3rd Party Risk Management
,
Breach Preparedness
,
Cybercrime
Trump Administration Warns of Economic Espionage Risk From China, Russia, Iran(
euroinfosec) •
January 8, 2019
The Trump administration has launched a public awareness campaign for the U.S. private sector, urging businesses to better defend themselves against online attackers who may be trying to steal their sensitive data or wage supply chain attacks.
See Also: Live Webinar: Building Secure Delivery Pipelines with Docker, Kubernetes, and Trend Micro
The effort, being run by the National Counterintelligence and Security Center, aims to improve the minimum level of information security practices in place at businesses. At a minimum, NCSC is urging all organizations to review supply chain security, safeguard against spear-phishing emails, beware of social media deception and expect that, when traveling abroad, their equipment will be subject to surveillance or interference.
The NCSC has branded the effort as "Know the Risk, Raise Your Shield," and released a range of videos, posters, brochures and flyers via its website that promulgate strategies to help protect data, assets, technology and networks. The materials were previously distributed to the federal workforce.
"To enhance private sector awareness, we're arming U.S. companies with information they need to better understand and defend against these threats," says NCSC Director William Evanina.

Advice from the NCSC
The U.S. NCSC is a center within the Office of the Director of National Intelligence, not to be confused with the U.K.'s National Cyber Security Centre, which is the public-facing arm of British intelligence agency GCHQ.
The U.S. NCSC's 2018 Foreign Economic Espionage in Cyberspace report, released last July, singles out China, Russia and Iran as posing the biggest nation-state hacking risk to the U.S. private sector. Laws in China and Russia, in particular, allow government agencies to compel firms to assist in their efforts.
But officials warn that the threat is much broader.
"Make no mistake, American companies are squarely in the cross-hairs of well-financed nation-state actors, who are routinely breaching private sector networks, stealing proprietary data and compromising supply chains," Evanina says. "The attacks are persistent, aggressive, and cost our nation jobs, economic advantage, and hundreds of billions of dollars."
Last year, Director of National Intelligence Dan Coats told Congress that in the online realm, Russia poses the top online attack threat to United States, while China, North Korea and Iran are also top threats, "although many countries and some non-state actors are exploring ways to use influence operations, both domestically and abroad."

