Big Data , Breach Notification , Cybersecurity
7 Scenes: Scottish Cybersecurity Conference Talking Ransomware, Botnets, Banking, Bitcoins and More The Egg at the Craiglockhart campus of Edinburgh Napier University in Scotland (Photo: Mathew Schwartz, ISMG)
The Egg at the Craiglockhart campus of Edinburgh Napier University in Scotland (Photo: Mathew Schwartz, ISMG)Fun cybersecurity fact about Scotland: Many of Britain's banks host their security operations centers in or around Edinburgh.
See Also: Rethinking Endpoint Security
So said Ian Rainsborough of digital forensic software maker Guidance Software, addressing the May 10 "International Conference on Big Data in Cyber Security," hosted by Edinburgh Napier University in Scotland. Throughout the day, a range of experts from academia, industry and the public sector detailed the latest trends in big data, policing, organizing information security teams, ransomware campaigns and more (see Police Reveal Botnet Herders' Disaster Recovery Secrets).
Here are seven visual highlights from the event:
1. Scottish Cybersecurity Networking
The "International Conference on Big Data in Cyber Security" took place at Edinburgh Napier University.
Organized by Bill Buchanan, a professor at the Edinburgh Napier School of Computing, the one-day event included presentations from a number of information security experts, ranging from law enforcement officials and forensic investigators to "big data" practitioners and CISOs, and drew attendees from across the United Kingdom, as well as a smattering from the European mainland. But as with every type of local cybersecurity event, many of the attendees hailed from Scotland, and told me they were there not just to learn, but also to network with peers.
2. Ransomware Hits Hairdresser
 Police Scotland's Eamonn Keane said small businesses in Scotland have been especially hard hit by ransomware attacks.
Police Scotland's Eamonn Keane said small businesses in Scotland have been especially hard hit by ransomware attacks.
Eamonn Keane, a detective inspector with Police Scotland's cybercrime unit, said it's been difficult for police to disrupt the massive rise in ransomware infections. "Every day, there's a new ransomware virus," he said. "I suppose we're going to have to apply a much more proactive engagement from a law enforcement perspective ... like we did with Gameover Zeus, like we did with the international scale of Blackshades and cybercrime as a service" (see How Do We Catch Cybercrime Kingpins?).
3. New Breach Notification Window: 72 Hours
 Hewlett Packard Enterprise's Tim Grieveson says that the EU's new data protection regulation will require breach notifications within 72 hours of discovery.
Hewlett Packard Enterprise's Tim Grieveson says that the EU's new data protection regulation will require breach notifications within 72 hours of discovery.
After more than four years of related negotiations, the EU's General Data Protection Regulation - the Soviet-sounding "GDPR" for short - passed on April 14. The GDPR includes a number of new provisions, for example giving regulators the ability to impose a fine of up to 4 percent of a company's worldwide annual revenue, as well as instituting mandatory data breach notifications for any organization that stores or handles personally identifiable information, once they discover that they've been breached.
"The scary thing is 72 hours - we have 72 hours to actually tell the authorities there has been a breach," said Tim Grieveson, Hewlett Packard Enterprise's chief cyber and security strategist for the Europe, the Middle East and Africa regions. Other experts have told me that the 72-hour figure isn't yet set in stone, but the current focus on three days suggests that whatever the breach-notification requirement ends up being, it won't stretch to weeks.
4. Building Security Playbooks
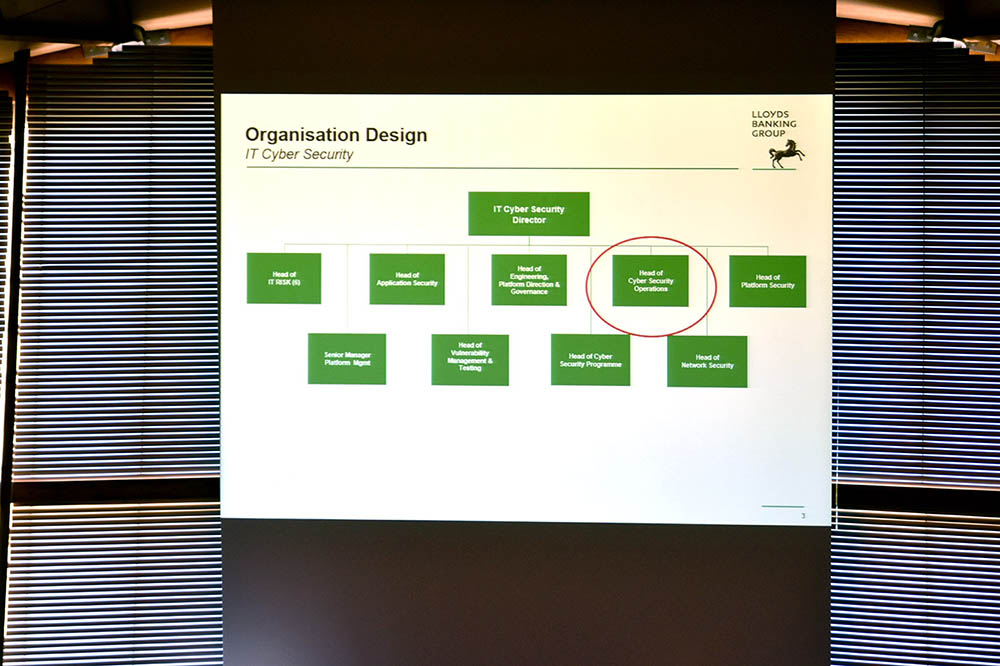 How Lloyds Banking Group organizes its security group.
