
Commercial Bank of Ceylon, based in Colombo, Sri Lanka, has apparently been hacked, with its data posted online May 12 by the Bozkurtlar hacking group, which has also posted seven other data dumps from banks in the Middle East and Asia since April 26.
See Also: How to Mitigate Credential Theft by Securing Active Directory
The group, believed to have Turkish ties, released data from five South Asian banks on May 10. It also dumped data online from UAE-based InvestBank on May 7 and data from Qatar National Bank on April 26.
Commercial Bank of Ceylon did not immediately reply to Information Security Media Group's request for comment. But a researcher analyzing the data involved, who asked to remain anonymous, says that the hacked data appears to be genuine.
The files from the latest disclosure appear to contain the entire contents of the corporate website of the Commercial Bank of Ceylon, the researcher says, explaining that no customer data or payment card information was apparently exposed in the incident. The dump appears to have occurred in November of last year, which suggests the compromise took place before that, according to the researcher.
As with the other bank data compromises in the region in recent weeks, the attackers notified ISMG and others via Twitter about the file dump, which apparently was relatively quickly taken offline. Commercial Bank of Ceylon's web services at www.combank.net appear to have been taken offline briefly post the disclosure. The website was functional on May 13.
Data Dump Contents
The dump contains 158,276 files in 22,901 folders and is about 6.97 GB uncompressed. The compromised data contains annual reports, application forms, bank financial statements, .PHP files, web development backups and other files needed for the functioning of the bank's corporate front-end web infrastructure, the researcher tells ISMG.
 A sample file from the Commercial Bank of Ceylon dump
A sample file from the Commercial Bank of Ceylon dump
The attackers appear to have compromised the bank's systems using a SQL injection attack and uploading a Web Shell - a script that enables remote administration - onto the bank's PHP server, the researcher says. He bases this conclusion on the presence of artifacts from the hack in the data dump, including logs and files the indicate where the SQL injection was used and where the Shell was injected.
Bozkurtlar attackers had posted on Twitter, on a handle which has since been taken offline, that they would continue posting data from Asian and Middle Eastern banks, after the first dump of data from QNB (see: Qatar National Bank Suffers Massive Breach).
Many have been questioning the motives of the Bozkurtlar attackers, given the lack of any hacktivist message, announcement or reports of attempts at blackmail. However, analysis has revealed some common patterns and methods in the attacks, the researcher claims.
The Havij Connection
Several of the attacks appear to have involved an Iranian automated SQL injection tool called Havij 1.18 Pro, as per logs found in the leaked data, which includes the tool's payload, the researcher says. The attackers seem to have been successful in compromising Commercial Bank of Ceylon's web-facing front-end using a combination of this tool and Web Shell upload, but were unable to pivot onto the internal network as a result of relatively strong internal security controls.
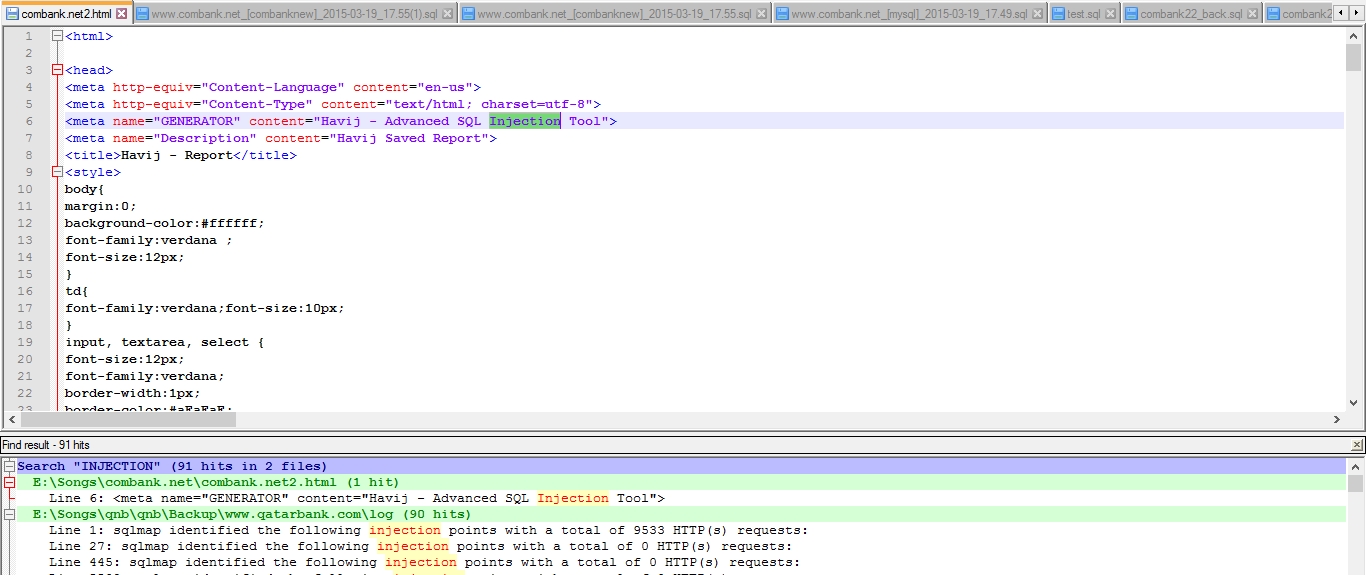 Havij log from Commercial Bank of Ceylon compromise dump
Havij log from Commercial Bank of Ceylon compromise dump
In addition to the Commercial Bank of Ceylon attack, the Havij advanced SQL injection tool was apparently used in the attacks against Kathmandu, Nepal-based Sanima Bank and Dhaka, Bangladesh-based Dutch Bangla Bank, the researcher confirms. The Qatar National Bank breach also involved an SQL injection and Web Shell combination, but it remains unclear if it involved the Havij tool (see: Dissecting a Hacktivist Attack).
The automated SQL injection tool has gained a lot of popularity with the cybercriminals and white hat researchers alike, because of the ease with which SQL injection attacks could be launched - literally at a click of a button - greatly reducing the effort and expertise required to launch such attacks.
Havij was written by Farshad Shahbazi, a security researcher at Iranian security firm the ITSecTeam, who also goes by hacker moniker r3dm0v3. The tool was released in July 2009 and the ITSecTeam started offering a free version in 2010, making the tool popular with hackers worldwide - regardless of the hat they are wearing, notes a blog on the Havij. While Havij was discontinued at the end of 2014, it is still freely available for download online.
ITSecTeam was in the news earler this year when a grand jury in New York indicted seven Iranian nationals who were allegedly working on behalf of the Iranian government - some of whom were employees of ITSecTeam - for their alleged involvement in conspiracies to conduct a coordinated campaign of distributed denial-of-service attacks against U.S. banks and others from 2011 through 2013 (see: 7 Iranians Indicted for DDoS Attacks Against U.S. Banks).

