Anti-Malware , Fraud , Phishing
Slew of Security Updates Also Includes Block for Rogue 911 Calls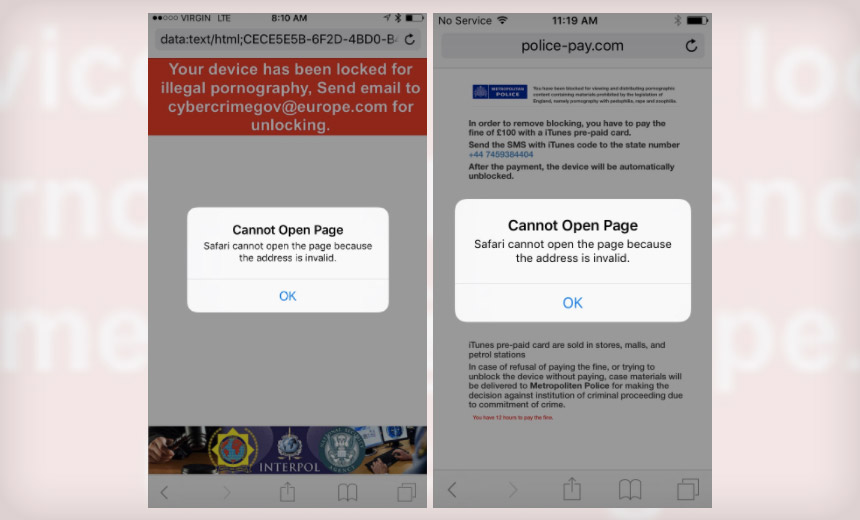 Source: Lookout
Source: LookoutA scareware gang has been seeding bogus websites with malicious JavaScript that locks Apple iOS devices and demands a ransom, payable as an iTunes gift card code.
See Also: Balancing Fraud Detection & the Consumer Banking Experience
"The group involved in this campaign has purchased a large number of domains that try to catch users that are seeking controversial content on the internet and coerce them into paying a ransom to them," Andrew Blaich and Jeremy Richards, researchers at mobile security firm Lookout, say in a blog post. The sites purport to offer everything from pornography to music downloads, they say.
But the flaw exploited in the attack is blocked in iOS 10.3, released March 27 as part of a big batch of Apple security updates for everything from macOS and iOS devices to Safari and the iWork suite.
Security experts recommend installing the updates as quickly as possible. "Exploitation of some of these vulnerabilities may allow a remote attacker to take control of an affected system," the U.S. Computer Emergency Readiness Team warns in a related security alert.
Scareware Locks iPhones, iPads
In terms of the iOS scareware campaign, the attack attempts to lock a user's browser, displaying a message such as "Your device has been locked ..." or "... you have to pay the fine of 100 pounds with an iTunes pre-paid card" message, Lookout says.
Thankfully, this attack harkens back to the early days of ransomware, in that it features a lock screen but doesn't forcibly encrypt data on the device or delete anything.
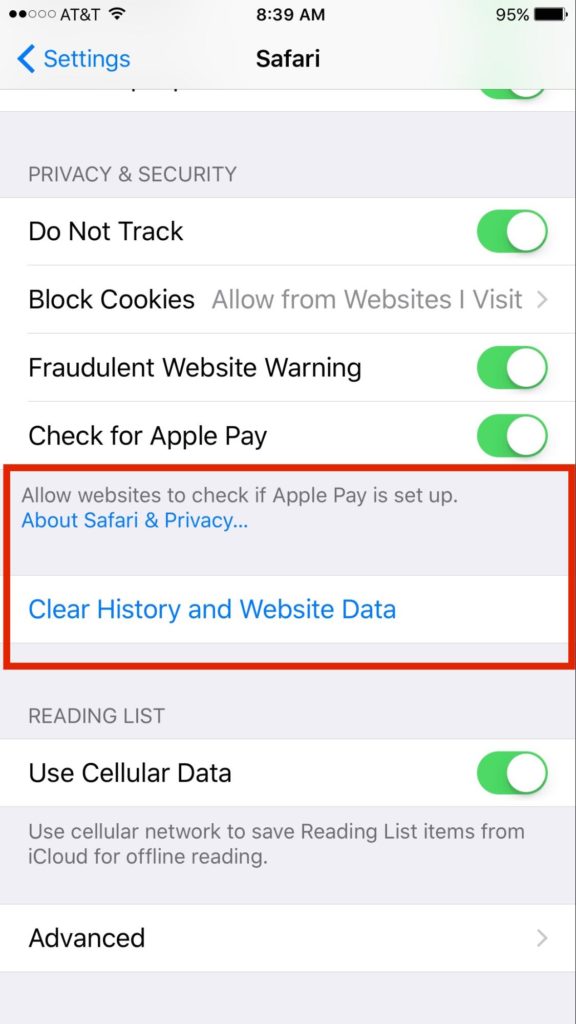 Any scareware victims not yet running iOS 10.3 can mitigate the attack by clearing their Safari cache (Settings > Safari > Clear History and Website Data). Source: Lookout
Any scareware victims not yet running iOS 10.3 can mitigate the attack by clearing their Safari cache (Settings > Safari > Clear History and Website Data). Source: Lookout"However, a knowledgeable user could restore functionality of Mobile Safari by clearing the browser's cache via the iOS settings," the Lookout researchers say, noting that they spotted related attacks in the wild in February and reported the underlying flaw to Apple. "Its purpose is to scare the victim into paying to unlock the browser before he realizes he doesn't have to pay the ransom to recover data or access the browser."
