
Most enterprises, when addressing mobile security, focus on securing applications, such as the devices' operating systems, or preventing the installation of malware. But the cybersecurity experts at the National Institute of Standards and Technology say organizations should take a much broader approach to ensuring mobile security.
See Also: Hide & Sneak: Defeat Threat Actors Lurking within Your SSL Traffic
Referring to the need to address the risks posed by cellular networks and other elements of the mobile infrastructure, NIST Cybersecurity Engineer Joshua Franklin says: "There is this whole other side of a mobile device that has its own complex hardware, firmware, software and network protocols that need to be addressed." Franklin co-authored the recently released draft report, Assessing Threats to Mobile Devices & Infrastructure: the Mobile Threat Catalogue.
NIST earlier this month published the 50-page document, also known as Interagency Report 8144, that encourages organizations to take a broader approach to mobile security. NIST mobile security experts call on enterprises to adopt a new perspective on mobile security by extending their view to encompass the entire mobile security ecosystem, which includes threats that occur through cellular networks, cloud computing infrastructure and app stores.
NIST's Joshua Franklin describes the mobile security ecosystem."Often IT shops or security managers will address or secure the apps on a phone and protect the operating system from potential threats," Franklin said. "But there is a much wider range of threats that need to be addressed. For example, enterprise security teams often don't focus on the cellular radios in smartphones, which, if not secured, can allow someone to eavesdrop on your CEO's calls."
The NIST report comes as companies struggle to secure their mobile systems, according to new research from cloud and IT management services provider NetEnrich. More than 40 percent of the 150 North American IT professionals NetEnrich surveyed said their organizations suffered the loss of key corporate data from mobile devices.
"Enterprise mobile security is a moving target, for which companies and IT professionals must be adjusting constantly," says NetEnrich CEO Raju Chekuri. "A policy that works today may not work next year, let alone two to three years from now."
Mobile Ecosystem
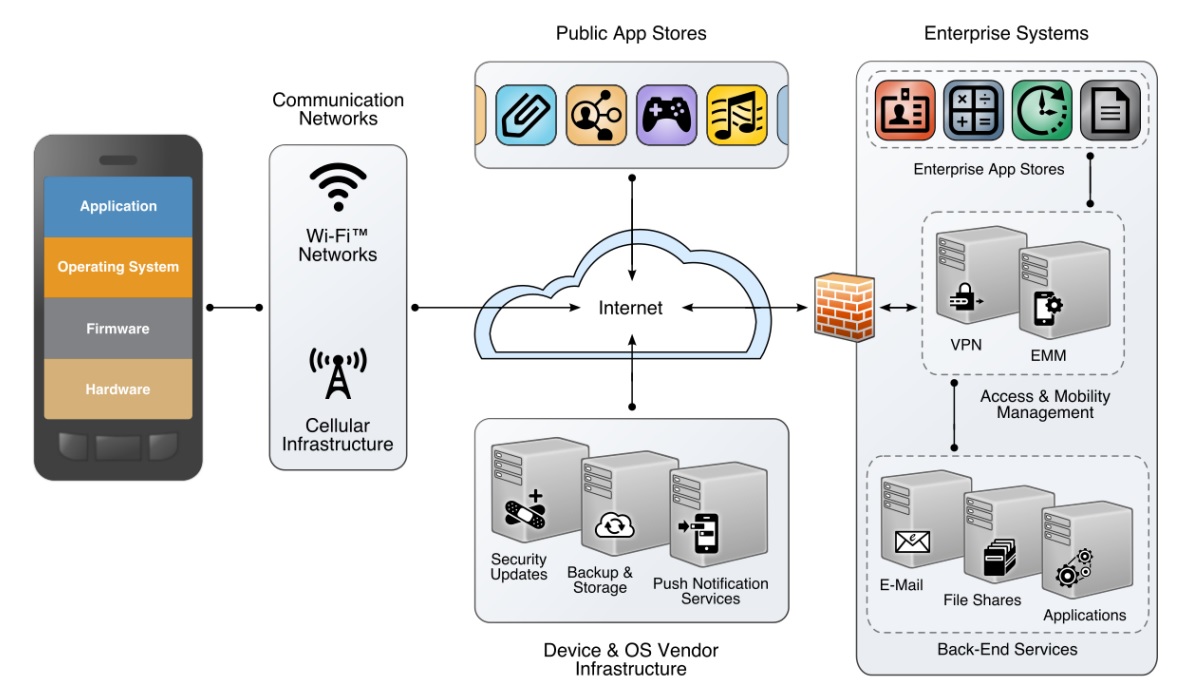 Credit: National Institute of Standards and Technology
Credit: National Institute of Standards and TechnologyThe NIST report is not guidance; there're no list of controls to be implemented or specific best practices to be adopted. Instead, NIST catalogs threats to mobile devices and associated mobile infrastructure to encourage enterprises to develop and implement mobile security best practices and solutions to better safeguard enterprise information technology.
The mobile technology catalog classifies mobile threats in numerous areas, including authentication, supply chains, physical access, ecosystem and network protocols, technologies and infrastructure. It also covers mobile security challenges involving the Global Positioning System, Wi-Fi, Bluetooth and mobile payments.
The draft document identifies known threats and furnishes available information about each one, including countermeasures to mitigate the impact of a particular threat when available.
Target Audience
The target audience for the report includes mobile security engineers and architects, who can use the recommendation to conduct informed risk assessments, build threat models, enumerate the attack surface of their mobile infrastructure and identify mitigations for their mobile deployments. Others NIST identifies as getting value from IR 8144: mobile operating system developers, device manufacturers, mobile network operators such as carriers, mobile application developers and information system security professionals who manage mobile devices in enterprises.
In addition, NIST says the report could be used when developing enterprisewide procurement and deployment strategies for mobile devices and evaluating the risks mobile devices pose to otherwise secure parts of the enterprise.
NIST is requesting feedback on the draft before it's released in final form. Send comments to This email address is being protected from spambots. You need JavaScript enabled to view it. by Oct. 12.

