
Britain's HSBC, which is one of the world's largest banks, is warning customers that it's been targeted by distributed denial-of-service attacks that continue to disrupt customers' access to online banking services.
See Also: 2015 Breach Preparedness and Response Study: The Results
The attacks began Jan. 29, and while HSBC reports that "we successfully defended our systems," as is common with mitigating DDoS attacks, the defenses employed have left some customers unable to access their online accounts. The bank says it's working with authorities to investigate the matter.
We continue to defend our services against todays attack. For urgent transactions please visit your local branch 1/2
HSBC notes that the attacks have not resulted in any customer details being compromised.
"HSBC Internet banking came under a denial-of-service attack this morning, which affected personal banking websites in the U.K.," a spokesman tells the BBC. "HSBC has successfully defended against the attack, and customer transactions were not affected. We are working hard to restore services, and normal service is now being resumed. We apologize for any inconvenience this incident may have caused."
The attack comes at an awkward time for banking customers on two fronts: First, it's payday for many. Perhaps more important, however, it's also just two days before the annual Jan. 31 tax payment deadline in the United Kingdom. Millions of filers face a 3 percent penalty if those taxes are not paid on time.
Threat-intelligence firm iSight Partners says that the date and time when the attacks began are significant. "We believe that an actor of unknown motivation chose this time to conduct a DoS attack against HSBC because a DoS attack performed at a time of peak traffic levels would need potentially much less strength to cause a disruption than if it were conducted at a time of lower traffic volume," the firm says in a research note.
HSBC is working closely with law enforcement authorities to pursue the criminals responsible for today's attack on our internet banking.
HSBC didn't immediately respond to a query about whether its DDoS disruptions had been preceded by a ransom demand, which law enforcement agencies it's working with or whether any particular group or individual has claimed responsibility for the DDoS attacks.
Hacktivism Is Out, Extortion Is In
Back in 2013 and 2013, a major DDoS campaign by the self-proclaimed hacktivist group Izz ad-Din al-Qassam Cyber Fighters primarily targeted U.S. banks with DDoS disruptions. The group claimed that its attacks would continue until an anti-Muslim video was removed from YouTube. Many U.S. officials, speaking off the record, contended that the Iranian government was behind the attacks.
Since then, banks have continued to face DDoS disruptions, although more recently many have been tied to extortion attempts (see Cyber Extortion: Fighting DDoS Attacks).
DDoS mitigation provider Arbor Networks, in a new report, says that about one-third of DDoS disruptions now appear to have an extortion component.
"Historically, ideological hacktivism has commonly been the top motivation, only displaced last year by nihilism/vandalism," according to Arbor's report. Now, however, the top perceived motivation behind attacks is "criminals demonstrating attack capabilities," followed by attacks designed to compromise gaming services and extortion (see Lizard Squad DDoS Attack Targets U.K. National Crime Agency).
The most infamous DDoS extortion rackets today are the Armada Collective and a group calling itself DD4BC, for "DDoS for Bitcoin." Police in Bosnia and Herzegovina last month arrested a "main target" as well as another suspect as part of the anti-DD4BC Operation Pleiades, which is ongoing. But EU law enforcement officials have declined to comment on any other suspected DD4BC members they might be pursuing or where they're located (see Europol Announces DD4BC Arrests).
Botnet-Driven DDoS Malware Trends
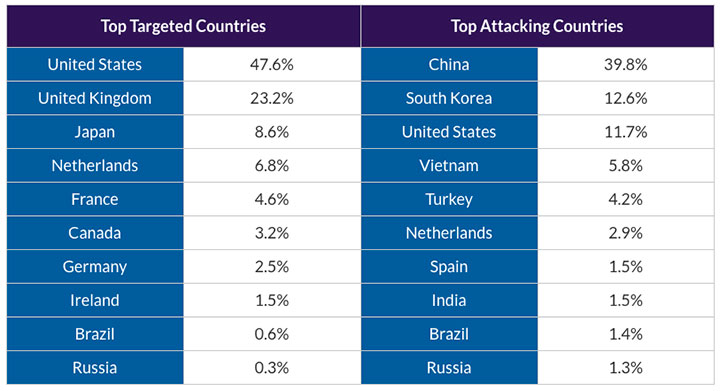 Botnet-driven DDoS attack trends from Oct. to Dec. 2015. (Source: Imperva)
Botnet-driven DDoS attack trends from Oct. to Dec. 2015. (Source: Imperva)The HSBC website disruption also comes as DDoS defense firm Imperva warns that botnet-driven DDoS attacks against sites in the United Kingdom have recently spiked, based on a review of attack patterns for the final three months of 2015. DDoS malware infects victims' PCs, turning them into remotely controllable attack nodes. Criminal organizations can use the malware to attack targets of their choosing, or wage attacks on behalf of paying clients as part of the so-called cybercrime-as-a-service ecosystem (see How Do We Catch Cybercrime Kingpins?).
While U.S.-based sites continued to be the most targeted, attacks against both U.K. and Japanese sites have increased sharply, according to Imperva researchers. In particular, the percentage of all botnet attacks that targeted U.K.-based sites rose from 3 percent in the third quarter of the year to 23 percent in the fourth quarter, they say. During the same timeframe, the number of botnet-driven DDoS attacks against Japanese sites rose from 1 percent to 9 percent.
In terms of origin, 40 percent of botnet-driven DDoS attacks now emanate from China, followed by 13 percent from South Korea and 12 percent from the United States, according to Imperva. It also notes that the most prevalent DDoS malware strains at the end of 2015 were Nitol and PCRat, each of which were used in about one-third of all such attacks.