The malicious JavaScript code used in the ransomware attack was previously posted to a Russian website, according to Lookout, and appears to have been designed to target iOS 8. Researchers say attackers registered a number of bogus websites - such as pay-police.com - to try and scare victims into paying up. The attack code, meanwhile, was seeded into a variety of different types of bogus websites.
"The attack code creates a popup window, which infinitely loops until the victim pays the money," the researchers say. "The ransom is paid by sending, via SMS, an iTunes gift card code to a phone number displayed on the scam website. The pop-up window error dialog on newer versions of iOS is actually the result of Mobile Safari not being able to find a local URL lookup, so it fails, but keeps presenting the dialog message due to the infinite loop in the code."
But the pop-up window only appears to work on older versions of iOS. For more recent versions, including iOS 10.2, the attack simply creates a denial-of-service - DOS - condition in the Safari browser, meaning it can't be used.
Lookout says the attack appears to be part of a broader phishing campaign that's customized for victims based on their geography. It's published the following list of email addresses that related phishing messages have been using as their return address:
Australia: This email address is being protected from spambots. You need JavaScript enabled to view it. Ireland: This email address is being protected from spambots. You need JavaScript enabled to view it. New Zealand: This email address is being protected from spambots. You need JavaScript enabled to view it. United Kingdom: This email address is being protected from spambots. You need JavaScript enabled to view it. United States: This email address is being protected from spambots. You need JavaScript enabled to view it.Slew of Apple Security Updates
The fix for the scareware attack arrived March 27 as part of what Johannes Ullrich, dean of research for the SANS Technology Institute, calls Apple's "surprise patch days," in which the company issues a slew of fixes with no prior warning.
Various updates include the release of iOS 10.3. One of the now-patched iOS flaws, CVE-2017-2484, allowed third-party apps to initiate calls without user interaction. "This issue was addressed by prompting a user to confirm call initiation," Apple says. "Problems like this have been abused by pranksters to trick users into dialing 911 which in some cases lead to DoS attacks against 911 call centers," Ullrich says in a blog post.
Apple also released security updates via macOS Sierra 10.12.4 - that's no surprise, as much macOS and iOS code now overlaps. Updates were also issued for two prior versions of OS X - El Capitan 10.11 and Yosemite 10.10. As usual, Apple has been coy about what security fixes it's included in the updates for older operating system, saying simply: "Security Update 2017-001 is recommended for all users and improves the security of OS X."
Apple shipped additional security updates in the form of macOS Server 5.3 for macOS 10.12.4 and later, tvOS 10.2 for Apple TV 4th generation, and watchOS 3.2 for all models of Apple Watch.
Apple also pushed new versions of its iWork suite - which includes Pages, Numbers and Keynote apps - for both iOS and macOS. Also debuting is Safari 10.1, which is the latest version of its browser for both platforms. "The Safari update addresses a number of WebKit issues and various other typical browser flaws Some of the vulnerabilities can lead to arbitrary code execution," Ullrich says, noting that some of the fixes appear to relate to flaws that were used by researchers earlier this month in Trend Micro's Pwn2Own contest, held during the CanSecWest 2017 Conference in Vancouver, British Columbia.
FileVault2 Attack Blocked
One interesting macOS vulnerability addressed in the March 27 updates is CVE-2016-7585, which was discovered by security researcher Ulf Frisk. He first detailed the flaw in full in a Dec. 15, 2016 blog post, after Apple issued a related fix.
"A malicious Thunderbolt adapter may be able to recover the FileVault 2 encryption password," Apple says of the flaw. Frisk says the latest update from Apple makes "just very minor improvements" from the fix that Apple shipped in December.
As part of what he dubs the PCILeech attack, Frisk demonstrated how a Thunderbolt adapter could be modified to recover a user's encryption password for FileVault2, which is built-in macOS full-disk encryption software, in about 30 seconds. Frisk says the problem related to how EFI firmware was loaded when a macOS device first boots, saying that it allowed Thunderbolt devices to access memory.
Such vulnerabilities are not abstract concerns. The Vault 7 release of CIA attack tools by WikiLeaks, for example, revealed malware such as "DarkSeaSkies," which was designed to persist in the EFI firmware of an Apple MacBook Air (see Apple Says Latest WikiLeaks CIA Attack Tool Dump No Threat).
Frisk says anyone can test the attack on an unpatched macOS device, using a $300 Thunderbolt adapter and open source code that he published to code-sharing site GitHub. He said the password recovery attack was "tested and found to work on multiple MacBooks and MacBook Airs -all with Thunderbolt 2 ... [but] not tested on more recent macs with USB-C."
Ulf Frisk demonstrates his PCILeech attack, which used open source code and $300 in hardware to bypass FileVault2.Apple says its latest fix for the PCILeech flaw discovered by Frisk was to enable Direct Memory Access protections in the macOS EFI firmware.
Needless to say, the fix for the PCILeech flaw is one of dozens of reasons why Apple users should update their devices sooner than later. "There has been a lot of interest in exploiting Apple products," Ullrich from the SANS Institute says. "I highly recommend updating expeditiously."

