Cybersecurity , Device Identification , Endpoint Security
Trend Micro Says It Moved Cranes Using RF Software Flaws(jeremy_kirk) • January 16, 2019 Cranes in Norfolk Harbor in Virginia (Joanna Poe via Flickr/CC)
Cranes in Norfolk Harbor in Virginia (Joanna Poe via Flickr/CC)Radio-frequency controllers used in the construction, mining and shipping industries are dangerously vulnerable to hackers, making the devices prime targets for attacks that could shut down operations and possibly hurt workers, Trend Micro says in new report.
See Also: Key Drivers to Enable Digital Transformation in Financial Services
RF controllers, which are critical for safety, often use proprietary communication protocols that haven't kept pace with security threats. An attacker could spend less than $2,000 to build a battery-powered, coin-sized device that can take over an industrial device, Trend Micro claims.
The results from such an attack could be unavailable equipment, financial losses, and at worst, human injuries. The affected vendors include Saga, Juuko, Gain Electronic Co. Ltd., Telecrane, and Hetronic, Trend Micro reports.
"Unfortunately, we found a complete lack of security in the design of these devices, leaving millions of vulnerable units installed on heavy industrial machinery open to local and remote attacks unless patched promptly," the information security company says in an 82-page technical report released Tuesday and in an accompanying blog.
 Images of several handheld and belt-pack remote controllers manufactured between 1997 and last year (Source: Trend Micro)
Images of several handheld and belt-pack remote controllers manufactured between 1997 and last year (Source: Trend Micro)Trend Micro says it has notified the affected vendors and that some have already deployed patches or plan to upgrade their security defenses.
During on-site tests, Trend Micro researchers say they were able to quickly use software vulnerabilities "to move full-sized cranes deployed in production at construction sites, factories and transportation businesses."
