Anti-Malware , Risk Management , Technology
Authorities Sinkhole Malicious Infrastructure, But Will Disruption Hold?
One of the world's most prevalent malware families - Dorkbot - and its associated botnets have been disrupted by an international coalition of law enforcement agencies in cooperation with technology and security firms.
Once it infects a PC, attackers can instruct the malware to install additional malicious code, launch distributed denial-of-service attacks, steal online account credentials as well as send spam, authorities say.
"Botnets like Dorkbot have victimized users worldwide, which is why a global law enforcement team approach working with the private sector is so important," says Wil van Gemert, deputy director of operations at the association of European police agencies known as Europol, which participated in the takedown.
Authorities say that in the past year alone, the credential-stealing malware has been tied to infections of more than 1 million PCs across 190 different countries. But while the current command-and-control channels tied to the malware have been "sinkholed" - forcibly redirected to servers controlled by authorities - beginning Dec. 3, it's not clear whether that disruption will hold, should the malware's developer release an updated version tied to new C&C servers. Authorities have previously sinkholed related domains, but the malware has continued to reemerge.
Dorkbot, which uses Internet Relay Chat in part for C&C purposes, first appeared in 2011. It's sold on cybercrime forums as a crimeware toolkit called "NgrBot," which includes bot-building kits as well as extensive documentation, according to a blog post from Microsoft, which says it assisted with this Dorkbot disruption by contributing related intelligence (see Why Cybercrime Now Exceeds Conventional Crime).
The latest Dorkbot takedown was coordinated by law enforcement agencies across multiple countries, including the U.S. FBI and Department of Homeland Security's Computer Emergency Readiness Team, the Royal Canadian Mounted Police, as well as Interpol and its EU counterpart Europol. Confusingly, the DDoS botnet shares its name with the unrelated annual London Dorkbot event launched in 2001, which is dedicated to "people doing strange things with electricity."
Europol works with international partners to target Dorkbot Botnet https://t.co/4F6jGqG9OL @EC3Europol @FBI @DHSgov & more
"Dorkbot has been active for a number of years, with its activity largely facilitated by the ease in which bots are created through the availability of online kits allowing anyone to build their own bot," says Raj Samani, CTO for Europe, the Middle East and Africa at security firm Intel Security, and a cybersecurity adviser to Europol. "It is hugely encouraging to see the trend of collaboration within the security industry continue, which bodes well for the safety of our data in this digital age."
The takedown follows multiple related disruption efforts launched by Poland's computer emergency response team, CERT Polska, which sinkholed the malware C&C channels in 2012 after Dorkbot began spreading between Polish users of Skype. In 2013, the agency also seized 641 domains that had been registered using "rogue registrar" Domain Silver, of which 179 domains had been tied to C&C activity for malware and ransomware, including Andromeda, Citadel, ZeuS and Dorkbot.
Dorkbot Targets Credentials
Authorities say Dorkbot is designed to steal passwords for online accounts, including such social networks as Facebook and Twitter, as well as to install additional malware that can turn infected endpoints into nodes in a DDoS attack or part of a spam relay.
"Dorkbot-infected systems are used by cybercriminals to steal sensitive information - such as user account credentials, launch denial-of-service attacks, disable security protection and distribute several malware variants to victims' computers," US-CERT says in a related alert. "Dorkbot is commonly spread via malicious links sent through social networks, instant message programs or through infected USB devices."
The malware can also be spread by criminals installing a Dorkbot crimeware toolkit onto hacked - but otherwise legitimate - websites and launching drive-by attacks against all browsers that visit the site, security experts say. "Dorkbot has been around in different forms for several years now and is still very prevalent," says Jean-Ian Boutin, a Canadian malware researcher with security firm ESET, which participated in the takedown, in a blog post. Back in 2011, for example, ESET researchers found that 80,000 infected PCs in Latin America alone were part of just a single instance of the botnet.
Hardest Hit: India
In the past 12 months, however, Microsoft says it's seen an average of 100,000 PCs per month getting infected by Dorkbot. Over the past six months, the country with the greatest number of infected PCs has been India, followed by Indonesia, Russia, Argentina and Malaysia.
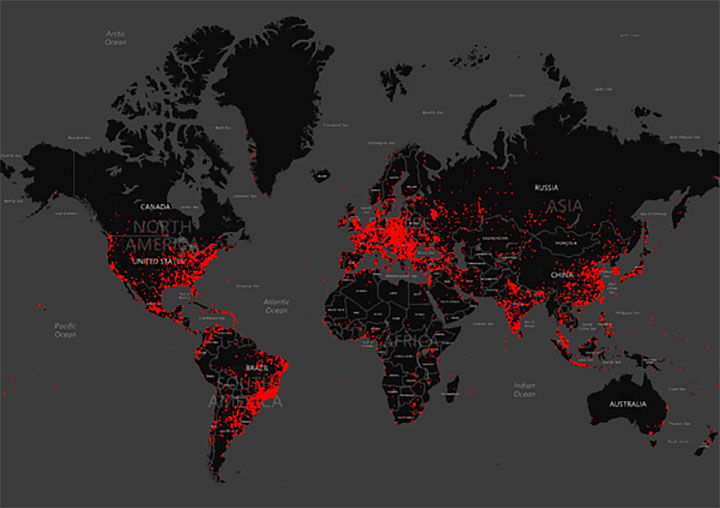
A heat map of Dorkbot infections seen over the past 12 months. Source: Microsoft.
Security experts say Dorkbot is often used as the first stage of an attack by criminals. After infecting a PC, the software downloads the full Dorkbot module from a hardcoded C&C server, attempts to disable security software running on the endpoint and then "phones home" to an IRC server for instructions, ESET's Boutin says. After that, it often loads such malicious code as "Kasidet - malware used to conduct DDoS attacks also known as Neutrino bot - and Lethic, a well-known spambot."
"The main danger related to the botnet, as we see it, lies in it acting as a dropper for other threats," CERT Polska says in a blog post. "This is a common business model and similar to other threats we have neutralized, for example a very large Polish-authored botnet called Virut."
Microsoft says it sees Dorkbot being used by at least several different criminal enterprises, one of which employs a version of the malware that's customized to search for and subvert any older versions of the malware that it finds already infecting a PC. "The operator appears to be abusing the older IRC-based Dorkbot variant by disabling the self-check routine, changing IRC commands and using the loader to force it to connect to the operator's own C&C server," it says.
Total Infection Rate Unknown
Authorities say it's impossible to know just how prevalent related malware infections might be. "Estimating the true scale of the infection will be possible only after collecting data from sinkholes," CERT Polska says.
For detecting and removing Dorkbot, CERT Polska is directing users to either the Microsoft Malicious Software Removal Tool or ESET's Dorkbot Cleaner tool, both of which are free.