Robert Hannigan, speaking at the June 2018 Infosecurity Europe conference in London, said cybercrime groups and nation-state attackers are increasingly blurring together. (Photo: Mathew Schwartz)
Indeed, the former head of the U.K.'s signals intelligence agency, GCHQ, last year warned that it was becoming increasingly difficult to tell cybercriminals and nation-state actors apart (see: Cybercrime Groups and Nation-State Attackers Blur Together).
"In some cases, you can see these groups sitting in the same room, and in some cases, you can see where people have been conducting state activity during the day, and then doing crime activity at night," said Robert Hannigan, who headed GCHQ until 2017, speaking at last year's Infosecurity Europe conference in London. "It's an interesting mixture of profit and political intent."
Charges Filed
As part of its effort to warn private businesses to take information security more seriously, NCSC pointed to the numerous charges that have been filed in the past 12 months against alleged nation-state hackers. Individuals named in indictments or sanctions allegedly worked for or on behalf of the governments of:
China: In December 2018, the U.S. Department of Justice charged two Chinese citizens, associated with China's Ministry of State Security, with perpetrating online attacks designed to infiltrate IT managed service providers, which serve large numbers of IT customers. It followed the Justice Department last October charging two Chinese intelligence officers and eight others with economic espionage (see:
2 Chinese Nationals Indicted for Cyber Espionage).
North Korea: In September 2018, the Justice Department charged a North Korean national with having helped perpetrate the WannaCry ransomware outbreak, the Sony Pictures Entertainment breach as well as the theft of $81 million from Bangladesh Bank (see:
Feds Charge North Korean With Devastating Cyberattacks).
Russia: In June 2018, the U.S. government imposed sanctions on multiple Russian individuals and organizations for their alleged "destabilizing cyber activities," including intrusions against the U.S. energy grid and global compromises of routers and switches (see:
US Imposes More Russian Sanctions for Cyberattacks).
Iran: In March 2018, the Justice Department charged nine Iranian nationals with stealing more than 31 terabytes of data from 320 universities in 22 countries - including 144 U.S. institutions - as well as multiple businesses and government agencies (see:
Britain Backs US Hacking Allegations Against Iranians).
Threats to Supply Chain
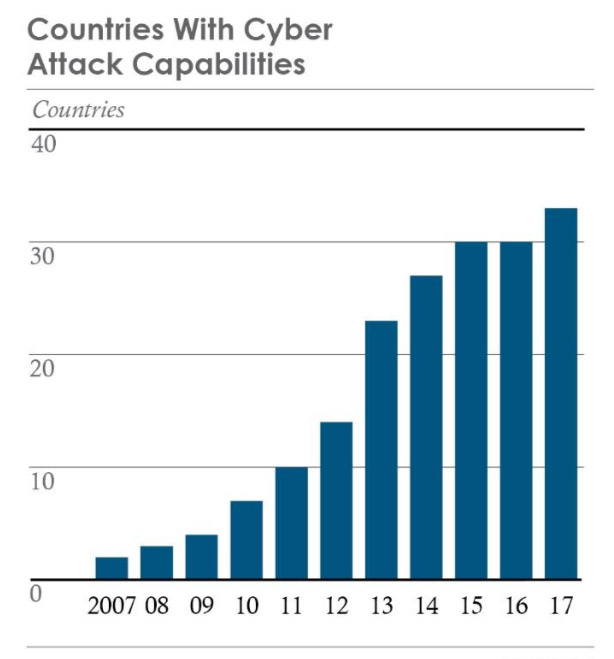
Source: Worldwide Threat Assessment of the U.S. Intelligence Community, released Feb. 13, 2018
Of course, anyone - government-sponsored or otherwise - can potentially launch a hack attack. But the outreach effort by NCSC focuses on some tactics that have been regularly employed by nation-state attackers, including targeting supply chains.
On that front, the NCSC outreach mirrors recent moves by the Trump administration - as well as some governments abroad - to restrict the use of Chinese-built telecommunications gear over fears that it could be easily suborned at the request of Beijing (see: Report: Trump Weighs Executive Order Banning Huawei, ZTE).
NCSC doesn't suggest that securing supply chains will be inexpensive. But it warns that "this is a place where an ounce of prevention is worth a pound of cure."
Prevention includes asking the right questions, conducting due diligence, as well as hiring "acquisition and procurement personnel" to be integral member's of an organization's "enterprise-wide risk management and security program," NCSC says.
Spear-Phishing Success
Spear-phishing attacks are regularly used by every stripe of online attacker; they're the entry point for the majority of hacks perpetrated by remote attackers, security experts say.
Spear-phishing emails have also been employed by APT groups, which the U.S. intelligence establishment said were being run by Russia's intelligence agencies, that targeted multiple U.S. organizations, including hacking the Democratic National Committee and the presidential campaign of Hillary Clinton (see: Nation-State Spear Phishing Attacks Remain Alive and Well).
Such attacks can not only be low cost, but as the attackers' seizure - and then release - of sensitive DNC communications demonstrates, also effective at penetrating targeted environments.
'I'd Like to Add You'
Social media may now be a large part of the U.S. cultural DNA, but NCSC warns that it's also used a tool by foreign intelligence service recruiters.
"China's intelligence services use social media platforms to spot, assess and target Americans with access to business or government secrets," NCSC warns. As an example, the center notes that last year, a Chinese intelligence operative, posing as a job recruiter, first approached a former CIA officer who was ultimately convicted of espionage.
Leave Mobile Devices at Home
The guidance from NCSC also touches on mobile devices and advocates avoiding traveling abroad with smartphones, laptops or other mobile devices, whenever possible. "If possible, leave your electronic device at home," NCSC says. "If you bring it, always keep it with you; the hotel safe isn't really 'safe.'"
It also notes that WiFi access points can be easily monitored by any domestic government agency, and spyware or other malicious software pushed to any system or device that connects to the network. NCSC's advice adds impetus to the need for organizations to issue "burner" devices, especially to executives, with minimum functionality for use when traveling to some foreign countries. Such devices can be completely wiped upon an employee's return.
"When abroad, don't expect electronic privacy," NCSC says.


 Image: Kryptos Logic
Image: Kryptos Logic

 The headquarters of the Bundeskriminalamtes - Germany's Federal Criminal Police Office - in Wiesbaden, Hesse (Photo: BKA)
The headquarters of the Bundeskriminalamtes - Germany's Federal Criminal Police Office - in Wiesbaden, Hesse (Photo: BKA) Centro Hospitalar Barreiro Montijo, which was recently fined in a GDPR enforcement case in Portugal
Centro Hospitalar Barreiro Montijo, which was recently fined in a GDPR enforcement case in Portugal
 Advice from the NCSC
Advice from the NCSC Robert Hannigan, speaking at the June 2018 Infosecurity Europe conference in London, said cybercrime groups and nation-state attackers are increasingly blurring together. (Photo: Mathew Schwartz)
Robert Hannigan, speaking at the June 2018 Infosecurity Europe conference in London, said cybercrime groups and nation-state attackers are increasingly blurring together. (Photo: Mathew Schwartz) Source: Worldwide Threat Assessment of the U.S. Intelligence Community, released Feb. 13, 2018
Source: Worldwide Threat Assessment of the U.S. Intelligence Community, released Feb. 13, 2018