Ironically, Trend Micro claims that commercial garage door openers are more secure than millions of RF controllers deployed for industrial purposes.
Garage remotes, for example, employ rolling code, which prevents would-be attackers from being able to replay the identical packets at a later time to open the garage door. Without rolling code, an attacker could record commands that start or stop a piece of equipment, then play back the command at another time.
Local And Remote Attacks
The researchers analyzed RF controllers manufactured by seven vendors. None of those vendors implemented "proper security measures, making attacks possible both locally and remotely," Trend Micro claims.
By reverse-engineering communication protocols, the researchers identified five classes of attacks, four of which it estimates could be carried out for $2,000 or less, as seen below.
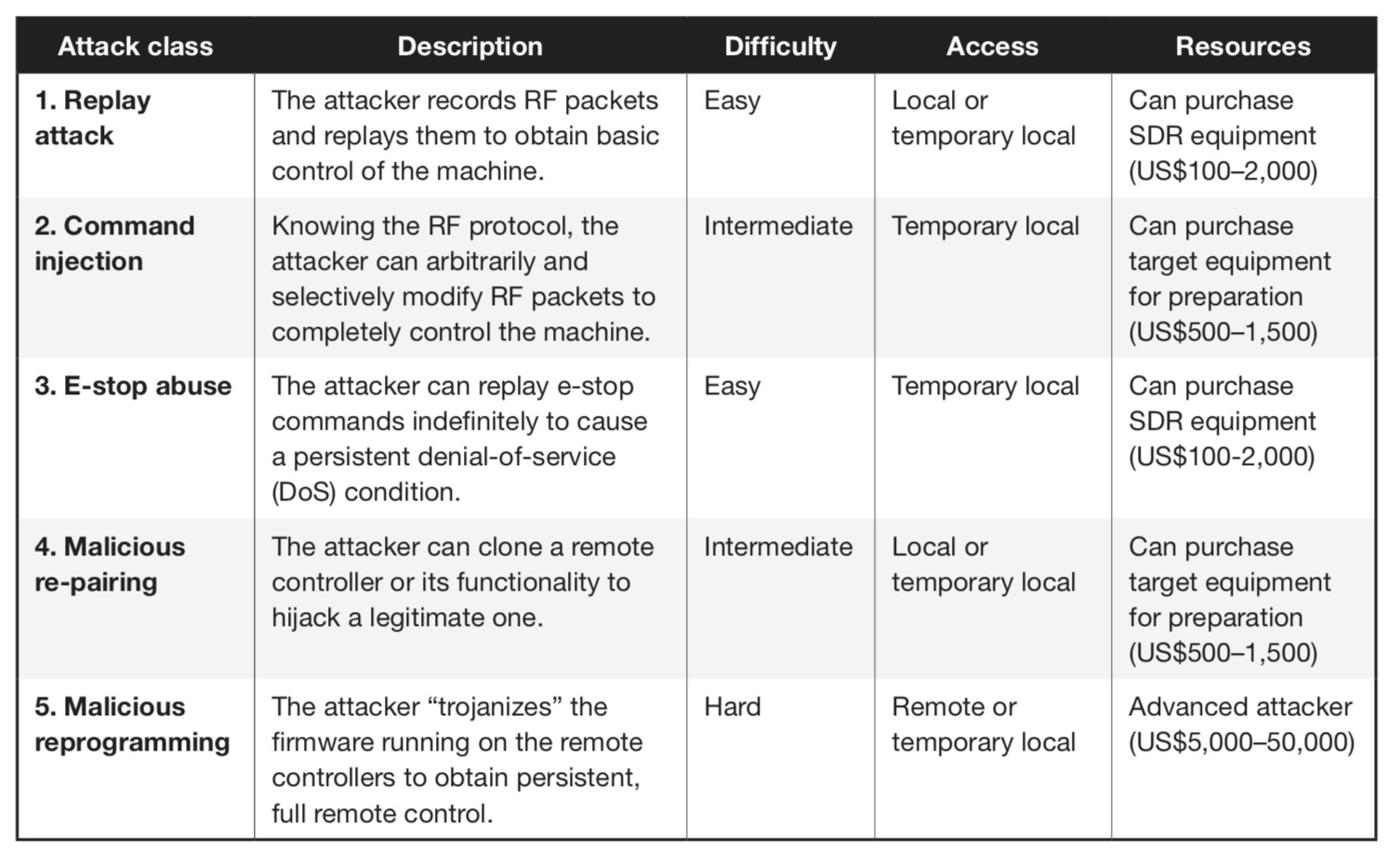 Source: Trend Micro
Source: Trend MicroMany vendors, by default, rely on security-by-obscurity, but that's a risky strategy that relies on attackers not spending too much time mapping the system, Trend Micro says. So far, there is scant public documentation on exactly how many RF controllers work, aside from some leaked schematics and some user manuals. As a result, there hasn't been much publicly released research into RF controller security.
Attackers who can't successfully reverse-engineer an RF protocol, however, may still be able to launch a replay attack, which might give them basic control over a device. Another low-cost attack is simply to stop a device by sending a repeating command - essentially executing a denial-of-service attack.
"We simply consider that, to carry out our attacks, a budget of a few hundred U.S. dollars is sufficient for the replay and e-stop abuse attacks, whereas the other attacks might require the attacker to obtain a copy of the target device, whose price ranges from a hundred to a few thousand U.S. dollars," the researchers say.