How Lloyds Banking Group organizes its security group.
The day included multiple banking-related discussions. One was from Stephen Livingstone, who works with the security operations group at Lloyds Banking, which prioritizes developing security playbooks. "This is primarily because we're expecting to see high staff turnover in the next couple of years, and we want to ensure that knowledge transfer is something that happens often and easily," he said.
From a security standpoint, meanwhile, he said that one online challenge continues to be the "bring your own device" movement, because Lloyds currently has no legal resource to seize BYOD technology during the course of an internal investigation, although a fix is in the works. "We're addressing that with legal at the moment," Livingstone said.
5. Inside a Backup Botnet
 Forcepoint's Andy Settle delivers his presentation from inside the university building known as "The Egg."
Forcepoint's Andy Settle delivers his presentation from inside the university building known as "The Egg."
Andy Settle, head of special investigations for security firm Forcepoint - formerly known as Raytheon Websense - detailed a botnet campaign the company discovered, which it calls JAKU.
Settle said it's unclear who's behind the botnet, or what its purpose might be. But after launching a six-month investigation in October 2015, Forcepoint has found a number of interesting clues:
Victims: Korean language speakers are the most targeted (43 percent), followed by Japanese (30 percent) and English (13 percent). North Korea: "Tens, not hundreds, of victims" appear to travel to and from the North Korean capital of Pyongyang. Russia: Barring a few infections at a Russian ISP in Moscow, none of the botnet's victims were in Russia. Counterfeit Windows: 52 percent of victims appeared to be using a counterfeit Microsoft Windows operating system. Dwell time: The average victim PC is infected by JAKU malware for 93 days - up to a maximum of 348 days in one case - before the malware is somehow either blocked or eradicated.The takeaway from the above? "Don't jump to conclusions," Settle said. For example, the absence of Russian victims might be due to the malware selecting targets based on geography, language and timing, he said.
One possibility, Settle told me, is that whoever is behind the botnet has been keeping it in reserve for future campaigns, so that if a primary botnet gets disrupted by security researchers or law enforcement agencies, the JAKU botnet could become their primary botnet.
6. Big Data: Better Tools Required
 Steven Wilson, head of Europol's EC3
Steven Wilson, head of Europol's EC3
Steven Wilson, head of the European Cybercrime Center (EC3) at Europol - the EU's law enforcement agency - told the conference that better information sharing has been helping law enforcement agencies more quickly spot and disrupt criminal activity online.
Europol Director Rob Wainwright has been advancing the use of information-sharing platforms to connect more than 500 different law enforcement agencies from Europe - and beyond - and noted earlier this year that the amount of information being exchanged "has quadrupled in less than five years."
Because the volume of these incoming data feeds is both massive and increasing, and already reaches hundreds of terabytes per month, Wilson told the conference that Europol is increasingly looking to academia and the private sector to help it build the tools it needs to analyze all of that information. "The data feeds we're starting to get now are enormous, and to try and [tackle] them with conventional policing tactics is practically impossible," Wilson said.
7. Follow the Bitcoin Money
 Police Scotland's Eamonn Keane said criminals are increasingly operating online.
Police Scotland's Eamonn Keane said criminals are increasingly operating online.
Authorities already have some tools - developed by academics - that allow them to analyze and de-anonymize some bitcoin transactions, using, in part, data from the blockchain, which is the public ledger of all bitcoin transactions.
None of the law enforcement representatives present at the conference shared any new insights into exactly what those capabilities might be, although Police Scotland's Keane said the result of those capabilities has been well-documented, for example via the takedowns of both notorious Silk Road darknet marketplaces to date.
But criminals continue to be drawn by the relative ease and safety of operating online, Keane said, citing the following passage from a TED talk by Mikko Hypponen, chief research officer at Finnish security firm F-Secure: "It's more likely for any of us to become the victim of a crime online than here in the real world. And it's very obvious that this is only going to get worse. In the future, the majority of crime will be happening online."
Keane said: "We have a mandate to protect you in the real world; increasingly, it's moving into the online environment."
All photographs by Mathew J. Schwartz.

