one possible tie to techniques previously used by North Korea.
Researchers found that the group used a PowerShell script called BabySharkPro, which had previously been associated with threat actors tied to North Korean threat activity. The RiskIQ analysis, however, concedes this could be a "false flag" to mislead those investigating this particular campaign.
"The only 'connection' to North Korea is the reference to 'Baby Shark,' Klijnsma says. "However, this doesn't mean the Cardshark group is part of a North Korean operation. Baby Shark could even be a false flag to throw off researchers. However, we do note that the size, sophistication and focus of this campaign do rival that of known state-sponsored groups."
Using the BabySharkPro script, the attackers could deploy the credential-stealing tool Mimikatz, which could then gather more data from a victim's computer and allow the group to burrow deeper into the network, RiskIQ found.