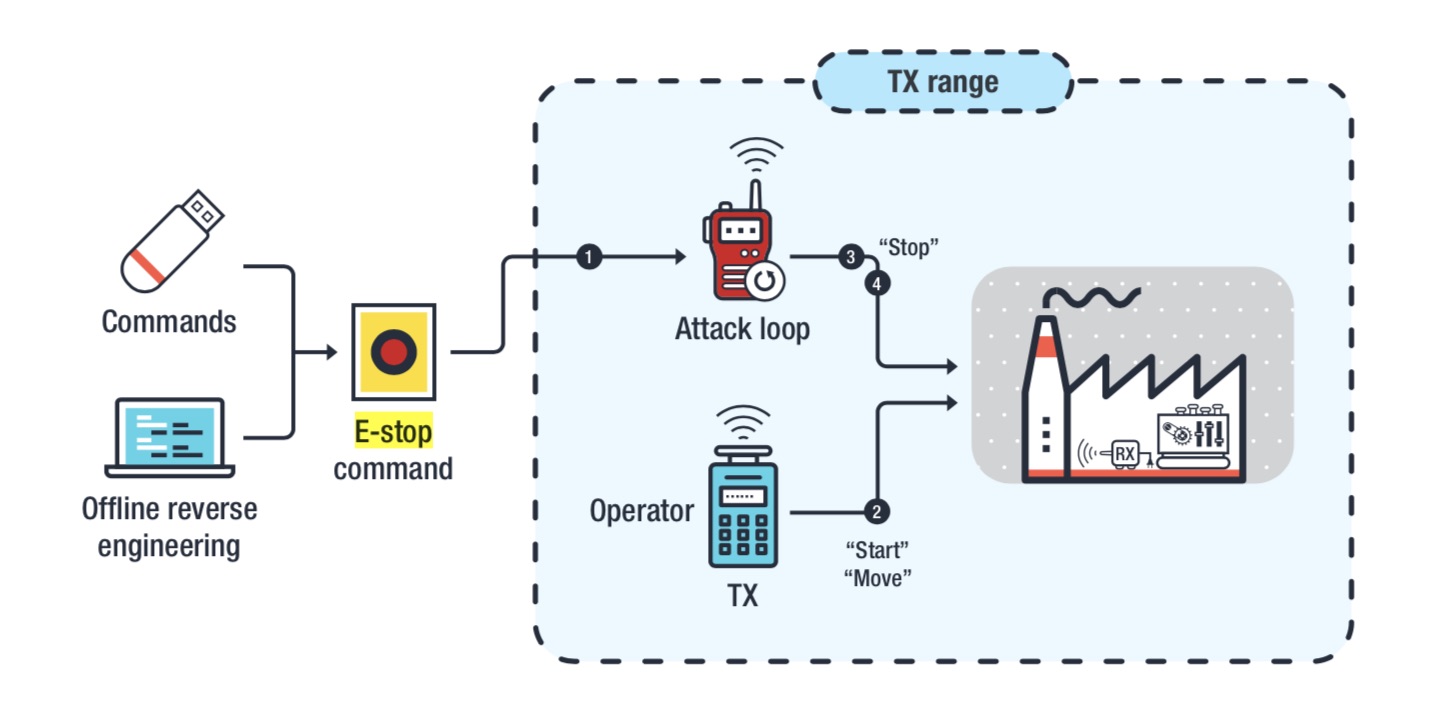 A conceptual diagram of an e-stop attack (Source: Trend Micro)
A conceptual diagram of an e-stop attack (Source: Trend Micro)The cost to mount attacks has recently declined thanks to platforms such as Arduino, which Trend Micro says allows for the construction of modular hardware tools with the same flexibility as a software-defined radio. In fact, the researchers used it to build their own custom, lightweight hacking device, which they call RFQuack; it can sniff and send RF packets.
"From a research perspective, this is a step forward in terms of tools," Trend Micro says. "From a risk perspective, this lowers the barrier for an attacker."
Ditch Proprietary Protocols
One of the bigger-picture problems with insecure RF controllers mirrors the internet of things device security challenge: Many get deployed and might remain in use for a long time, due to the high cost of replacing a device or simply because such devices are forgotten about until they break, Trend Micro says.
"They're assembled from the vendor, configured - usually by system integrators - according to the clients' requests (e.g., which button does what action), installed at the facilities or equipment and forgotten until they break down," the researchers say.
Patching is often possible, but that remedial action can be stymied by an organization not willing to absorb downtime costs and experience business disruption. Also, the potential for digital attacks in some of these industries hasn't really been considered by users, Trend Micro says.
The researchers recommend that RF vendors to move away from the proprietary protocols on which they have so long relied and instead embrace open standards, such as Bluetooth Low Energy. Some vendors have already started making devices that use the 2.4GHz bands, usually to reduce interference and limit ranges.
Researchers also recommend vendors ensure that their firmware updates remain secure by using over-the-air updates that can accommodate distributed key exchange schemes, which ensures that only digitally signed firmware can be installed. Also, Trend Micro recommends that vendors implement tamper-control mechanisms that would hamper potential attackers reverse-engineering their wares.

